Photo Gallery
|
|
Targeted Attack Protection (TAP)

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | proofpoint.com |
NOMINATION HIGHLIGHTS
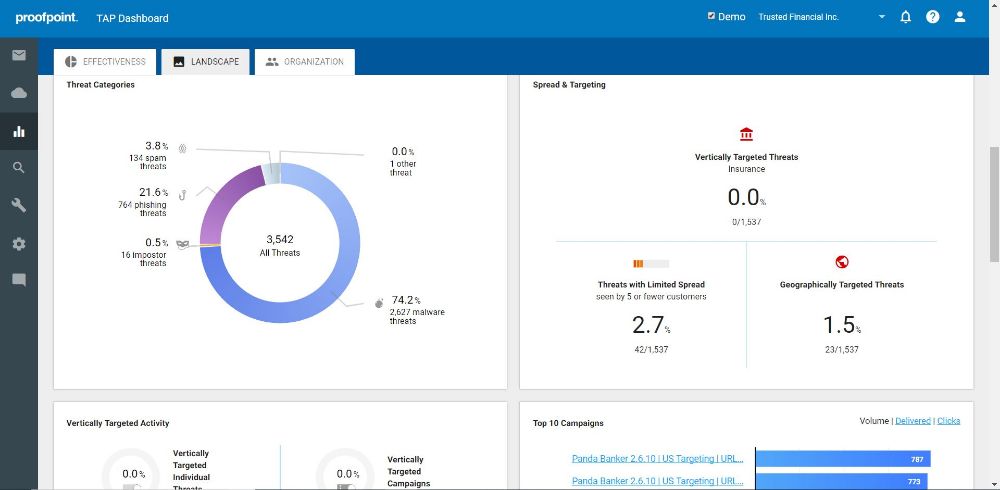
Targeted Attack Protection (TAP) protects against ransomware and advanced threats that target people and their data via the tools they use to conduct business. TAP features multiple machine learning engines spanning threat classification, composite multistage threats, relationship and communication classification, key employee classification, and evolving page design classification to not only detect new and emerging threats, but also leverage that data to inform future detection.
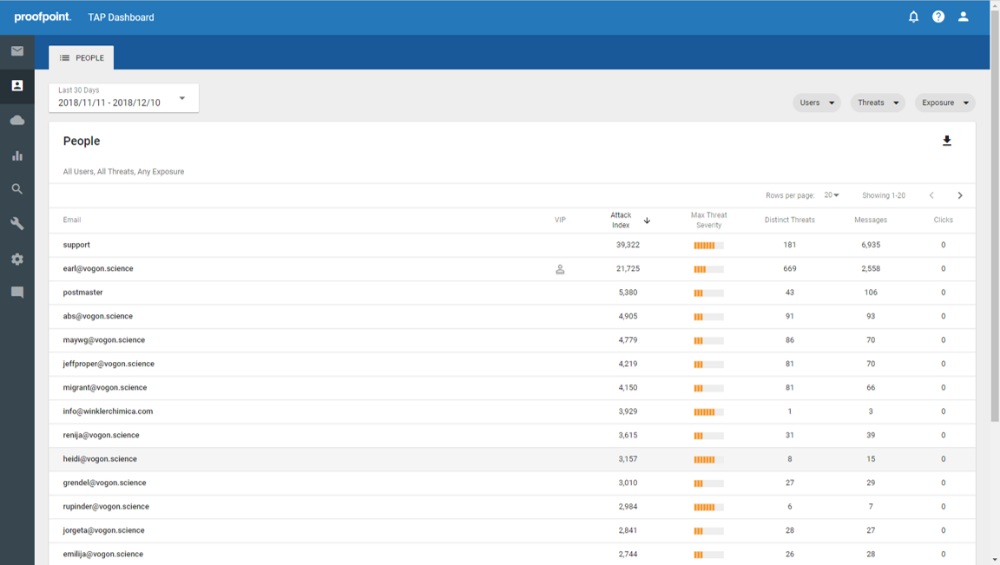
When observing an organization’s attack profile, security teams must balance the number of incoming threats with each threat’s severity. Users with the highest threat volume do not always represent the users that pose the most risk. Likewise, the lowest threat volume does not always equal the lowest risk as highly targeted threats are often more dangerous than widespread threat campaigns.
TAP customers have access to a unique Attack Index capability that provides security teams with a people-centric view into their organization’s security posture. With Proofpoint’s Attack Index, security administrators gain the unique ability to identify the very attacked people (VAPs) within their company and select policies and controls to better secure those users.
Proofpoint’s Attack Index provides a weighted composite score of all threats sent to an individual in an organization. With this visibility and insight, security teams can tailor their security policies, solutions, and trainings to help mitigate their VAP risk and prioritize where and how to apply controls to protect those most at risk.
TAP consists of three to five levels of sandboxing, culminating in analyst-led or sandbox analysis and forensics. These sandboxes work alongside multiple machine learning engines spanning threat classification, composite multistage threats, relationship and communication classification, key employee classification, and evolving page design classification. This functionality not only detects new and never seen before threats, but also leverages its data to inform future detection.
How we are different
• TAP’s effectiveness is underscored by the fact that over 70 security vendors and governments agencies license its components under the Emerging Threats ETPro Ruleset brand.
• TAP greatly reduces threat volume and severity and reduces the staffing requirements for both front end threat analysis and back-end incident response. TAP has been shown to minimize the impact of the cybersecurity workforce shortage and enable messaging teams to deliver better uptime and quality of service. In some cases, customer have stated that TAP’s 2% to 10% increase in effectiveness has a material impact on risk of infection and data loss that could not be bridged by hiring upwards of 10 more employees.
• TAP’s training corpus includes 600+ billion nodes of threat data gathered from continuous detection across our systems with some of the highest threat detection rates for email, mobile, social, network, and SaaS threats. This detection pool continually grows as our detection systems also include a worldwide sensor network and one of the largest malware exchanges on the market.


