Photo Gallery
 |
 |
ThreatMatrix Deception and Response Platform

Additional Info
| Company | Attivo Networks |
| Company size | 99 employees |
| Website | http://www.attivonetworks.com |
NOMINATION HIGHLIGHTS
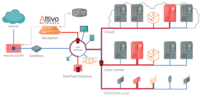
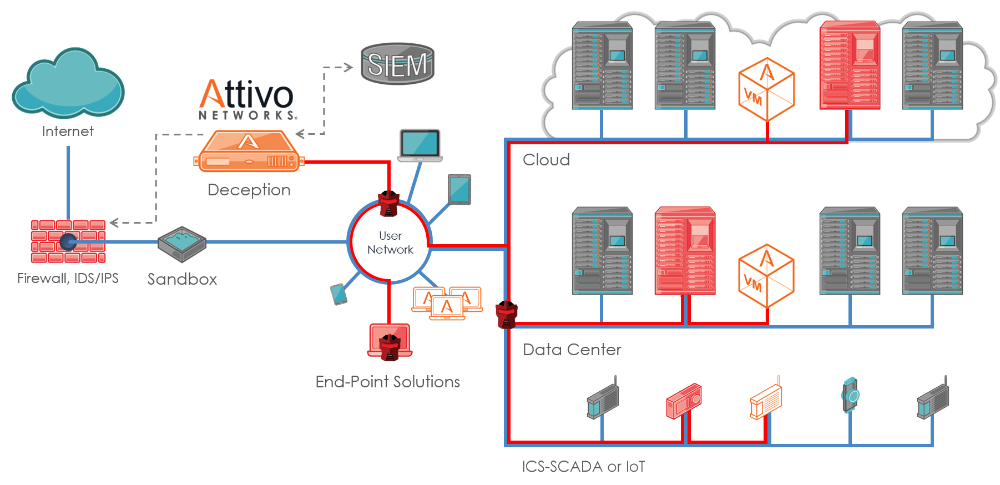
The ThreatMatrix for ICS- SCADA environments is truly a unique offering that closes the gap for early detection of attacks targeting industrial control systems. The solution is designed for threat detection on Industrial Control Systems (ICS) SCADA devices used to monitor and control most manufacturing operations as well as critical infrastructure such as natural gas, oil, water, and electric power distribution and transmission systems around the world.
SCADA support is included within the ThreatMatrix BOTsink offering, which provides support for enterprise network, public, private, and hybrid cloud, IoT, and POS in-network threat detection. With this solution, Attivo provides customers upstream and downstream threat detection for business, process controls, and field sensors. Organizations will now have real-time visibility into reconnaissance and stolen credentials attacks and will gain visibility to external, insider, and third party threats as they move laterally through the network. Regardless of whether the malware originates from a USB device, from clicking on a phishing email or through another point of access, Attivo will set the traps and provide the visibility required to quickly detect and stop an attack.
Deception is a different and highly effective solution for protecting SCADA environments, since it does not rely on knowing the attack signatures or patterns, and it also does not need to monitor all traffic to look for suspicious behavior. Deception also does not require software to be loaded or maintained on the SCADA device. Instead, deception techniques are used to confuse, delay, and redirect the enemy by incorporating ambiguity and by misdirecting their operations.
Additionally, the ThreatMatrix platform provides ThreatPath that assesses likely attack paths and attack time-lapsed reply so that organizations can understand configuration and credential vulnerabilities and the lateral movement of attacks . This information can then be used for attack prediction and strengthening of an organization’s security posture.
How we are different
The ThreatMatrix platform is truly a unique offering that closes the gap for early detection of attacks targeting ICS-SCADA devices.
With the broad variety of ICS-SCADA security devices, this solution provides accurate detection of threats and their lateral movement. The alerts are based on engagement so the security team won't be chasing false positives and endless logs. The solution also uses dynamic deceptions to self-learn and match environments and will respin after attack to avoid attacker fingerprinting.
Third party integrations with major prevention, endpoint, SIEM devices automate incident response with automated blocking and quarantine saving security teams time and energy in quarantine and remediation.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



