Photo Gallery
 |

 |
The Forescout Platform

Additional Info
| Company | Forescout Technologies Inc. |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.forescout.com/ |
NOMINATION HIGHLIGHTS
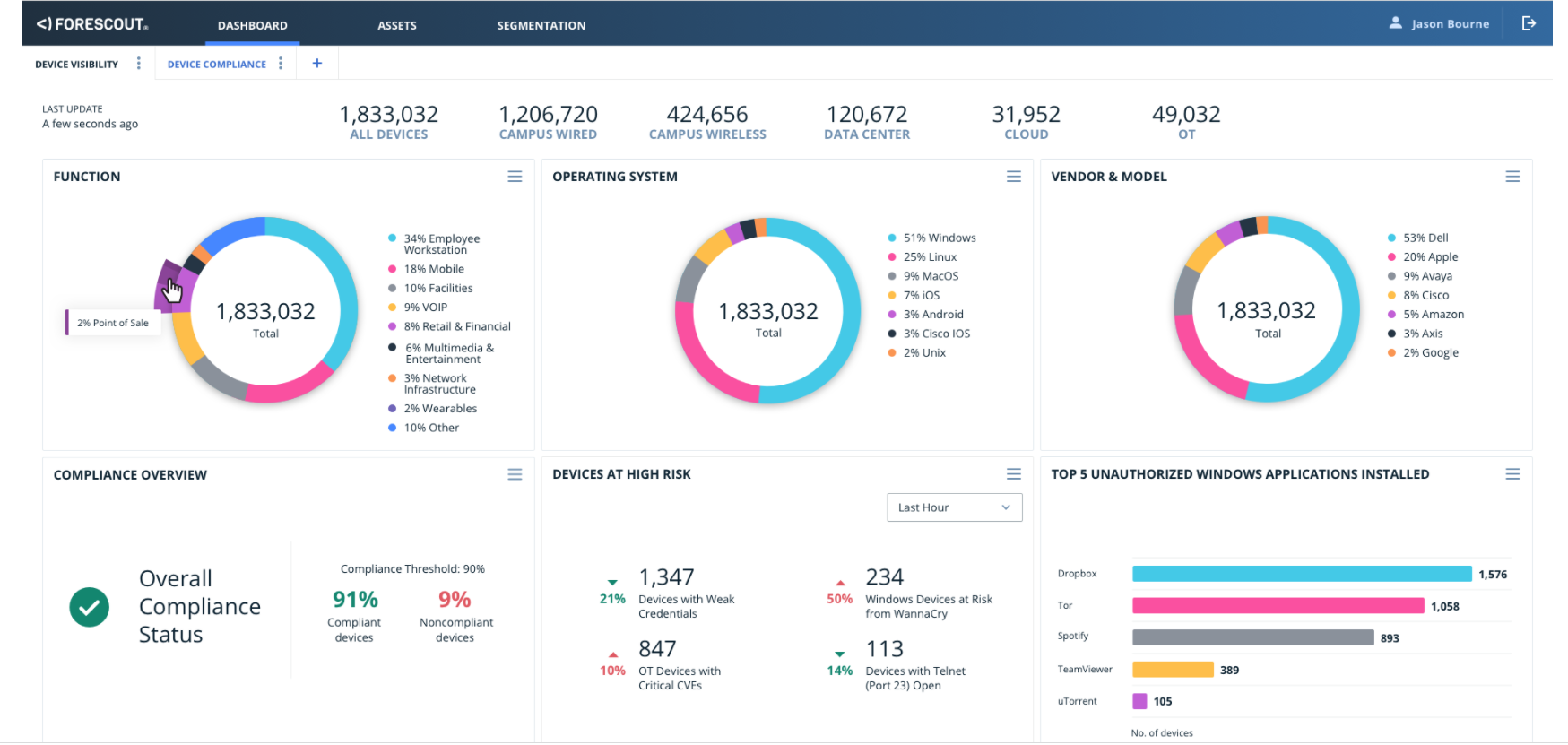
As more companies recognize the growing cybersecurity risk posed by connected devices, they are turning to Forescout for help.
The Forescout platform allows customers to effectively manage cyber, operational and compliance risks across the environment by identifying and classifying IoT devices and providing real-time insight into devices’ communication and risky behavior across the extended environment.
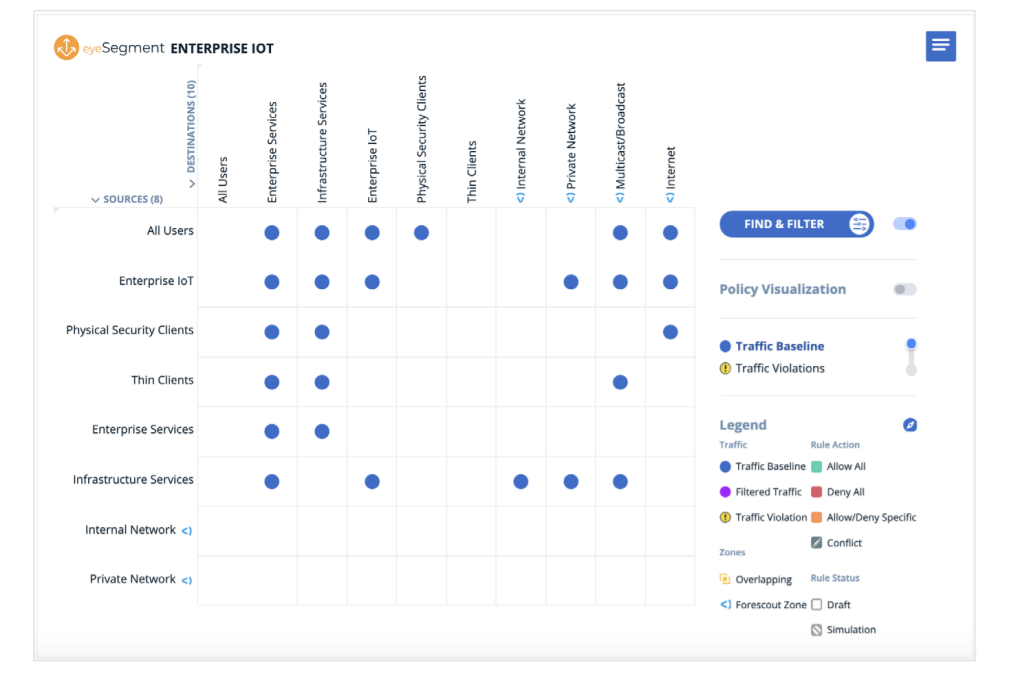
Forescout believes that IoT security must be based on a Zero Trust approach that combines complete device visibility, proactive network segmentation and least-privilege access control of all digital assets –devices, users, apps and workloads. When organizations gain visibility into everything connected to the network, including IoT and OT devices, they can start understanding how to apply decisions on who and what has access to company information or applications. Knowing what and who is on the network will enable enterprises to segment with confidence. Customers will also be better able to quantify their cybersecurity risk profile, meet compliance needs and manage asset inventory.
To further support organizations with their Zero Trust initiatives, Forescout recently expanded its set of network segmentation capabilities on the Forescout platform that will provide end-to-end visibility and real-time analysis to automate risk mitigation and policy management.
These capabilities offer a clear path from managed network access to full Zero Trust. A clear path to execute network segmentation is imperative, and embracing these three principles guides Forescout and its customers to the most successful network segmentation outcomes:
– Understand their business requirements
– Know what is on the network and how it communicates
– Visualize traffic flows
Overall, Forescout’s 20+ years of device intelligence has allowed the company to get ahead of and solve incredibly complex security challenges while enabling customers to be the beneficiaries by providing them easier pathways to execute.
