Photo Gallery
 |
|
ThreatX: Web Application and API Protection Platform


Additional Info
| Company | ThreatX |
| Company size | 50 - 99 employees |
| Website | https://www.threatx.com/ |
NOMINATION HIGHLIGHTS
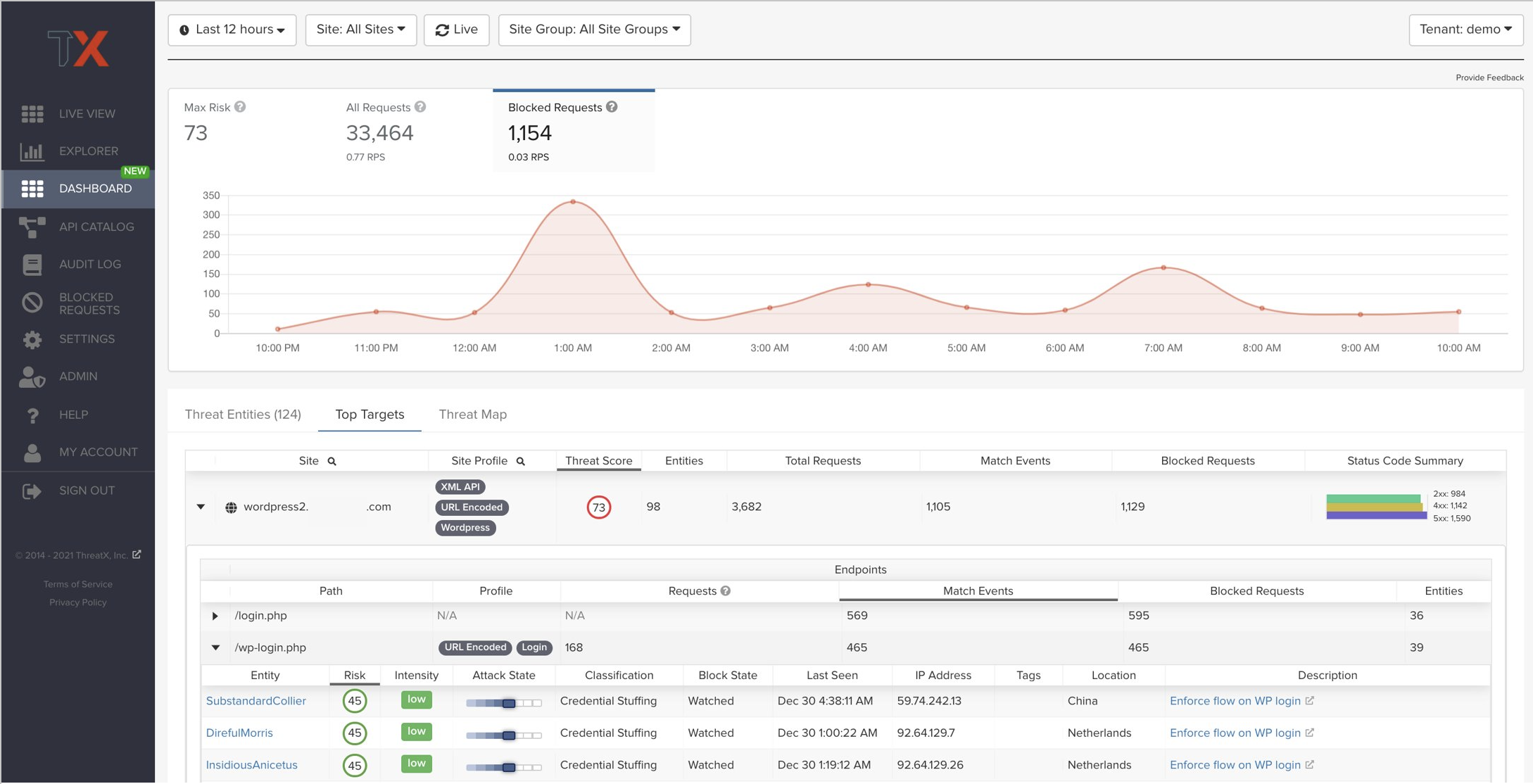
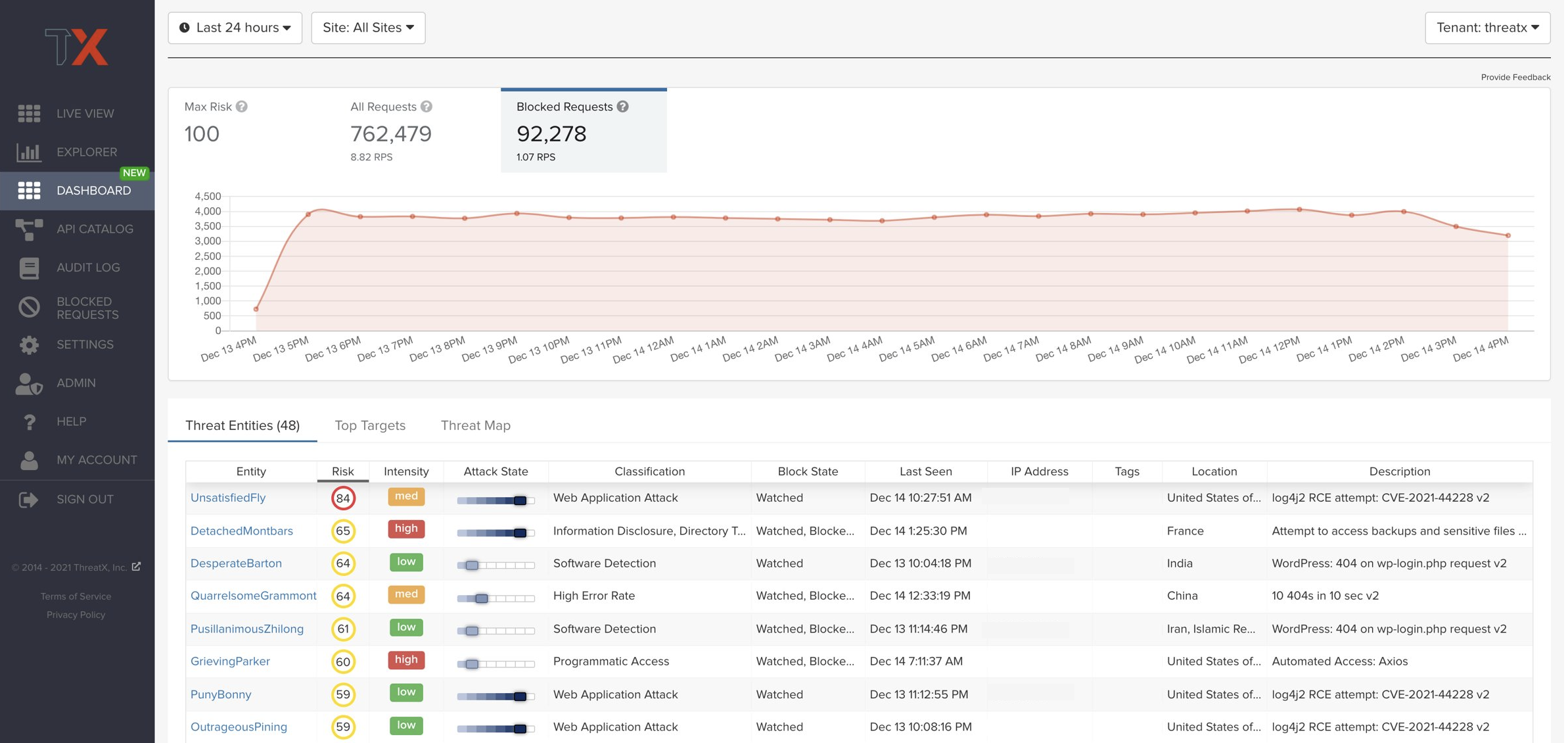
While APIs have quickly become the de facto building blocks of applications, they also introduce a sprawling attack surface with new and unique risks. In the past, all user experiences were predictably funneled through a single path of a WWW website. Today, that same website includes more advanced functionality and can be accessed from a variety of mobile devices, meaning it may expose dozens or hundreds of API calls. That proliferation of functionality means a proliferation of attack surface. Gartner Research predicts that “by 2022, API abuses will be the most-frequent attack vector resulting in data breaches for enterprise web applications.” Defense teams need something that helps simplify API security.
ThreatX’s API security enables customers to immediately protect all their APIs – both known and unknown – from all threats. By scrutinizing real traffic that hits APIs, ThreatX instantly protects rogue, zombie, and legitimate APIs. And unlike signature-based solutions, ThreatX protects APIs with its Attacker-Centric Behavioral Analytics that identifies and correlates attackers’ behavior across multiple attack vectors to more precisely identify threats – avoiding false positives that could unnecessarily block legitimate traffic or cripple an application’s functionality. Once your APIs are protected, you get API discovery, based on real traffic, that further defines your API attack surface, and the operational health of the endpoints backing your web applications.
Finally, all ThreatX customers have access to 24/7 Fully Managed AppSec Services that work hand in hand with security teams to streamline security operations, ensure continuous coverage, or simply free staff to work on other issues.
How we are different
ThreatX gives you instant API protection, for all your APIs, regardless of their status or which gateway they sit behind, no schema required. You’re protected without any discovery, integration, instrumenting of your code base, or talks with your dev teams.
ThreatX natively decodes and analyzes API traffic such as JSON and XML in order to identify any threats hidden within. This ensures teams can block injection attacks and other threats and exploits in the same way they do on the web front-end.
ThreatX can identify a variety of ways that attackers or bots may try to abuse exposed application or business logic. For example, ThreatX can identify if an entity is hitting password reset functionality without having visited the login page. Likewise, the solution can identify a spike in resource-intensive requests or an entity constantly refreshing inventory functionality, which could be a sign of an automated attack.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



