Photo Gallery
 |
 |
Synopsys Seeker IAST

Additional Info
| Company | Synopsys |
| Company size | 10,000 or more employees |
| World Region | North America |
| Website | http://www.synopsys.com |
NOMINATION HIGHLIGHTS
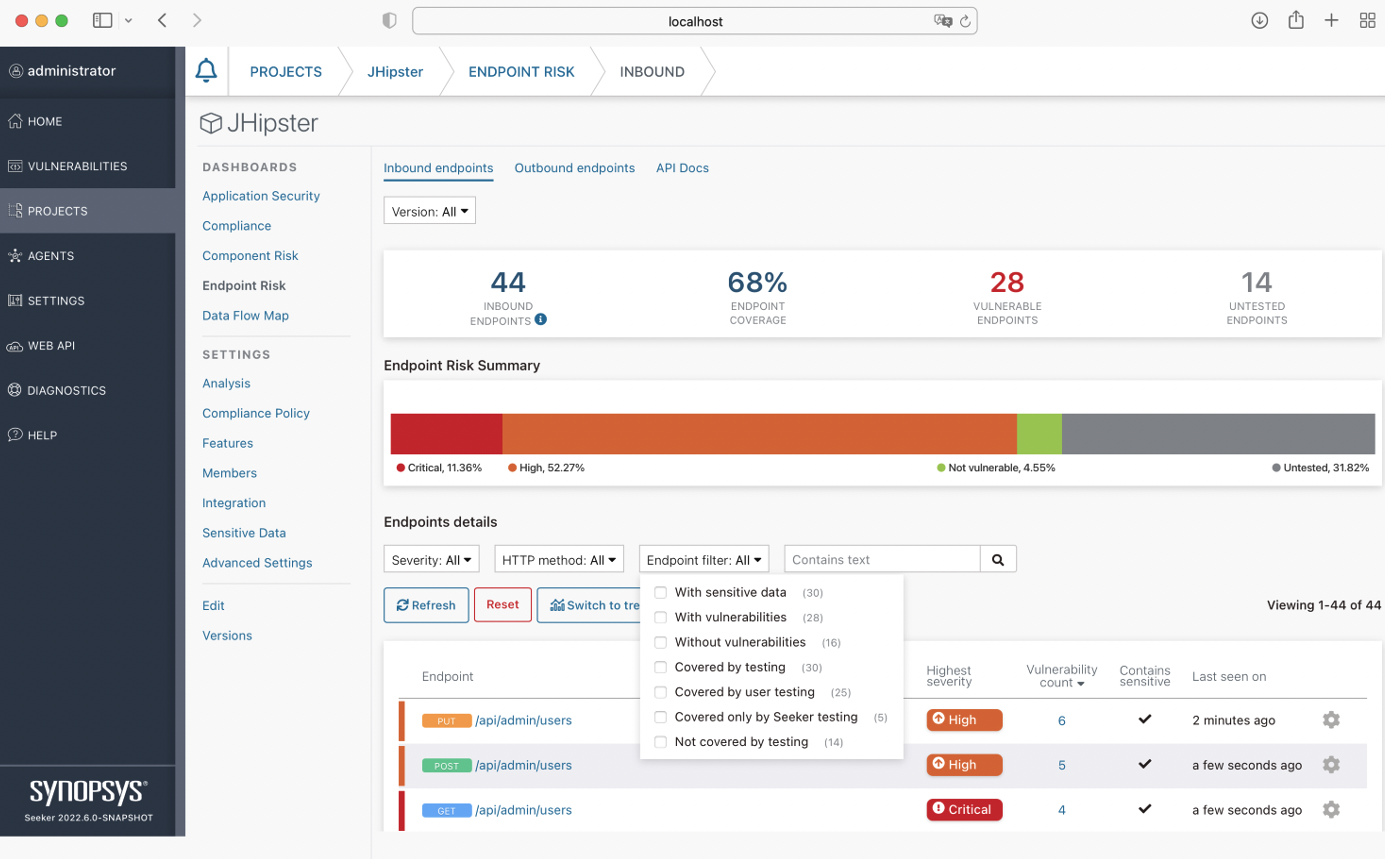
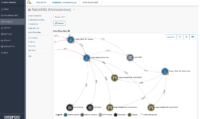
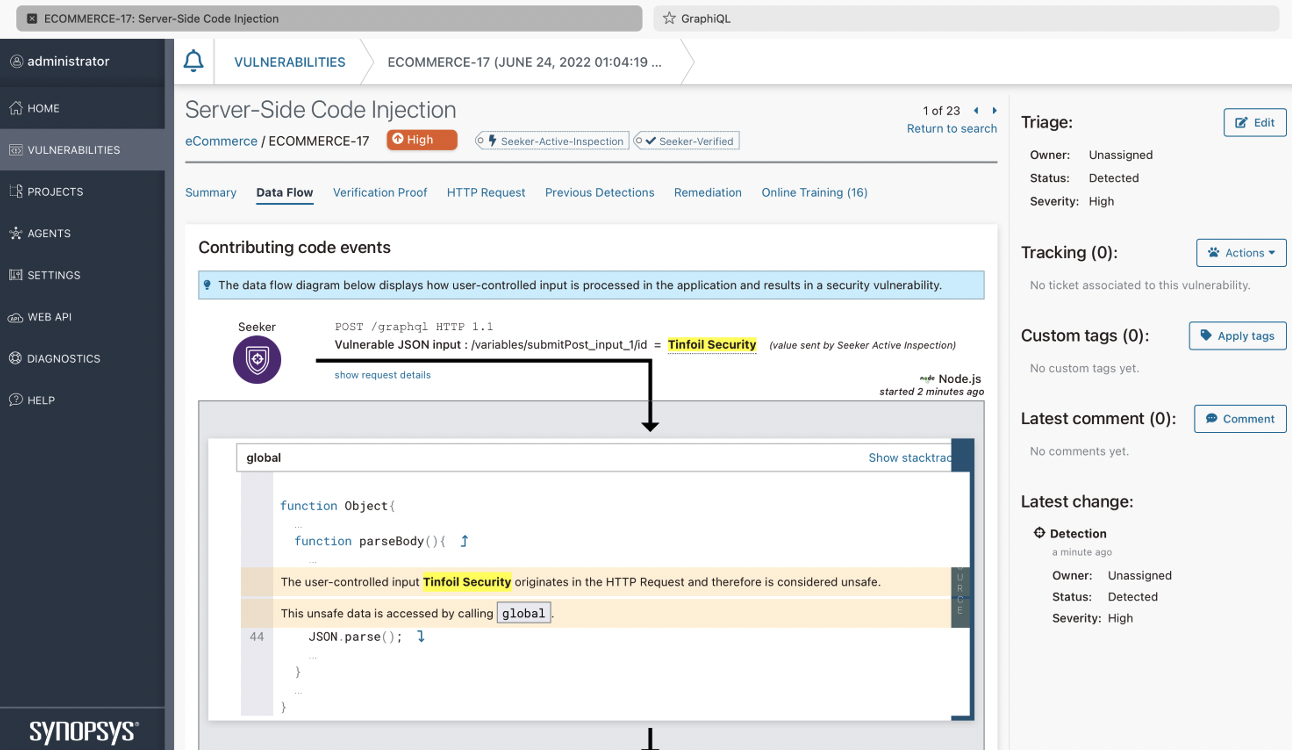
Synopsys’ Seeker IAST discovers and catalogues API endpoints, and extensively tests web services and APIs at runtime to detect OWASP Top 10 vulnerabilities during functional testing. Seeker provides continuous runtime testing, a detailed dataflow diagram and taint analysis across micro-services, and also generates automatic test traffic for OpenAPI and GraphQL based APIs. Seeker provides dashboards, reporting, vulnerability lifecycle management, a REST API, integrations with 3rd party issue tracking systems, and line-of-code level visibility of the underlying causes of detected vulnerabilities.
Seeker IAST does not require API specifications. Instead, Seeker relies on functional test activities to drive traffic to APIs, and its API endpoints discovery engine. When API specifications are available, Seeker can use them to self-crawl the applications for comprehensive coverage. Seeker can intercept and reuse authentication tokens used with the application to carry out the full self-crawling testing automatically, without the need for configuring authentication. This eliminates time-consuming and expensive configuration work while speeding up time to results without further human intervention.
Seeker notes the delta between test runs and can automatically open and close vulnerabilities in the context of the changes between versions. This reduces the administrative burden on engineers tasked with finding and fixing issues. These changes can also be propagated automatically to third-party bug tracking tools such as JIRA.
Additionally, Seeker IAST is designed to be integrated into the SDLC during the testing phase to analyze applications, self-crawl APIs, and leverage other tools such as Postman tests to gain enhanced coverage.
How we are different
- API discovery, cataloguing, and testing:
Seeker discovers all declared endpoints/APIs inside an application (including untested endpoints) to provide a unique view of the attack surface – a complete inventory of endpoints with the detected vulnerabilities and associated risks. Seeker provides continuous testing of all inbound and outbound APIs. OpenAPI specifications are automatically collected and displayed in the Seeker UI. The built-in API Scanner engine can also ingest and convert HAR and Postman files to provide seamless discovery, testing and analysis of APIs without documentation.
