Photo Gallery
 |
 |
Threat Hunter

Additional Info
| Company | Exabeam |
| Company size | 75 employees |
| Website | http://www.exabeam.com |
NOMINATION HIGHLIGHTS
Today’s enterprise breaches are after more than credit card numbers. Advanced persistent threat attacks (APT) are becoming the norm, with cybercriminals breaking into corporate networks using stolen credentials and targeting high-value, sensitive data. According to ISACA, 74 percent of enterprises surveyed think they will be a target for advanced persistent threat (APT) attacks, and 28 percent have already been attacked.
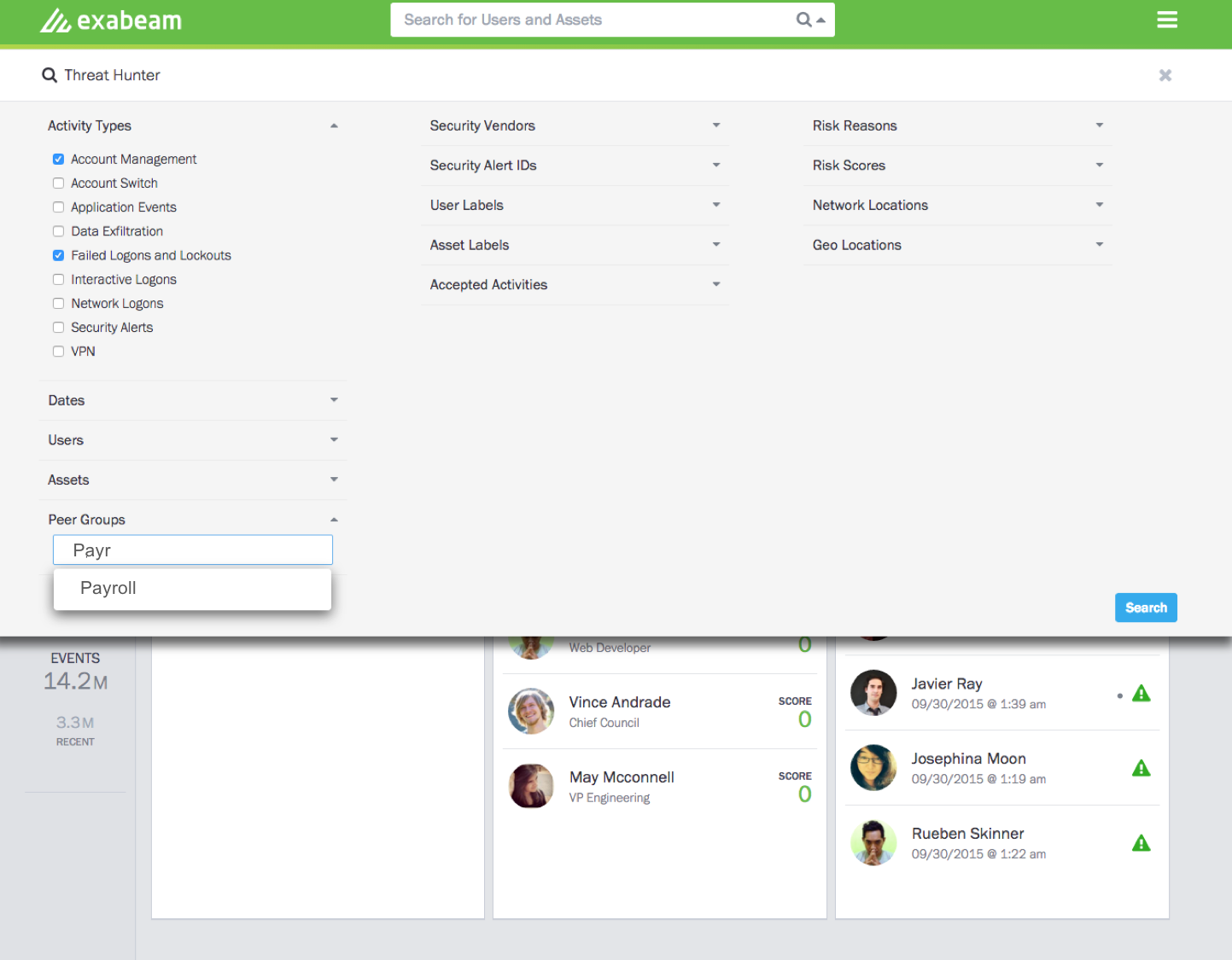
Threat Hunter is a new product for the instant and targeted querying of security big data by anyone. With Threat Hunter, security professionals can proactively identify and respond to adversaries within their networks. The product enables analysts to search, pivot, and drill down across multiple dimensions of user activity to find sessions that contain specific risky behaviors.
Exabeam’s leading UBA platform uncovers APT attacks using big data science to alert security teams to suspicious user behavior even if they change locations, devices, or logins. Threat Hunter builds on the Exabeam platform by allowing any security analyst to execute a multi-dimensional search and drill-down of user sessions to actively hunt for imposters or malicious insiders based on their unusual behavior. Threat Hunter is the only UBA-related product that allows the security analyst to interrogate and query the system to find user session that match specific criteria.
How we are different
According to Tony Palmer, senior lab analyst at Enterprise Strategy Group, the promise of User Behavior Analytics is that the system will notify security analysts about risky activities. Exabeam’s Threat Hunter provides the other half of the equation—the ability to ask the system which users match a specific set of risk criteria and get useful answers.
As the only UBA-related product that allows security analysts to interrogate and query the system to find user sessions that match specific criteria, Threat Hunter deserves recognition for its ability to provide customers:
• Increased security – Find advanced persistent threats before they cause data loss.
• Reduced chance of data breach – Find attackers that are hiding in the network by staying under the radar.
• Faster response to cyber attacks – Effectively remove all adversaries once an attack is detected by finding all traces of activity.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



