Photo Gallery
|


|
Strobes CTEM


Additional Info
| Company | Strobes Security |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://strobes.co/ |
NOMINATION HIGHLIGHTS
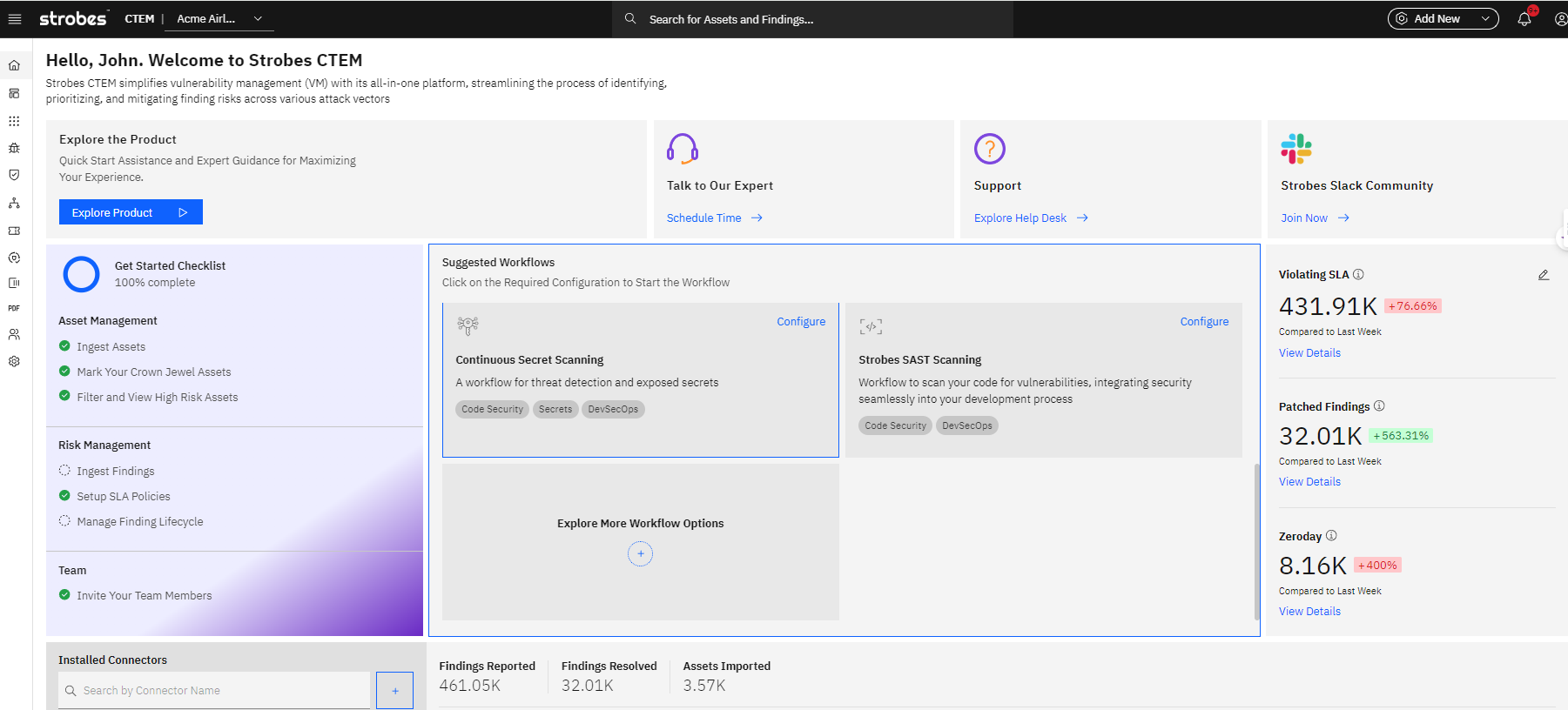
Strobes CTEM empowers your organization with a comprehensive suite of cybersecurity tools, designed for a complete threat exposure management journey. This means you get everything you need, from the initial discovery of your assets to ongoing vulnerability assessments and penetration testing – all in a single, unified platform.
Strobes CTEM goes beyond traditional security solutions. As one of the world’s first platforms specifically designed for continuous threat exposure management, we provide cutting-edge tools and methodologies to proactively address the cyberthreats.
With Strobes CTEM, you gain:
Attack Surface Management: Continuously map your organization’s external facing assets, ensuring a complete picture of your potential attack points.
Vulnerability Management: Identify and prioritize vulnerabilities in your systems, allowing you to focus on the most critical risks.
Penetration Testing as a Service: Simulate real-world attacks to uncover weaknesses before cybercriminals do.
Streamlined Compliance: Simplify meeting industry standards and regulations with easy-to-use reporting tools.
Strobes CTEM is more than just a combination of solutions – it’s a journey towards a more secure future.
Key Capabilities / Features
Key Features / Capabilities
Asset Discovery & Management
Rapidly identify and catalog every digital asset across your enterprise, ensuring comprehensive oversight and a complete security view.
