Photo Gallery
 |

 |
Targeted Attack Protection (TAP)


Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
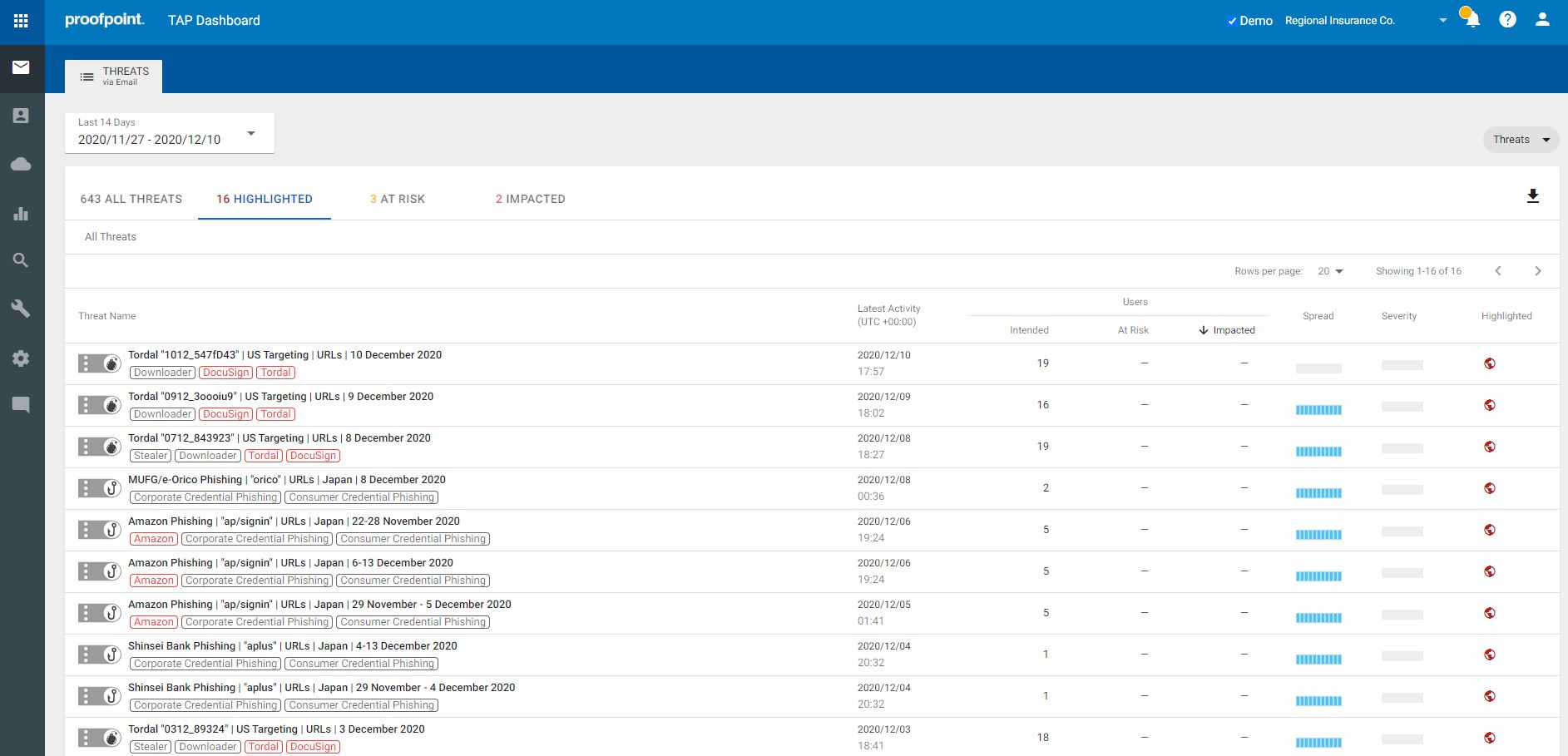
• Targeted Attack Protection (TAP) protects against ransomware and advanced threats that target people and their data via the tools they use to conduct business. TAP uses static and dynamic techniques to continually adapt and detect new cyber-attack patterns. We analyze potential threats using multiple approaches to examine behavior, code and protocol. This enables us to detect threats early in the attack chain. This sandboxing and analysis take place in virtual environments, bare-metal hardware, and they leverage analyst-assisted execution to maximize detection and intelligence extraction. TAP also detects threats and risks in cloud apps and connects email attacks related to credential theft or other attacks. Our technology doesn’t just detect threats and ransomware—it also applies machine learning to observe the patterns, behaviors, and techniques used in each attack. Armed with that insight, TAP learns and adapts.
