Photo Gallery
 |
The Resilience Solution
Additional Info
| Company | Resilience |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://cyberresilience.com |
NOMINATION HIGHLIGHTS
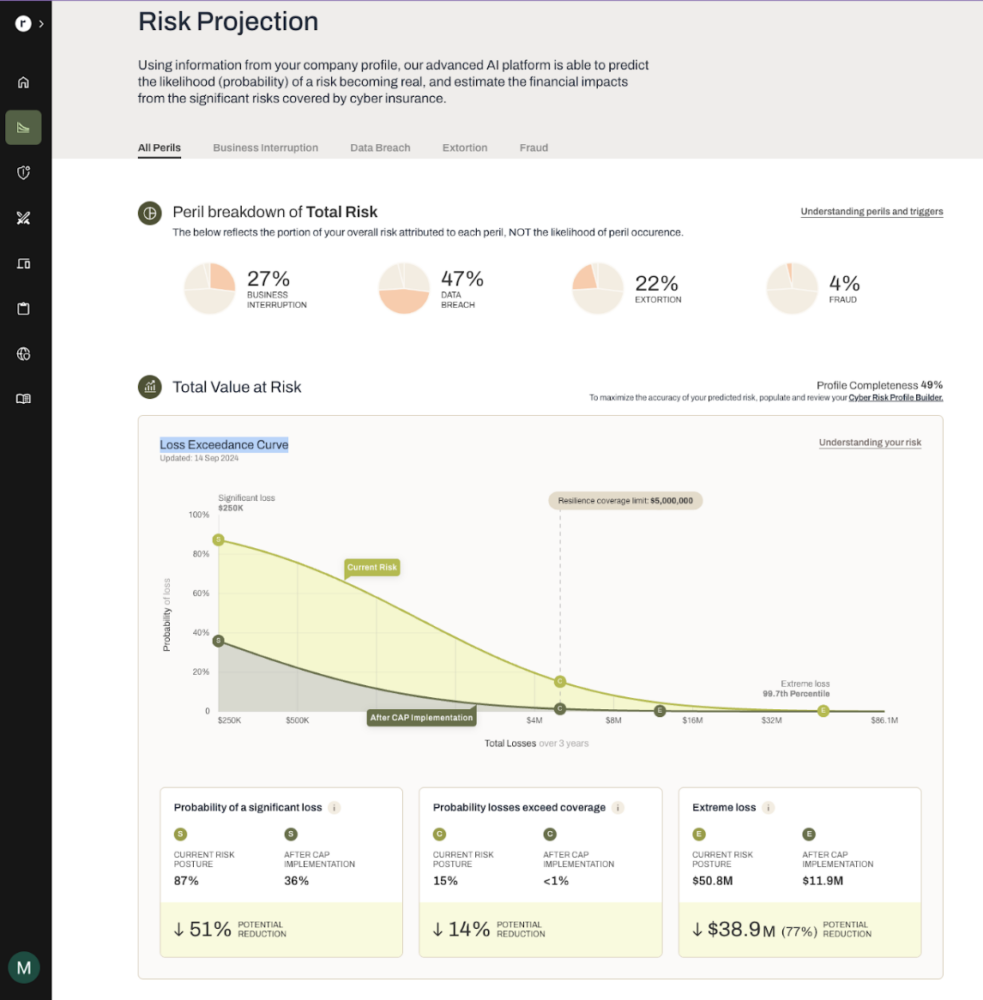
Many cybersecurity experts frame cyber risk in nebulous, hypothetical terms. But an understanding of what risk actually looks like in concrete, dollars-and-cents terminology is essential to achieving true cyber hygiene. Enter Resilience.