- Discover assets at scale
- Identify high-risk assets
- Integrate with CMDB & cloud providers
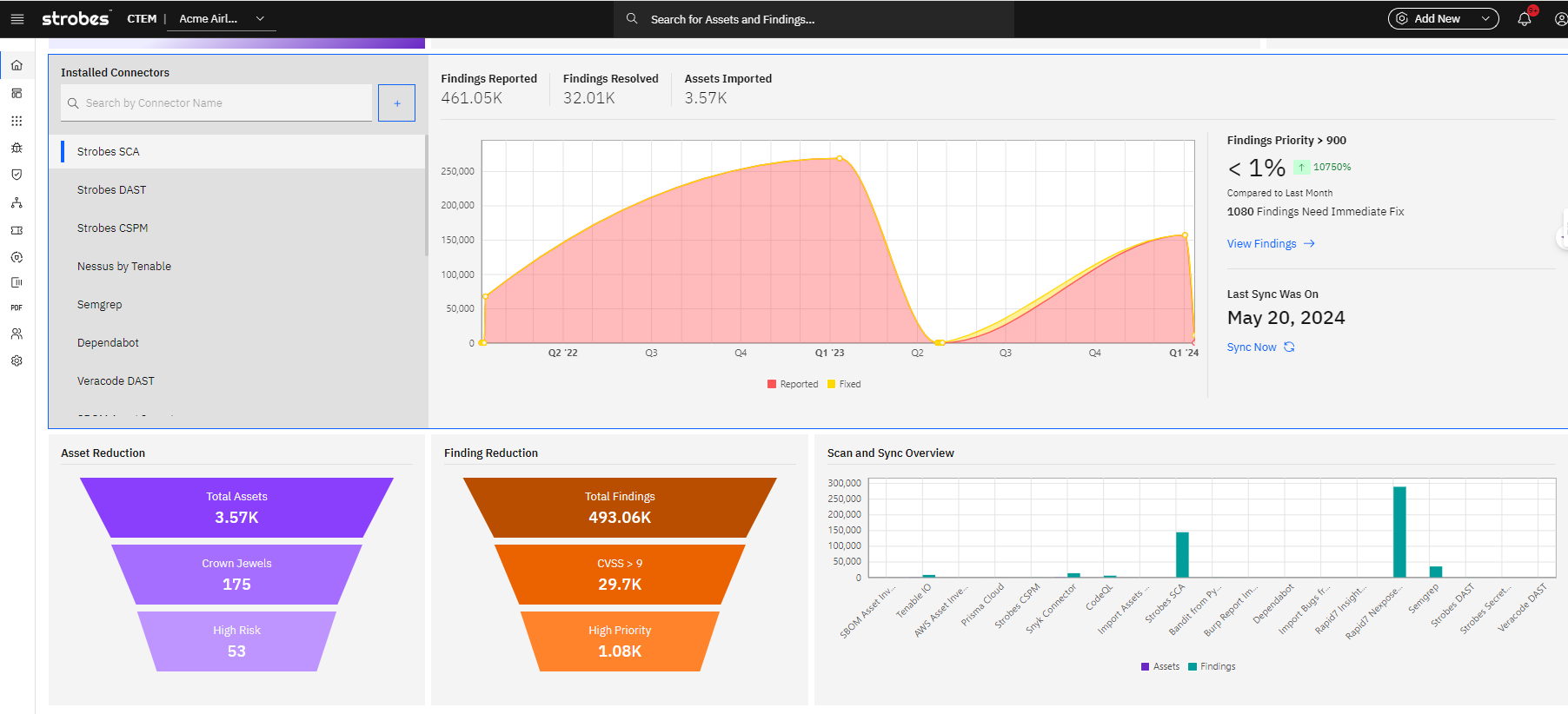
Vulnerability Scanning & Management
Centralize vulnerability data, streamlining the review and mitigation processes, and fostering swift decision-making.
- Scan for misconfigurations & vulnerabilities
- Aggregate all vulnerabilities in one place
- Advanced filters to speed up VM process by 10x
Risk-Based Prioritization
Leverage the platform's scoring system to make informed decisions about which vulnerabilities to address first, based on potential impact and available resources.
- Set up SLA policies
- Build custom workflows
- Integrate with Slack, MS Teams, Email, and much more
Integrations
Enhance your security landscape by seamlessly connecting with 120 + leading connectors, ensuring 360-degree vulnerability aggregation.
- Run open-source scanners
- Integrate with commercial vulnerability scanners
- Send vulnerabilities to Jira & ServiceNow
Analytics & Dashboards
Leverage a comprehensive library of templates to generate reports and visualizations, simplifying data presentation and enhancing understanding.
How we are different
Strobes CTEM offers a revolutionary approach to cybersecurity, setting itself apart from the competition in three key ways:
1. Unparalleled Precision and Automation: We are pioneers in Continuous Threat Exposure Management (CTEM). Unlike traditional solutions that focus on individual aspects of security, Strobes seamlessly integrates Attack Surface Management, Penetration Testing as a Service (PTaaS), and Risk-Based Vulnerability Management (RBVM) into a single platform. This comprehensive approach provides a holistic view of your threat landscape, allowing you to identify and address vulnerabilities with unmatched accuracy and efficiency.
2. Actionable Insights for Every Stakeholder: Strobes go beyond simply identifying vulnerabilities. Our platform empowers informed decision-making across your organization. With customizable dashboards, you can tailor security insights to the specific needs of different roles. This ensures everyone, from security professionals to executives, has the actionable information they need to effectively manage risk.
3. Future-Proofed Security with Integrations: Strobes understands that vulnerability management is an ongoing process. That's why we offer over 100 integrations with leading vulnerability scanners and security platforms like Jira and ServiceNow. This seamless integration streamlines workflows automates reporting and vulnerability management, and reduces the burden on your security team. This ensures your security posture remains adaptable and efficient in the face of evolving threats.