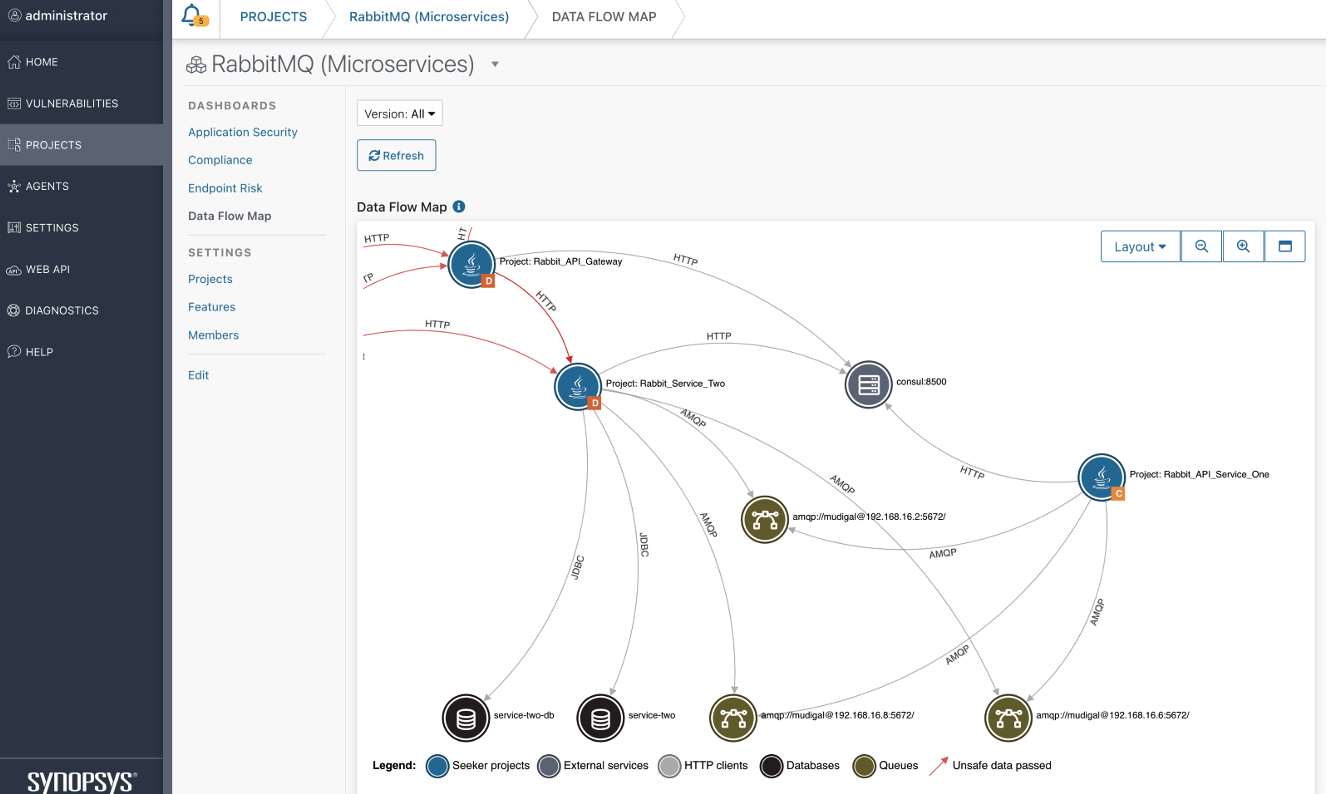
- Microservices visualization and analysis:
Seeker creates a data flow map of communicating services, including interactions between services, queues, databases, and external API calls. This capability is particularly useful for identifying the OWASP Top 10 2021 issue: A04 - Insecure Design. One of Seeker’s differentiators is the ability to track data across different services and resources, analyzing the full journey of unsafe data through the system. Seeker tracks dataflow between microservices over HTTP, Kafka, gRPC, Apache Dubbo and RabbitMQ. In addition, Seeker also supports serverless function calls like AWS Lambda and Azure Functions.
- Integrated SCA and reachability:
Seeker integrates with Black Duck and Black Duck Binary Analysis to automatically run Software Composition Analysis on the application binaries. Seeker can also identify and instantly report on the vulnerable methods and open source components in use for timely developer remediation. that are actually called to eliminate SCA noise.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



