Thales Protection for Google Client Side Encryption
Recognized in the Category:
Photo Gallery
|

|
Thales Protection for Google Client Side Encryption


Additional Info
| Company | Thales |
| Company size | 10,000 or more employees |
| Website | http://www.cpl.thalesgroup.com |
NOMINATION HIGHLIGHTS
Customers using Google Workspace Client-side encryption can
achieve stronger security and lower deployment overheads by
benefiting from Thales’s integrated end-to-end solution that protects
identities and controls encryption keys separate from their sensitive
data in the cloud.
Client-side encryption keys enable service providers to host
encrypted data but not decrypt it, protecting the user’s privacy.
When a user retrieves their file, the corresponding data encryption
key is decrypted using customer-provided keys only after the user
has been authenticated with customer-controlled authentication.
Thales’s SafeNet Trusted Access (STA) used with CipherTrust Cloud
Key Manager provides customers with an independent IDP and key
management solution from a single vendor, helping you achieve
your business goals with a smoother deployment, superior user
experience and better value.
Thales is a trusted multi-cloud partner. The combination of STA
and CipherTrust Cloud Key Manager allows organizations to
keep control of both their access security and key management
while avoiding vendor lock-in – vital to supporting multi-cloud
environments as part of digital transformation initiatives
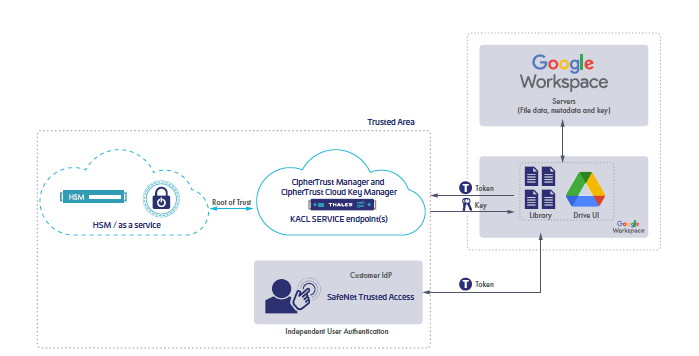
How the Joint Solution Works
A user logs into Google Workspace and is redirected to STA for
authentication and identity validation.
• STA authenticates the user and creates an authentication token
• When the user creates a Client-side encrypted file, the STAgenerated
authentication token and a separate Googlegenerated
authorization token are sent to the CipherTrust Cloud
Key Manager with a Google-generated Data Encryption Key
(DEK)
• CipherTrust Cloud Key Manager validates the STA-generated
authentication token with STA and validates the Googlegenerated
authorization token with Google
• If both tokens are validated, CipherTrust Cloud Key Manager
encrypts the DEK with a CipherTrust-generated Key Encrypting
Key (KEK) – and returns the encrypted DEK to Google
• Subsequent file opens or saves require validation by CipherTrust
Cloud Key Manager which permits authorized
How we are different
1) Identity Protection for Client-side encryption
STA serves as an independent third party IDP and
authenticates users to Google Workspace. STA enables
authentication for Google Workspace Client-side encryption
via an OIDC integration.
2)Enhancing Authentication and Secure Access to
Google Workspace
STA federates with Google Workspace via a SAML
integration, enabling single-sign-on, and enforcing the
appropriate level of authentication when users log into their
Google service.
3) Simple and Strong Authentication
Apply a Zero Trust security model by enforcing authentication
1st, access later concepts, with strong and continuous
authentication, single-sign-on, and multifactor authentication to
all resources. Authentication methods include: FIDO, hardware
tokens, software tokens (OTP apps), out-of-band (OOB)
push authentication, certificate-based authentication (CBA),
pattern-based authentication, OOB via SMS and email, and
contextual authentication.