Resilience’s flagship offering, the Resilience Solution, uses a financially-proven AI platform to quantify and translate cyber risk into financial terms to articulate not only what could go wrong, but how much a potential exposure would cost the business. Then, Resilience creates a customized Quantified Action Plan with advice on where a company should invest resources to mitigate risk and reduce potential material loss and underwrites a dynamic cyber insurance policy to transfer some of that risk. All the while, Resilience’s Risk Operations Center (ROC)—a command center with a multidisciplinary team of data scientists, claims and incident managers, cybersecurity experts, and insurance underwriters—helps inform these strategies with real-time threat information and proactive vulnerability hunting.
Resilience’s comprehensive, one-of-a-kind approach equips companies to proactively reduce their risk, limiting material loss and ensuring business continuity when an attack inevitably occurs. It’s proven so effective that 96% of Resilience policyholders avoided claims with incurred losses in 2023. What’s more, in 2023-2024, over 90% of Resilience clients that directly experienced a ransomware attack avoided paying an extortion fee, compared to a 71% industry average.
Key Capabilities / Features
Resilience added three key features to its flagship solution over the past year to deliver more impactful results for clients and address security leaders’ pressing challenges.
Many organizations lack visibility into both their own and their vendors' resilience to cyber risk, often stemming from ineffective, inefficient vendor risk assessments and irregular internal security testing. The recent attack on CDK Global illustrates the devastating cross-supply-chain impact of insufficient risk management from either suppliers or their customers: CDK paid a $25 million ransom, and 15,000 of its customers experienced major disruptions. The similarly devastating attacks on Change Healthcare and AT&T show that even trusted vendors can present risks.
Resilience’s newly-introduced vendor risk report feature (VRR) and breach and attack simulation tool (BAS) give clients a comprehensive, real-time view of their risk profile. With VRR, clients can near-instantly receive in-depth reports on any current or prospective vendor’s security posture and adjust their relationship accordingly to minimize disruptions or loss. BAS simulates hypothetical attacks based on real-world threat tactics, providing crucial insight into what breaches look like, their impacts, and the vulnerabilities they exploit. Both tools are seamlessly integrated and centralized within the Resilience Solution platform for easy access.
Security leaders are also facing a deluge of data points from increasingly frequent attacks and the constant discovery of new vulnerabilities, making it difficult to grasp how their companies’ risks are changing and to prioritize and execute accordingly. Resilience integrated a Cyber Risk Profile Builder feature into the platform that helps CISOs maintain an up-to-date understanding of their organizations’ unique risk postures as the threat landscape changes or they implement new security tools. The Profile Builder uses the most current information—including IT footprint, prior incidents, recovery plans, and more—to accurately quantify incoming risk and calculate a recommendation for next steps.
How we are different
-With the Resilience Solution, AI-powered cyber risk management and cyber insurance are integrated, working together to maximize enterprises’ cyber hygiene. Many competitors offer both risk management and insurance, but Resilience is unique in combining the two into one financially-proven solution. This coalescence creates a positive feedback loop wherein improvements in security lower premiums—in turn motivating companies to continuously enhance their cybersecurity posture.
-Resilience ensures there’s always a human in the loop. While the Resilience Solution employs AI strategically, Resilience also recognizes the benefits of human insight. On top of providing 24/7 advocacy and support, in the event of an attack, Resilience proactively assigns dedicated cybersecurity and insurance experts to every reported issue so clients receive personalized attention. What’s more, Resilience’s team of security experts at the ROC constantly and proactively monitors emerging threats and quickly notifies clients when they’re exposed to an exploited vulnerability. Where other security companies drown clients in alerts, Resilience provides targeted, meaningful support by focusing on the threats that really matter to each individual customer.
-The Resilience Solution solves a key challenge for security leaders: communicating with the board. Understanding the nuances of cybersecurity can be a difficult undertaking for everyday enterprise leaders. Its technical complexity has historically made it difficult for security leaders to convey the business impacts of risk to non-security teams, keeping them from securing the essential resources and support to run effective security programs. The Resilience Solution not only offers unparalleled risk quantification but calculates exactly how much actions like purchasing insurance could reduce losses. This detailed analysis makes it easy for security leaders to calculate and articulate the exact ROI of their proposals to financial decision-makers.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



