Photo Gallery
 |
SpyCloud Compass Solution

Additional Info
| Company | SpyCloud |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://spycloud.com/ |
NOMINATION HIGHLIGHTS
The growth of cybercrime has seen criminals develop new and cunning tactics to access organizations’ data. Traditional threat intelligence solutions provide enterprises with perspective on the threat landscape but don’t supply detailed information on the exact information criminals have and are using to target businesses. This lack of perspective leads to vulnerability to cyberattacks, from account takeover and session hijacking to ransomware. To protect businesses, employees and customers, security teams need proactive, automated solutions that detect and address security gaps by remediating the exposed data that fuels cybercrime.
SpyCloud, the leader in Cybercrime Analytics (C2A), is disrupting the criminal underground and helping organizations strengthen defenses by increasing visibility into the extent of compromised data on corporate systems. By continuously ingesting and analyzing recaptured darknet data, SpyCloud transforms billions of assets from third-party breaches and malware-infected devices into actionable insights per customer needs: APIs integrated into login workflows, software enabling automatic resets of exposed Active Directory credentials, integrations into common SOARs to respond to malware infections on employees’ managed and unmanaged devices, and more.
Additionally, SpyCloud’s Compass solution allows organizations to detect and respond to data siphoned by infostealer malware. In 2023, 61% of breaches were malware-related, exposing over 343.78 million stolen assets. Compass – powered by SpyCloud’s repository of over 560+ billion recaptured assets – enables comprehensive remediation of malware-infected devices through a series of steps that augment existing incident response playbooks, enabling action even if the device is unmanaged and falls outside of corporate oversight. This SpyCloud-pioneered approach is called Post-Infection Remediation (PIR) and is designed to effectively remediate infostealer-affected devices, users, and applications, including third-party applications users rely on daily from SSO instances, sales and marketing databases, financial systems, and code repositories.
Key Capabilities / Features
Compass helps organizations proactively prevent ransomware by identifying definitive evidence of malware-infected devices, along with exposed users and applications that cybercriminals use to walk right into networks. As a result, organizations fill the gaps in its malware protection framework to detect and respond to high-priority threats.
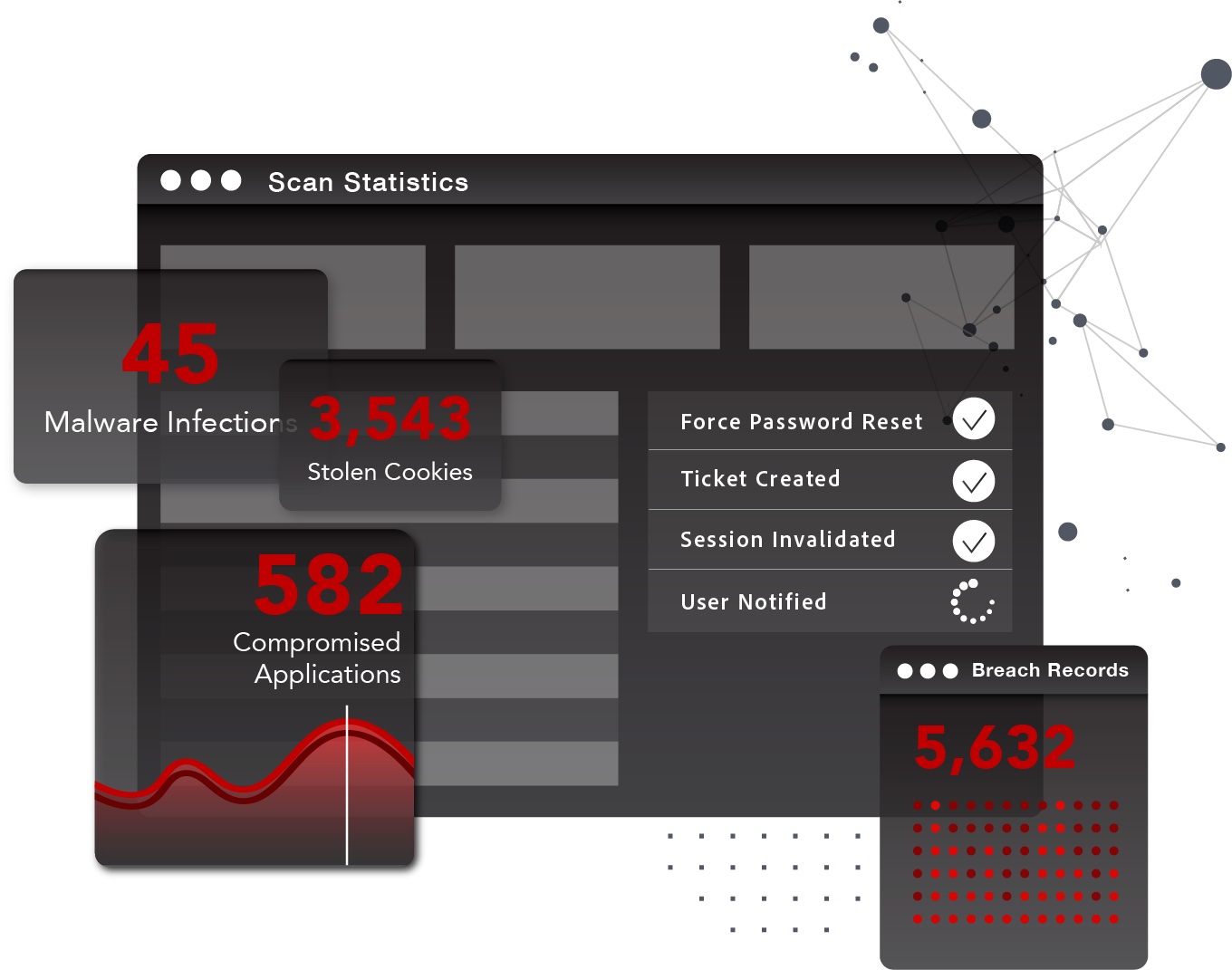
In addition, Compass identifies infected devices and applications connected to an organization by monitoring malware records for the target domains and third-party subdomains an organization chooses. Once it identifies what has been exfiltrated by the infection, such as credentials and session cookies for critical business applications, security teams can understand the scope of the threat at-a-glance.
