Photo Gallery

|

|
Threat Stack, Inc


Additional Info
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | http://www.threatstack.com |
NOMINATION HIGHLIGHTS
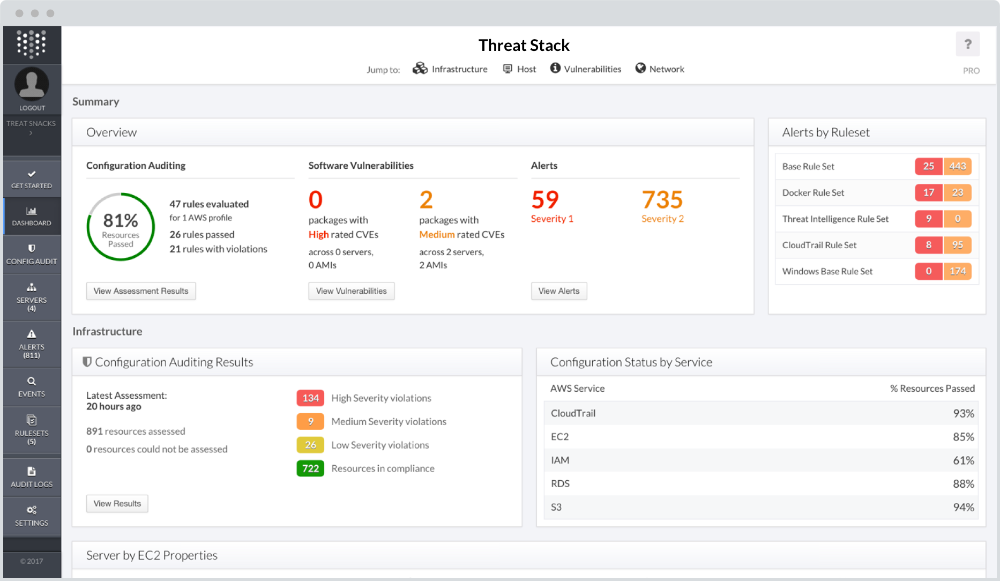
Following an aggressive growth plan in 2017, Threat Stack raised $45M in Series C funding, achieved 100% employee growth, 200% revenue growth, doubled its customer base to extend to over 1,800 users, and is utilized on more than 45,000 instances.
Threat Stack is tackling one of the most important problems facing cloud-based companies today — security visibility across the entire back-end infrastructure. We’re doing this by giving security, operations, and development professionals one platform to leverage and understand whether all compliance standards, best practices, and centralized workflows are being followed across the organization.Our rapid growth is fueled in part by the fact that it addresses a large number of security-related issues for SMB to Enterprise such as achieving compliance, moving upmarket, and strengthening internal security practices and policies across any cloud or on-prem infrastructure.
Although we are a startup, our mission goes beyond offering a comprehensive Intrusion Detection Platform. We make a point of constantly educating the market on how they can better protect themselves, how to approach security in the context of today’s cybercrime environment, and what it means to implement smart security practices across the organization.
How we are different
- Threat Stack makes security part of the everyday build and release cycle rather than a potential blocker at the end of the project. Teams using Threat Stack are able to move securely at the speed of DevOps.
- Rather than the traditional signature-based approach, Threat Stack sits at the host level and uses a behavior-based approach to intrusion detection that sends real-time alerts about any abnormal behavior from both internal and external sources.
- With continuous monitoring and real-time alerting, Threat Stack users can be certain that there are always eyes on their infrastructure. This expands beyond their own data to their customer data, which Threat Stack users know exists in a safe, secure, and compliant environment.


