Photo Gallery
 |
 |
StealthINTERCEPT

Additional Info
| Company | STEALTHbits |
| Company size | 100 - 499 employees |
| Website | http://www.stealthbits.com |
NOMINATION HIGHLIGHTS
As cyber-attacks become more sophisticated, organizations must monitor their IT environments for changes and activities that violate security policies. Native logs, however, do not provide the real-time intelligence needed to identify and block threats.
StealthINTERCEPT addresses this gap. By inspecting all Active Directory, Exchange, and File System traffic at the source, it detects malicious and unintended changes in real-time to safeguard organizations’ credentials and unstructured data. Without reliance on native logging, StealthINTERCEPT is able to identify authentication-based and file system attacks, monitor usage and abuse of privileged accounts, and detect changes in ways organizations have not been able to previously. Furthermore, StealthINTERCEPT can instantiate preventative controls to lock down critical assets and enforce security policies.
Features
• Real-time Monitoring—intercept Active Directory, Exchange, and File System traffic in real-time to give organizations faster, broader insight
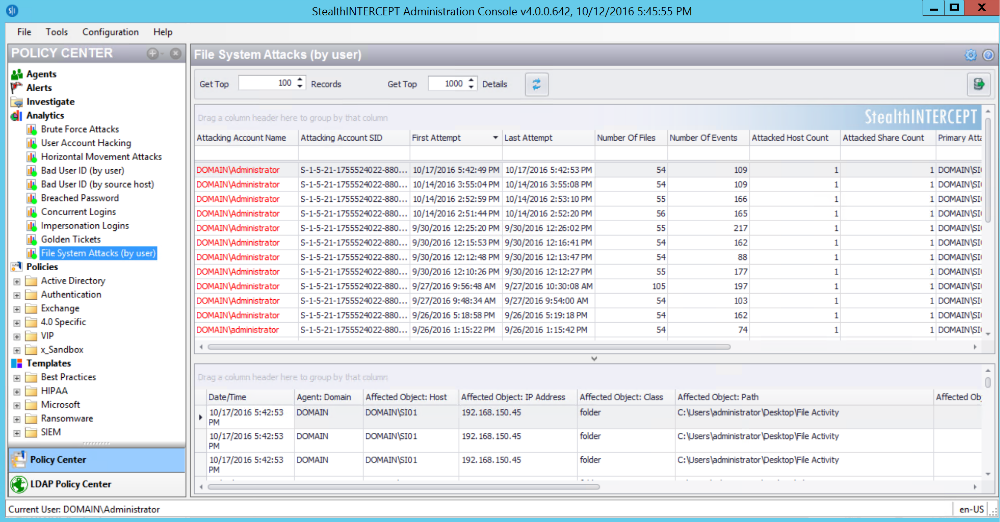
• Authentication and File System Attack Analytics—identify and block threats and privileged account abuse with pattern- and behavior-based detection techniques
• Change & Access Detection and Prevention—detect and prevent access and changes to privileged accounts, security groups and GPOs, file/folder permissions, and mailboxes
• Powerful Investigations—provide visibility into the who, what, where, and when of an event, including before/after values, origination/destination IP, host names, etc.
• Real-time Alerting—receive real-time alerts on changes and threats at global or policy-specific levels
• Dynamic Policies—enrich policies by connecting data from DLP, PIM, and other systems
• Out-of-the-Box SIEM Integration—send only relevant threats to SIEM for fast remediation
Benefits
• Enhanced Security and Policy Enforcement—identify and remediate security threats and prevent high-risk changes and activities (e.g. modifying GPOs)
• Improved Auditing and Compliance—track who is doing what with event context and reports to document activity and compliance
• Increased Value of Technology Investments—integrate with SIEM for greater insight, reduced risk, and decreased cost due to eliminating native logs
How we are different
• Real-time Threat Protection – StealthINTERCEPT focuses on the two common denominators in every data breach scenario: credentials and data. The vast majority of credentials are contained in Active Directory. The vast majority of data is contained in unstructured data repositories like file systems. Regardless of where an attack originates, internally or externally, attackers use similar tactics to compromise assets. They perform reconnaissance to find critical resources, probe those resources to locate credentials, escalate their privileges through lateral movement, and ultimately compromise and exfiltrate data. StealthINTERCEPT is designed to detect these behaviors in real-time, block them, and instantiate preventative controls that make these attacks impossible in the future.
• Award-Winning SIEM Integration – StealthINTERCEPT won the 2015 IBM Beacon Award for Outstanding Security Solution. The solution was recognized by IBM for being an “exceptional solution to drive business value and transform the way their clients and industries do business in the future.” STEALTHbits continued innovating by being early adopters of IBM’s X-Force Exchange with two StealthINTERCEPT dashboards. The solution not only has award-winning integration with IBM’s QRadar SIEM solution but also with all major SIEM platforms, allowing customers to derive greater value from their existing technology investments.
• Loyal Customer Advocates – STEALTHbits’ commitment to customer satisfaction has yielded impressive results. We have a 92% customer retention rate, with a diverse client base that includes 5 of the 6 largest financial institutions and 40% of the Fortune 100. Many of our customers have been with us for nearly a decade, with 80% of them buying additional STEALTHbits solutions. Our dedication has resulted in sustained growth and profitability for over 14 years, with 30% year-over-year growth in recent years.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



