Photo Gallery
 |
 |
Threat Stack Intrusion Detection Platform


Additional Info
| Company | Threat Stack, Inc |
| Company size | 100 - 499 employees |
| Website | http://www.threatstack.com |
NOMINATION HIGHLIGHTS
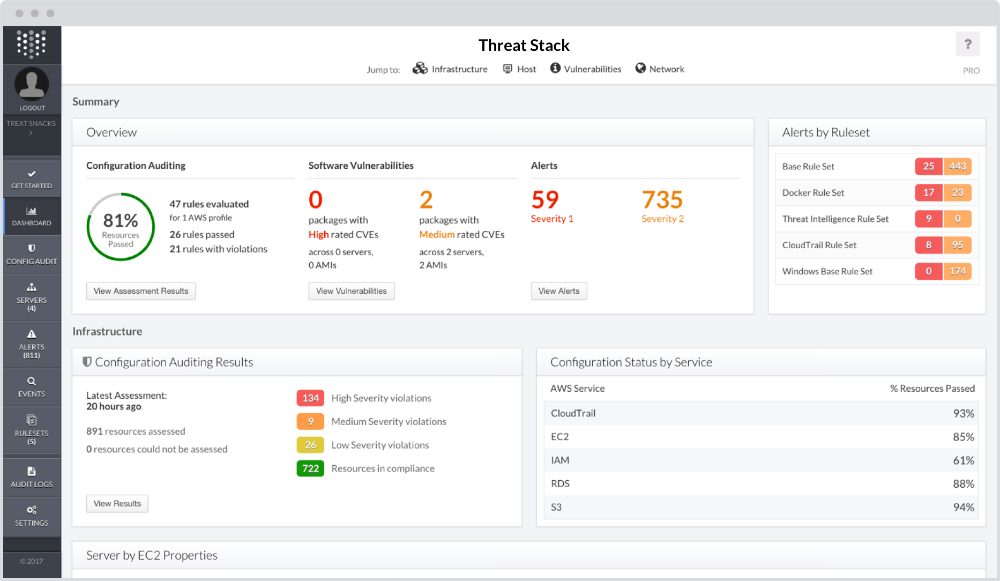
Threat Stack is a comprehensive Intrusion Detection Platform. With host-based IDS at the core, the Intrusion Detection Platform incorporates File Integrity Monitoring, Vulnerability Management, Threat Intelligence, and Configuration Auditing to deliver a full security platform that monitors for internal and external threats and answers the question of who did what, where, and when. Users are alerted in real time to potentially malicious activity and are provided with the best context possible around the alert, which reduces mean time to know about and resolve the issue from hours to minutes.
At Threat Stack, we are adapting with our customers and the market as a whole as more teams shift towards a DevOps mindset. Direct integrations with configuration management, chatops, and containerization tools give Threat Stack users the confidence to move at the speed of DevOps without security coming up as a blocker at the end of a project, but rather a continuous check on everything being developed and pushed to production.
How we are different
- Threat Stack takes a behavior-based approach to security rather than the traditional signature-based approach. This detects malicious behavior much higher up the cyber kill chain before anything is actually executed and the infrastructure is compromised.
- It manages all back-end security operations from a single platform. Host-based IDS is the core of Threat Stack, but it also enables users to manage file integrity, understand all user and file actions, know where instances are connecting out to, who is trying to ping servers, know what vulnerabilities exist, and audit the configuration of their services.
- Out-of-the-box rulesets cover most any use case one would have at a higher level, and are all easily customizable to fit specific use cases. Threat Stack also shoulders the data processing load to minimize resource consumption on the user’s instances. Because of this, there is about 1–3% CPU consumption on the user’s box and no need to spin up additional instances to support Threat Stack.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