From there, Compass provides detailed information on each exposure to shortcut the investigation steps and enables teams to quickly implement Post-Infection Remediation (PIR). With insights such as malware type, user details, time, application and more, organizations can streamline the recovery process with PIR.
Other capabilities include:
Exposed Application View: view all third-party applications that were exposed by each infostealer, including shadow IT apps accessed with either personal or corporate email address
Managed Devices and BYOD: pinpoint the exact malware-infected managed or unmanaged device that was used to access corporate applications
High Fidelity Alerts: get definitive evidence that stolen data tied to your enterprise is in criminal hands, with alerts of new exposures
Interactive Graphs: visualize the scope of a potential threat, including infected devices, users, and applications with actionable details
Intuitive Portal: see thorough details of each infection, along with powerful visualizations that illuminate your remediation action plan
Stolen Cookies: view the count and name of stolen cookies associated with your monitored subdomain for the affected applications
How we are different
Illuminated Attack Surface: To eliminate the many questions that follow a cyber incident, SpyCloud developed Compass to provide organizations with a complete picture of infiltration details to map the connections between applications, machines and users, enabling quicker PIR. These details include malware type, infection path, source, device name, date and time of infection, application name, and more. In addition, SpyCloud customers can identify previously unseen compromised assets, including credentials and cookies for third-party applications, to analyze the relationships between assets and prioritize response activity accordingly.
Full Remediation: Compass helps organizations proactively prevent ransomware by identifying evidence of malware-infected devices instead of waiting to act after a cybercriminal has stolen data. Once the exposed device or user has been identified, security teams can quickly respond to high-priority threats with PIR, as Compass provides security teams with the exact information cybercriminals have stolen. With PIR, organizations can remediate all employee devices, whether managed or unmanaged, significantly reducing the window of enterprise vulnerability.
Automated Recovery: Compass provides organizations with definitive evidence of entry points, allowing them to quickly reset credentials and invalidate session cookies using PIR. By acting swiftly, this automated recovery process significantly reduces organizations’ exposure to full-blown security threats and reduces alert fatigue by providing detailed information on each exposure – SpyCloud stands alone in the capability to support PIR.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



