ThreatMatrix Deception and Response Platform – Camouflage
Nominated in the Category:
Photo Gallery
 |

 |
ThreatMatrix Deception and Response Platform - Camouflage

Additional Info
| Company | Attivo Networks |
| Company size | 99 employees |
| Website | http://www.attivonetworks.com |
NOMINATION HIGHLIGHTS
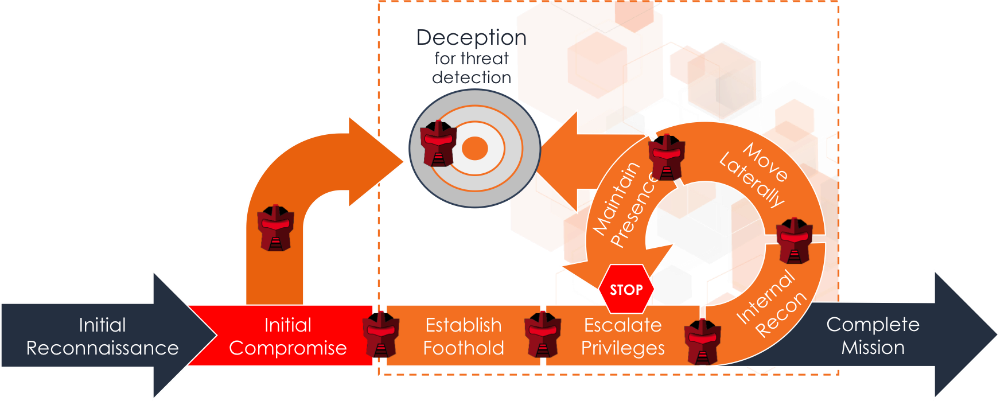
With the introduction of Camouflage, Attivo has moved its ThreatMatrix Deception and Response Platform into a new class of deception for threat detection and continuous threat management. Camouflage introduces machine self-learning into its algorithms for behavioral deception and deployment of its deception credentials and lures. Earlier versions of deception were based on using low to high interaction “honeypot” decoys to attract attackers. Attivo goes significantly further, by not only making the entire network a high interaction trap for attackers, but by also strategically deploying deception bait on end-points that is customized to match the production system and will dynamically self-learn the endpoint’s environment for the highest levels of authenticity. Do not be fooled that all deception is alike. Do you really think a ICS-SCADA environment looks the same as a medical network or a business network? No, of course not. Each environment runs different versions of operating systems, protocols, and services and mac addresses are very specific for the environment in which they are in. An attacker will study their attack surface and quickly identify and stay away from things that don’t look quite right.
Authenticity is core to the success of a deception solution. Low interaction or simple emulated environments can be detected by an attacker, whereas dynamic behavioral deception makes the bait and decoys indistinguishable to the attacker. Microsoft Active Directory support is also used for validation and additional deception. Additionally, the solution goes beyond just keeping a fresh façade and factors in fingerprinting after attacker engagement. The Camouflage solution will automatically respin the decoys and deception lures after attack to ensure the attacker cannot id and avoid the traps and detection in the future.
The solution is so stealthy, it’s now in high demand by blue penetration testing teams to trick the red teams and prove network resiliency.
How we are different
ThreatMatrix Platform is the most authentic, comprehensive, and scalable deception platform on the market and it is truly helping customers achieve visibility into in-network threats, attacker lateral movement, insider threats, and stolen credential attacks, all that are renowned for evading traditional security solutions. The platform provides the most comprehensive support for user networks, data centers, cloud, ICS-SCADA, IOT, POS environments
The solution provides the highest authenticity with cutting edge deception innovation that uses real operating systems, golden image customization, and dynamic behavioral deceptions for decoy and deception authenticity. This authentic use of decoys and deception lures sets the most attractive traps to lure in attackers and deceive them into revealing themselves.
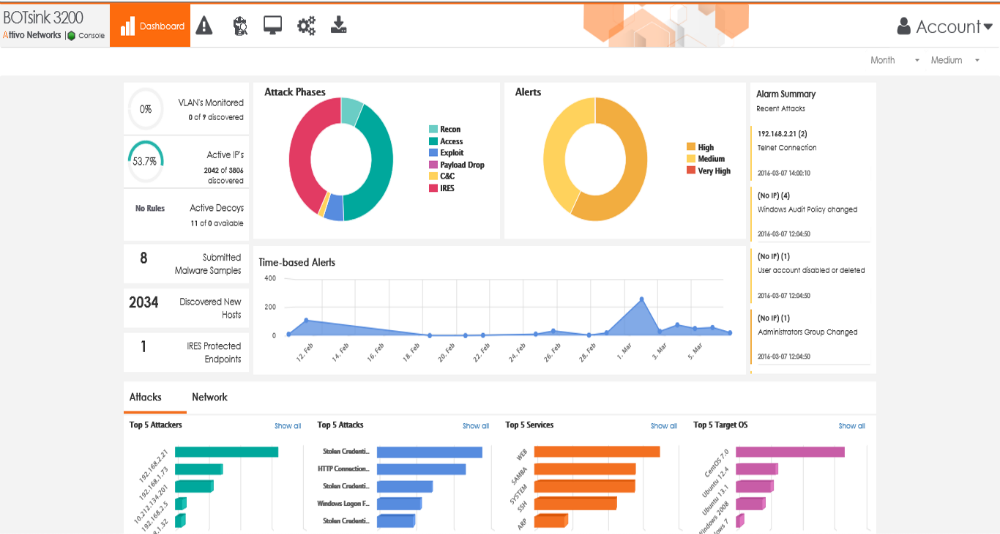
Upon engagement, attack analysis generates alerts that are engagement-based and substantiated with attack details – simplifying incident response and negating the need for additional resources to operate and respond to an incident. This attack information can be made available in forensic reports and/or be used for automated blocking and quarantine of attackers through 3rd party integration with firewall, NAC, end-point, SIEM vendors. Additionally, ThreatPath™ attack prevention reporting provides continuous visibility into a company’s vulnerabilities and weak links to help prevent attacker entry. Combined with attack time-lapsed replay, organizations can build a predictive and preventative security defense.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



