The Noetic Cyber Asset & Exposure Management platform
Recognized in the Category:
Photo Gallery

|

|
The Noetic Cyber Asset & Exposure Management platform

Additional Info
| Company | Noetic Cyber |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | http://www.noeticcyber.com |
NOMINATION HIGHLIGHTS
Noetic Cyber is a market leader and innovator in Cyber Asset Attack Surface Management (CAASM). Noetic delivers a proactive approach to attack surface and exposure management, giving security teams the visibility and context to uncover coverage gaps, improve their security posture and reduce cyber risk. Our goal is to improve security tool and control efficacy by breaking down existing siloes and leveraging those insights to support broader use cases. Noetic’s award winning platform is successfully deployed in customers across Pharmaceutical, Telco, Financial Services and Energy sectors.
The Noetic platform is designed to meet customers’ use cases around attack surface management, including cyber asset visibility, vulnerability prioritization, exposure and controls management and more. The Noetic solution leverages already deployed security and IT management tools for security data, aggregating, correlating and deduplicating it into a unified graph database that maps all assets in the organization, their security posture and the cyber relationships between them. With this unique perspective, Noetic is able to provide security teams with confidence in the accuracy of their data, help them to prioritize based on real business context, and our fully integrated automation workflow engine allows them to act on the critical findings we provide.
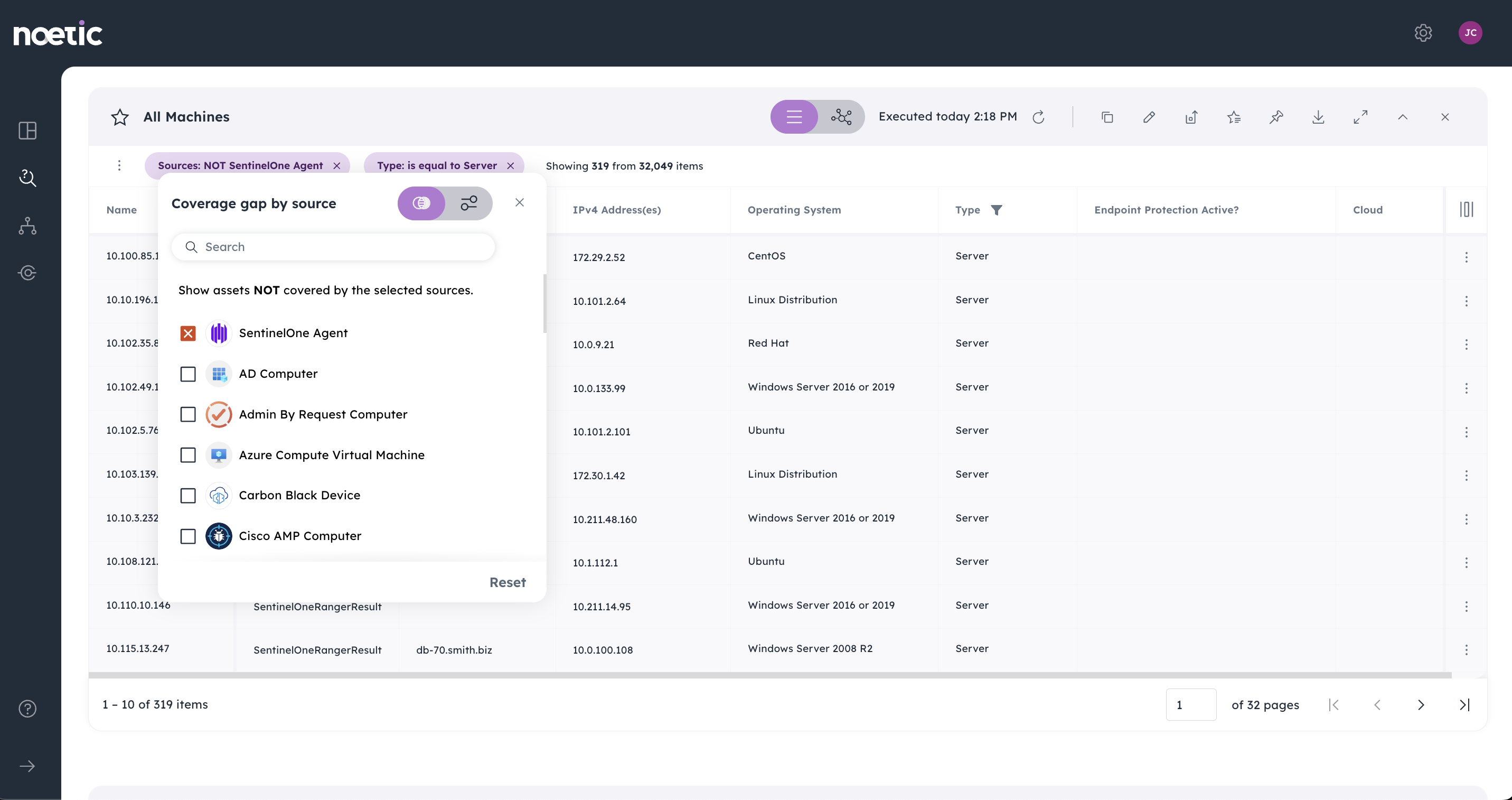
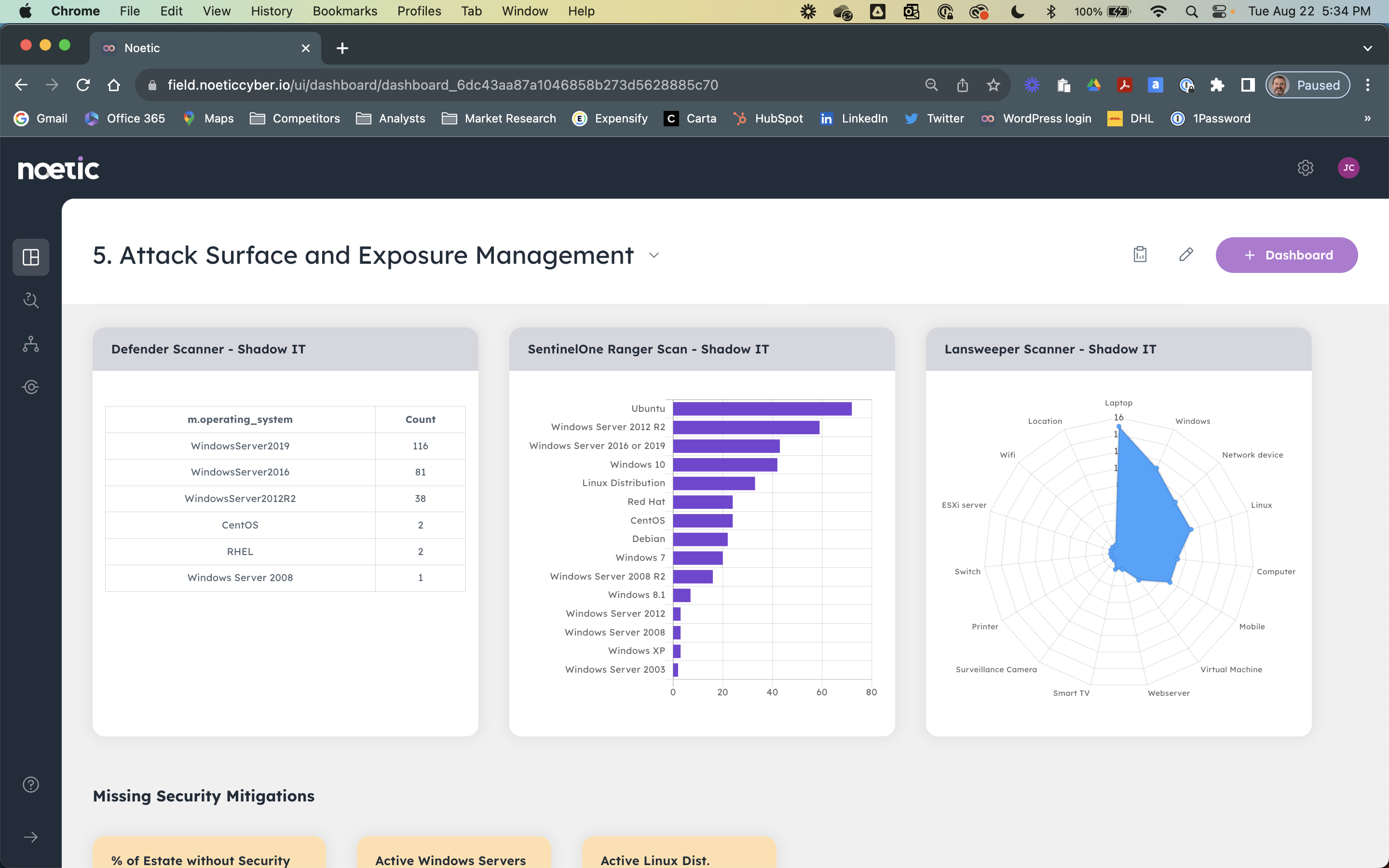
Customers use Noetic to provide them with complete, 360 degree visibility into their cyber estate across the cloud and on-premises, helping them to identify security coverage gaps, unpatched exposures and technical control drift.