TAP offers:
o URL Defense:
Protection against URL-based email threats including malware-based threats and credential phishing
Predictive analysis that preemptively identifies and sandboxes suspicious URLs based on email traffic pattern
URLs are rewritten to protect users on any device or network as well as provide real-time sandboxing on every click
o URL Isolation for hi-risk users
Provides adaptive security controls for your very attacked person (VAPs) based on risk profile
Enable users to access unknown or risky websites while still protecting your organization against URL or web-based attacks
Provides enhanced visibility and protection for permitted clicks
o Attachment Defense:
Protection against known malicious documents
Unknown attachments are analyzed and sandboxed
Includes sandboxing and analyses of numerous file types, password protect documents, attachments with embedded URLs and zip files
o SaaS Defense:
Surface suspicious log-in activity
Gain visibility into broad file sharing
Detect critical and high severity third-party applications
How we are different
• Unparalleled Protection – TAP leverages numerous techniques to protect against the everchanging threat landscape. This includes leveraging both our Nexus Threat Graph and NexusAI which provides real-time sharing of threat intelligence from the number 1 deployed solution across the F100, F1000, and G2000 as well as being the market leader in email and leading in other vectors such as cloud, network and social.
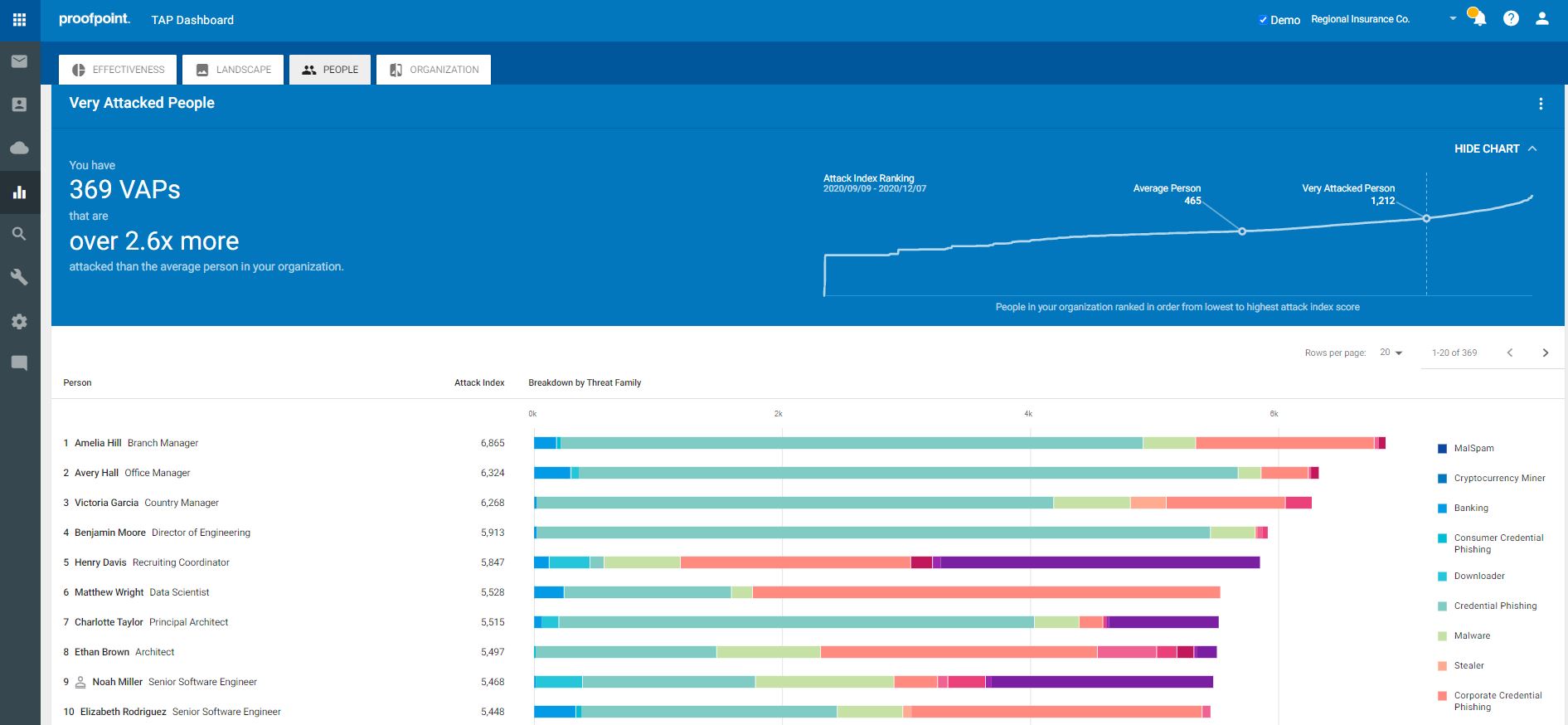
• Unmatched Visibility – TAP provides detailed information on threats and campaigns in real time. You gain visibility into both widespread and targeted attacks. It gives you details around the threat itself from impacted users, attack screenshots, and very in-depth forensics. Your security teams need to know who your most attacked people, or VAPs, are in order to protect them against the threats and ransomware that target them. The Proofpoint Attack Index helps identify these VAPs. This index is a weighted composite score of all threats sent to an individual in your organization. It scores threats on a scale of 0-1000 based on four factors: threat actor sophistication, spread and focus of attack targeting, type of attack, overall attack volume. By better understanding your VAPs, you can then prioritize the most effective ways to resolve threats.
• Integrated Across Security Ecosystem – The threat forensics and VAP information can be integrated with Proofpoint solutions as well as other industry leading vendors such as CrowdStrike, Okta, SailPoint, CyberArk, Palo Alto Networks and Splunk.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



