Stealthbits Credential and Data Security Assessment
Recognized in the Category:
Photo Gallery
|


|
Stealthbits Credential and Data Security Assessment

Additional Info
| Company | Stealthbits |
| Company size | 100 - 499 employees |
| Website | http://www.stealthbits.com |
NOMINATION HIGHLIGHTS
The Credential and Data Security Assessment (CDSA) is a full assessment and calculation of risk across some of the most critical and often misunderstood areas of an organization’s environment (whether completely on-premises, in the cloud, or operating in hybrid mode), including File Systems, SharePoint, Exchange, Office 365, AWS S3, Box, Dropbox, Microsoft SQL Server, Azure SQL, and Oracle Databases, Active Directory, Azure Active Directory, and Windows Desktop and Server infrastructure.
The CDSA focuses on three areas:
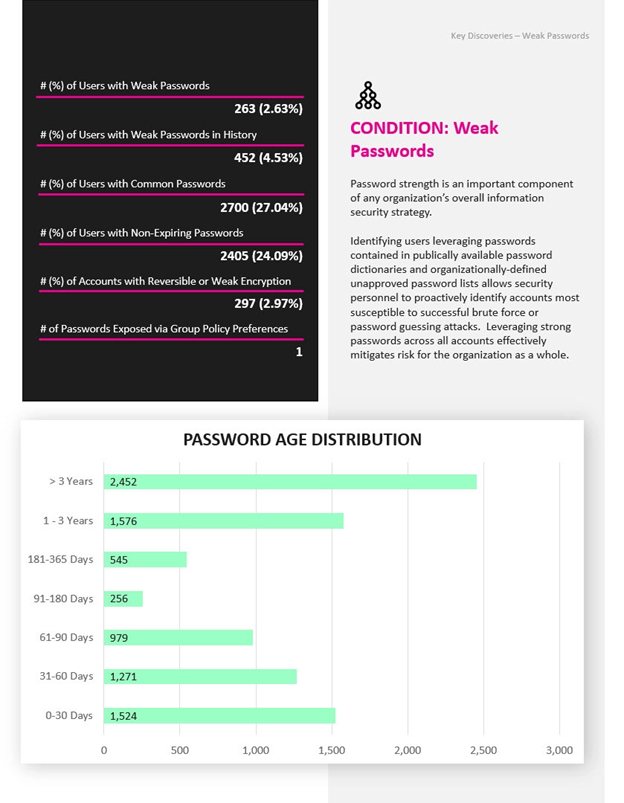
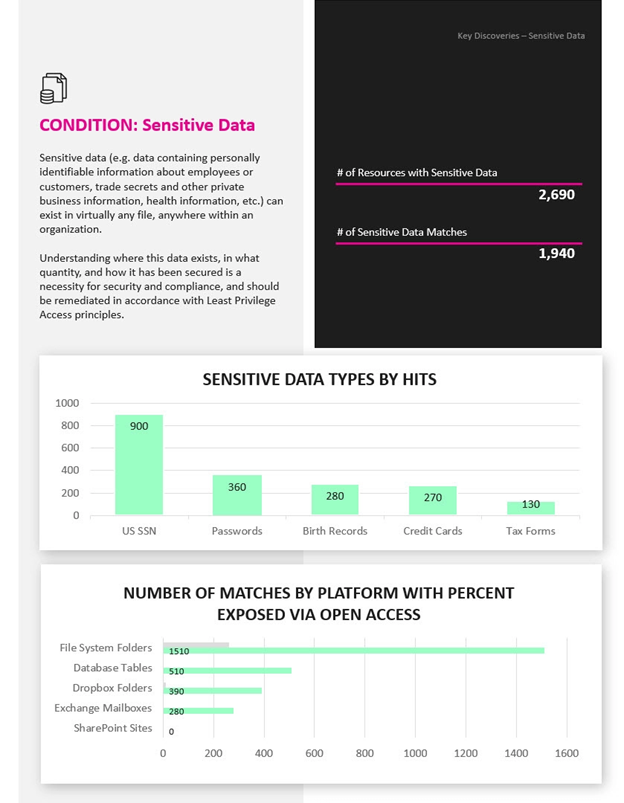
• Data – Discover sensitive data, open access rights, high-risk permissions, and stale data that is putting the organization at risk.
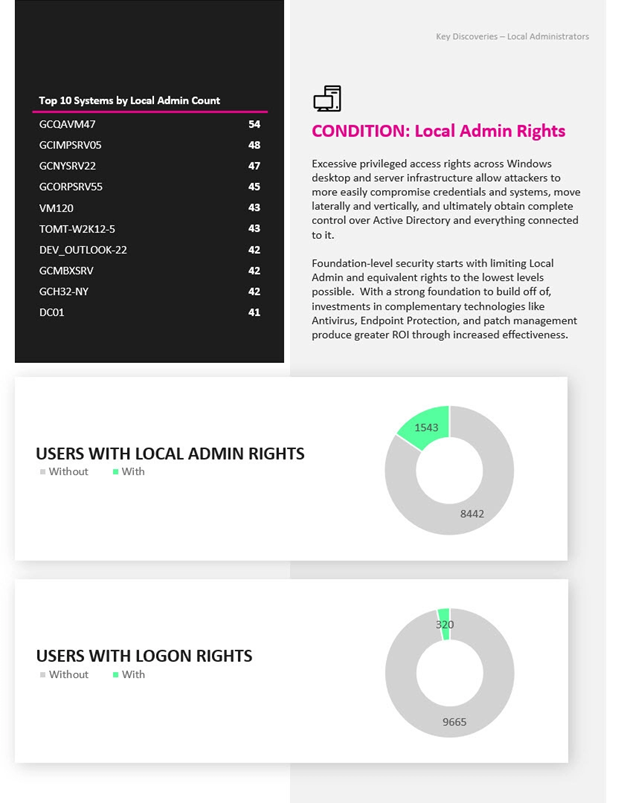
• Credentials – Pinpoint vulnerabilities in Active Directory permissions, account passwords, privileged access rights, configurations, objects, and more.
• Systems – Identify privileged access rights, service accounts, critical misconfigurations and conditions attackers exploit to steal credentials.
How we are different
Stealthbits’ Credential and Data Security Assessment differs from its competitors in several ways:
• Comprehensive visibility - with 100+ security checks in total, the CDSA identifies critical security conditions and misconfigurations across an organization’s on-premises and cloud-based data repositories, Active Directory, and Windows infrastructure. Other assessments often focus only on one aspect such as the data and ignore the issues of credentials and systems.
• Fast, no-impact scanning - With no agents to deploy and the ability to run from an existing system located anywhere in your environment, you’ll get all the data you need without making changes to your infrastructure or incurring additional costs. Other assessments often affect performance, take a lengthy time period to complete.
• Valuable output - A detailed Executive Summary highlights where attention is needed most and why, allowing any audience to fully understand the nature of the risks identified and why they’re important to remediate. Other assessments often have outputs that may be understood by someone with a deep technical understanding but fail to be absorbed by a higher level audience.
The bottom line is most other assessments only focus on one aspect such as the data, but not look at the credentials or systems. To put this in perspective, it’d be like hiring someone to do an assessment on how secure your family home is by only assessing the strength of your front door lock but completely ignoring the fact that the giant window next to your door is actually broken and wide open.