Key Capabilities / Features
- Query & Analytics: Designed for simplicity, the Noetic platform enables users of all skill levels to extract actionable insights from complex data sets. All queries can be saved and automated, powering continuously updated dashboards and reports. Powered by Machine Learning to help standardize key data types, Noetic allows users to effortlessly explore and comprehend complex data sets without the need for specialized expertise. These ‘spreadsheet-like’, interactive tables enable users to quickly and easily identify common security coverage gaps and filter based on common asset fields such as type, operating system (OS), location and more.
- Customizable Dashboards & Reporting - Noetic dashboard and reporting capabilities are as dynamic as your organizational objectives. Whether you’re a CISO gathering cyber risk insights for the board or a GRC leader collecting controls evidence for an upcoming audit, Noetic translates your data into tailored dashboards that drive informed decision-making. Noetic offers pre-built, out-of-the-box dashboards designed to provide quick insights. These ready-made dashboards cover common IT, security, and GRC metrics, serving as a starting point for users looking to gain immediate visibility into key aspects of their cyber ecosystem.
- Automated Workflows: Noetic's automation functionalities are designed to revolutionize operational efficiency, offering a comprehensive suite of features that simplify processes and save precious time. Going beyond simple report generation, our extensible Automated Workflows automate tasks, eliminate manual efforts, and enable organizations to confidently implement automation for security, risk, and compliance.
- Connector Ecosystem: Discover the potential of your infrastructure with the Noetic Connector Ecosystem. Our standards-based connectors give organizations the power to maintain an agile, integrated framework that evolves in tandem with their needs. Whether your data resides in the cloud or on-premises, Noetic connectors serve as the key to unlocking a single, authoritative source of truth.
How we are different
• Confidence in their Data: Security data accuracy and quality is an industry-wide challenge. Everyone has concerns about the quality of their security data, but the truth is that all data sources have value. EDR typically has a high data fidelity but lack breadth as they need to be deployed widely to be effective. CMDB records are often incomplete or outdated, but they can provide valuable information on application ownership and business criticality. Noetic's commitment to data trust goes beyond industry norms. Our robust data ingestion approach, combined with connector-specific assessments and collaborative tuning, ensures that the accuracy of your security data not only meets but consistently exceeds expectations. Our customers trust Noetic for a reliable, accurate, and evolving data foundation for their security programs.
• Prioritize based on key insights: It's impossible for any security team to tackle every exposure and vulnerability. The essence lies in effective prioritization—addressing what matters most. Security teams need to identify simple coverage gaps swiftly but also to prioritize more complex exposures based on the greatest risk to the business. With Noetic, organizations can see not only the technical security posture of the environment, but also the cyber relationship between all assets. It is this information that helps security teams understand potential exposure and cyber risk. Our Unified Model Explorer helps security teams to understand the critical relationships between different asset types.
• Act on key findings: Visibility into the 'dark' corners of your cyber estate is crucial, but it's just the starting point of an effective exposure management program. While most CAASM solutions offer visibility into unprotected assets, misconfigurations, and orphaned machines, Noetic takes it a step further by providing actionable insights and automated workflows to not only drive informed decisions—but also act accordingly.


