Photo Gallery
 |
 |
SpyCloud Identity and Access Management

Additional Info
| Company | SpyCloud |
| Company size | 50 - 99 employees |
| Website | http://www.spycloud.com |
NOMINATION HIGHLIGHTS
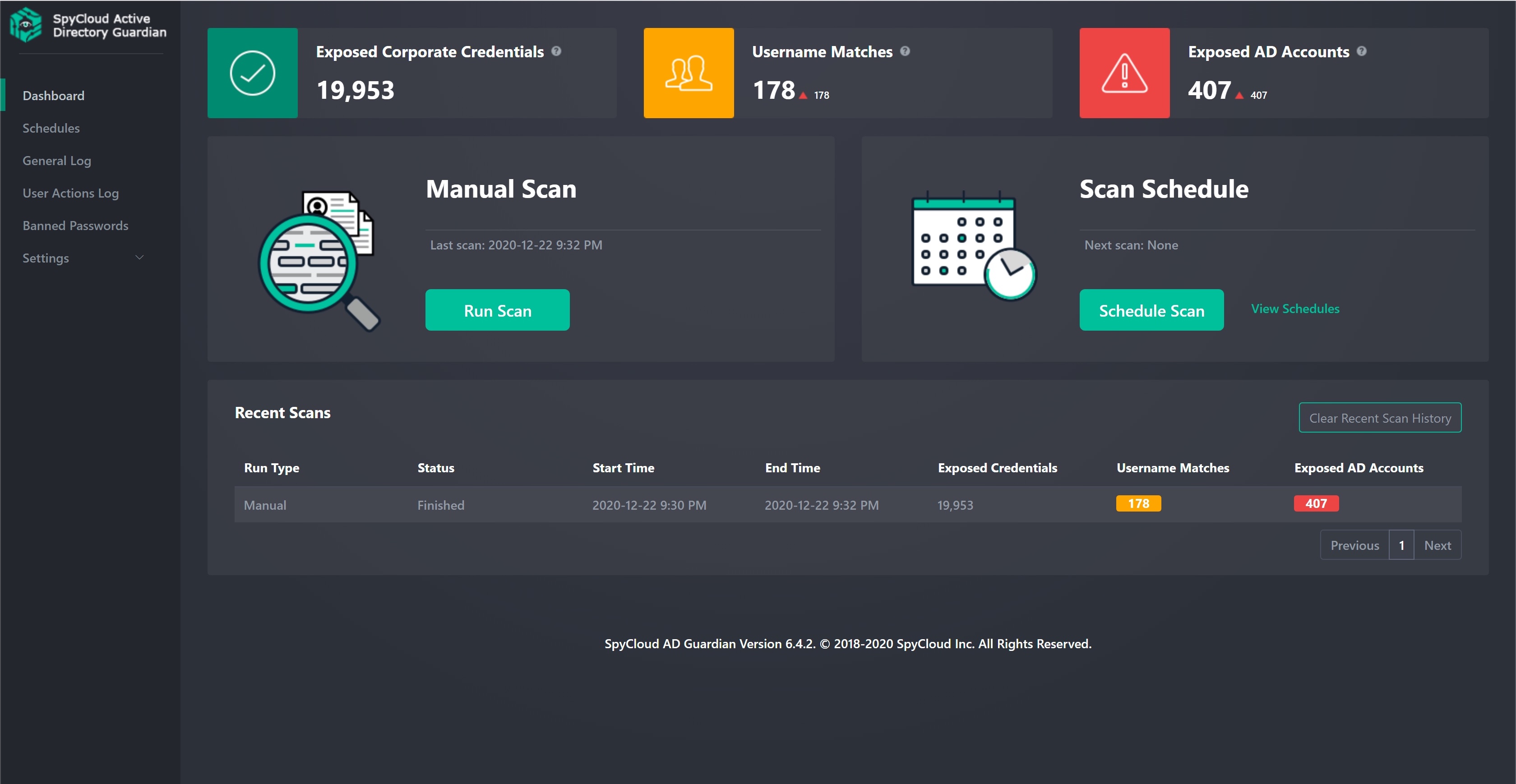
As strict as an organization’s IAM policies might be, they are only as secure as the user’s identity. If the user’s credentials are compromised, the wrong person can pose as them and access everything they can. SpyCloud is a key component of enterprise IAM/CIAM programs, ensuring that users logging in – whether employees, consumers, or suppliers – are who they say they are, and not bad actors leveraging stolen credentials. This happens by matching login credentials against SpyCloud’s massive breach data collection. If the login can’t be trusted, meaning the password is tied to a data breach and considered compromised, further steps can be taken to corroborate that the user is genuine without introducing unnecessary friction (i.e. step-up authentication), or the user can simply be forced to reset their password. SpyCloud is unique in that it can also run password-only checks and flag passwords that have ever been compromised in a data breach, regardless of whether it is tied to a given email address or username.
Threat actors use phishing attacks, social engineering and reused credentials to access business accounts and bypass traditional IAM safeguards. They target executives and privileged users who are likely to have access to valuable, sensitive parts of the network. SpyCloud recently launched VIP Guardian, a solution that enables businesses to extend password exposure alerts to the personal accounts of executives, board members, and employees with privileged access, empowering them to secure compromised personal credentials that could provide entry points to corporate resources. This is done without sacrificing the users’ privacy; their personal logins aren’t visible to employers. A compromised password on a tax prep, fitness, or online banking account reused in a corporate setting could provide a stepping stone to corporate resources. SpyCloud VIP Guardian enables companies to reduce these security blindspots.
How we are different
Password-only checks: If a user’s password appears in the SpyCloud database, it means that password is available to cybercriminals. Whether your user has recycled credentials across multiple accounts or chosen an easy-to-guess password, their account is at risk of account takeover. SpyCloud helps identify and prevent risky password choices by checking passwords against its repository of stolen credentials, so you can tell how many times a password has ever appeared in a breach—whether or not a specific user was involved.
Earliest possible data recovery: SpyCloud is different from other IAM solutions due to the strength of the database against which logins are verified. It does not rely solely on collecting breach data from dark web markets and pastebin sites. By the time stolen data is “leaked” to the dark web, it may be 18+ months after the breach. Companies may not be aware they have been breached, and therefore employees and consumers continue using compromised passwords, which, due to the prevalence of password reuse, could put other accounts at risk. In order to quickly notify users that their login data and/or PII is in criminal hands, SpyCloud’s research team infiltrates cybercriminal communities and socially engineers breached data sets directly from bad actors within days or weeks of the breach, enabling the fastest notification of exposed credentials available. Consumer data monitoring services take an average of nine months longer to notify their customers. This speed of collection (and therefore the speed with which logins can be checked for compromise) drastically decreases an enterprise’s threat exposure window.
Multiple methods for interacting with SpyCloud data: Login checks and automatic remediation of compromised accounts are handled through integration with Microsoft Active Directory, and APIs enable rapid integration of SpyCloud data into other existing employee and consumer login workflows, SIEMs, and Threat Intelligence Platforms.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