How we are different
-For 20+ years, Forescout has been focused on the fundamental principle of visibility for cybersecurity. The platform’s ability to discover all device types (IoT, OT, IIoT, IoMT and IT), assess risk, ensure compliance, and provide governance collectively with existing tools is unique to the market and what makes the Forescout platform the leading option to provide active defense in today’s Enterprise of Things. After deployment, the platform can detect 30% more devices on average than customers originally anticipated. Companies are thus better equipped to know what is on their network and how it communicates, visualize traffic flows, understand business requirements, and apply decisions based on who and what has access to company information or applications.
-Besides visibility, the platform is beneficial for its efficiency. It deploys quickly at large-enterprise scale – managing more than two million endpoints per deployment – without the need for infrastructure upgrades, resulting in faster ROI and lower TCO. The key components of achieving this efficiency include 1) Real-time, continuous assessment of risk and compliance, including rich, configurable dashboards and exportable reports, and risk scoring with clear, realistic recommendations to reduce inherent risk 2) A dedicated solution to design and enforce segmentation policies, reducing the attack surface and blast radius and 3) The ability to automate workflows and execute agentless actions for all managed, unmanaged, and third-party endpoints such as network access control, compliance enforcement, and incident response. With Forescout, companies can take a more proactive stance in combating threats posed by all devices.
-Over 3,800 global companies trust Forescout to help them identify, segment and mitigate risks from network-connected devices. Customers further benefit from the platform’s ability to integrate with and leverage existing tools and softwares instead of requiring companies to start their security infrastructures from scratch. This saves companies valuable resources and even maximizes the

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



