Photo Gallery

|

|
Thales SafeNet Trusted Access

Additional Info
| Company | Thales |
| Company size | 10,000 or more employees |
| Website | https://www.thalesesecurity.com/ |
NOMINATION HIGHLIGHTS
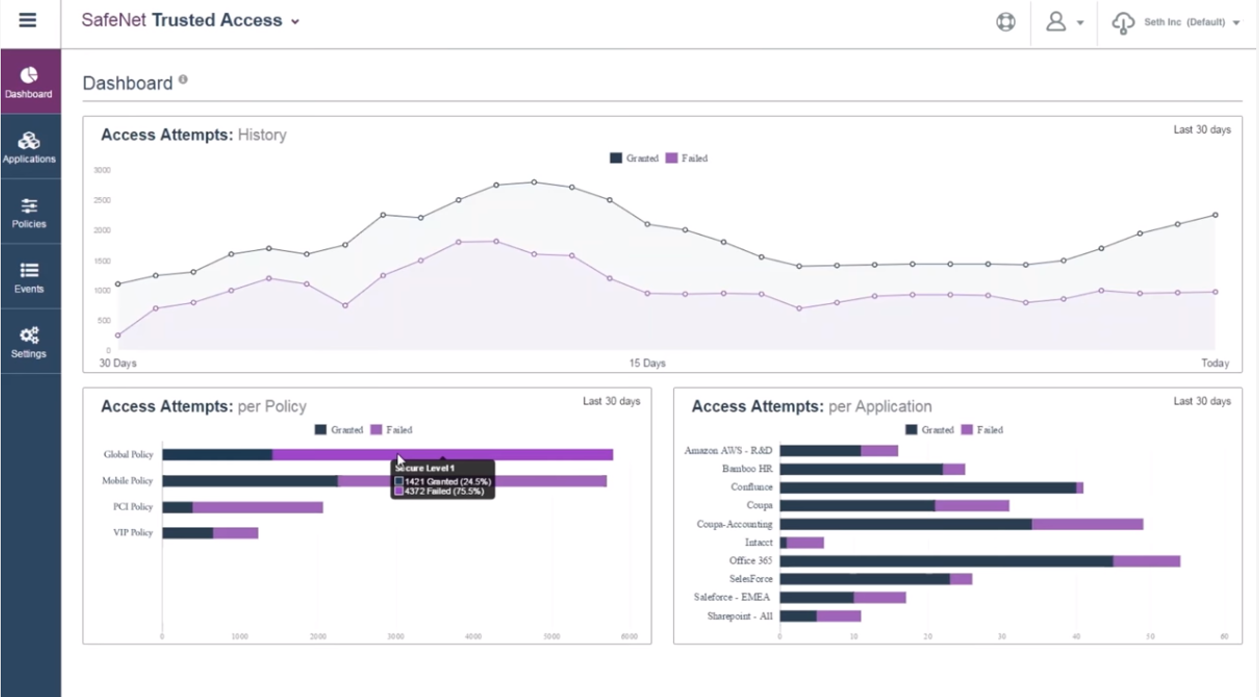
SafeNet Trusted Access is a cloud-based access management service that centrally manages and secures access to web and cloud-based applications, and simplifies the login experience for users by applying flexible risk-based policies, cloud SSO, and universal authentication methods. The service enables organizations to scale cloud access controls while meeting business, risk management and compliance needs. Even though the service is cloud based, it also provides the flexibility to leverage existing authentication methods for cloud access management and SSO.
SafeNet Trusted Access offers enterprises five core capabilities:
• Smart Single Sign-On lets users log in to all their cloud applications with a single identity, eliminating password fatigue, frustration, password resets and downtime.
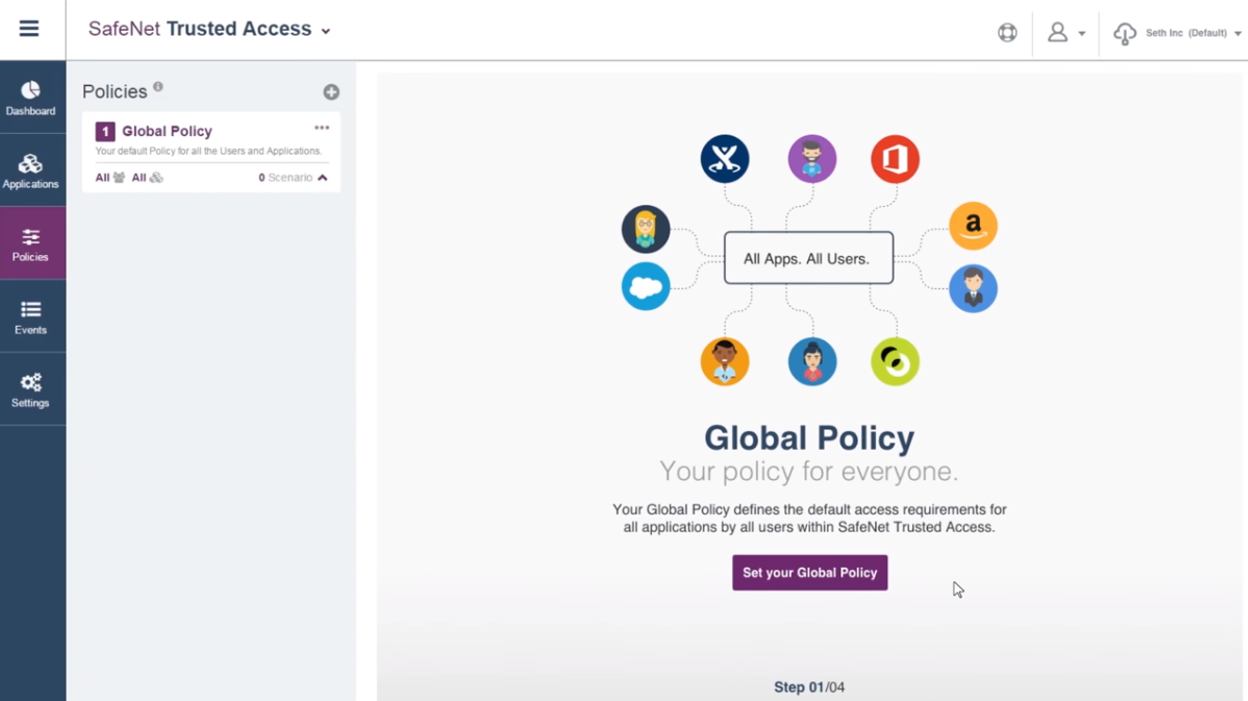
• Flexible access management through a simple to use policy engine gives customers real-time control over the ability to enforce policies at the individual user, group or application level.
• Data-driven insights into access events enable organizations to fine-tune their access policies, and ensure that they are neither too lax nor too stringent.
• Support for numerous authentication methods and allows organizations to leverage authentication schemes already deployed.
• Hundreds of easy app integrations enable the easiest connectivity to leading cloud apps, such as Salesforce, AWS, Slack and Office 365.
How we are different
SafeNet Trusted Access has several distinct advantages over other competing products and services, including:
• 100% cloud-based vs. other competitors who only offer on-premises or hybrid versions
• Ability to set up flexible access management through a simple to use policy engine that gives real-time control over the ability to enforce policies at the individual user, group or application level. Other competing products do not offer this level of granularity.
• Ability to use third-party authentication methods and form factors and built in support (no need for additional authentication service) for a very broad range of authentication methods, including the ability to use existing certificate-based PKI smart cards and infrastructure and take advantage of cloud SSO

