Photo Gallery
|

|
Symantec Endpoint Security for the Cloud Generation

Additional Info
| Company | Symantec |
| Company size | 10,000 or more employees |
| Website | https://www.symantec.com/products/endpoint-protection |
NOMINATION HIGHLIGHTS
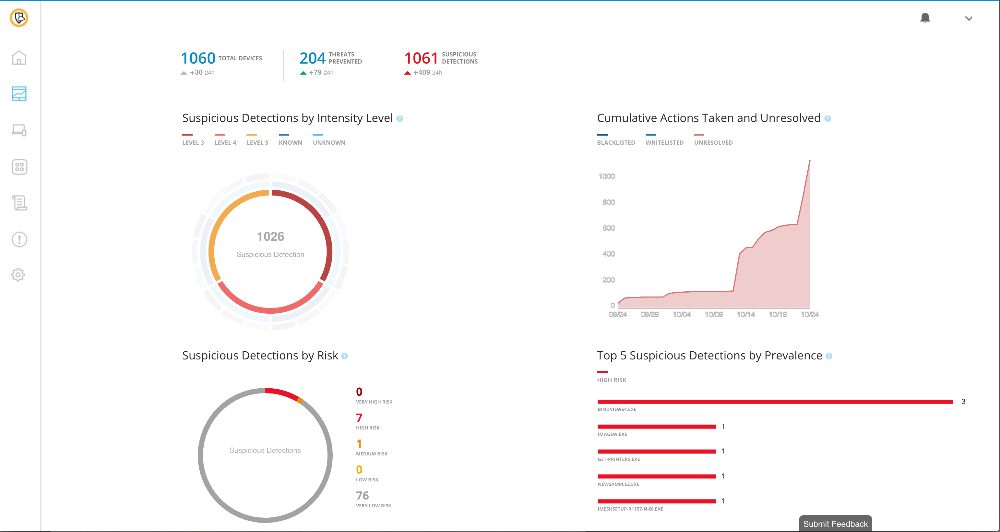
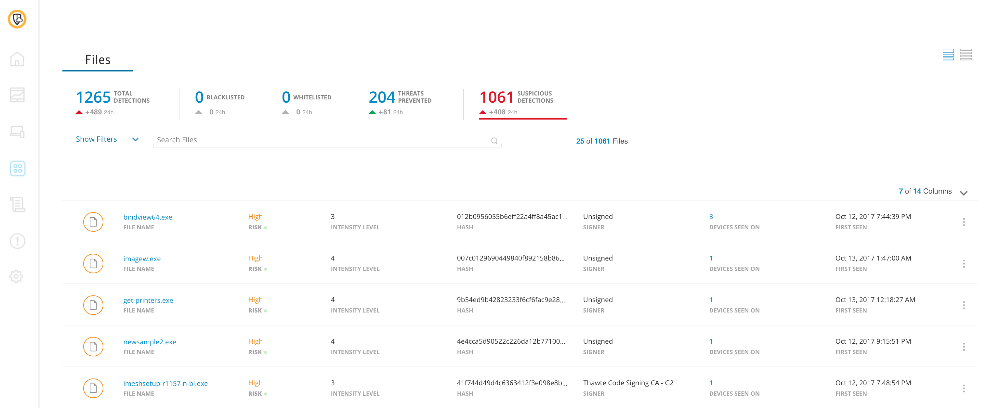
Symantec Endpoint Security for the Cloud Generation delivers the first solution of its kind by building on its market-leading Symantec Endpoint Protection (SEP) platform, combining deception technology, Mobile Threat Defense for iOS and Android, and Endpoint Detection and Response (EDR) in a single agent. The platform employs SEP 14.1 to apply advanced machine learning techniques and behavioral analysis that enables intensive protection that can be optimized for customer environments. SEP Hardening prevents vulnerability exploits including zero-day attacks and mitigates damage from attacks by shielding and isolating suspicious and malicious activity targeted toward commonly used applications.
How we are different
Symantec Endpoint Security for the Cloud Generation is the first endpoint security solution to offer the following technologies:
Next Generation and Traditional Protection - Symantec Endpoint Security for the Cloud Generation provides the most advanced and fully-featured endpoint solution available in a single agent by bringing together deception technology, Mobile Threat Defense for iOS and Android, Endpoint Detection and Response (EDR), Hardening and intensive protection through advanced machine learning. Symantec’s Endpoint Protection proactively blocked more than one billion WannaCry infection attempts.
Single Agent Architecture - Symantec’s single agent architecture allows CISOs and IT teams to monitor, manage and contain threats while reducing operational complexities. Through its integration framework, additional partner solutions can be integrated with Symantec Endpoint Protection (SEP) to ensure existing enterprise security architectures are orchestrated for response and minimized costs.
Deception at Scale – Symantec is the first to bring built-in deception techniques to the endpoint protection market. Deception technology deceives attackers into believing they have successfully breached an organization, when in reality, attackers are shunted to a false environment, served up fake assets and information – essentially leading them on a "wild goose chase" – while the security team works to neutralize the attack.


