Photo Gallery

|


|
Titania Nipper Enterprise


Additional Info
| Company | Titania |
| Company size | 50 - 99 employees |
| World Region | Europe |
| Website | https://www.titania.com/ |
NOMINATION HIGHLIGHTS
Titania is uniquely positioned to help organisations move beyond perimeter-only defences, specialising in router, switch and firewall security for the entire network. Nipper Enterprise has been designed to assure continuous network security and compliance in real-time by automating an inside-out view of the network, and delivers fast, accurate visibility of configuration posture at scale, in accordance with vendor device-hardening best practices, Zero Trust segmentation, and control and risk management frameworks.
Network owners can use Nipper Enterprise to increase the coverage and cadence of assessments and gain immediate awareness of any device configuration changes, evidence continuous compliance with military and industry regulations, and minimize their attack surface via MITRE ATT&CK® misconfiguration prioritization.
Nipper Enterprise automatically prioritizes findings by security and/or compliance risk and provides remediation advice, by risk to shut down attack vectors, and device specific guidance on how to fix misconfigurations, decreasing remediation time.
This unique approach also means that Nipper Enterprise reports provide the evidence needed to assure compliance with security controls and risk management frameworks including DISA RMF, NIST SP 800-53/171, STIG, CMMC and PCI DSS 4.0. Recent editions of these mandated data security standards have also seen a shift towards a zero trust approach to network security. Annual and sampled vulnerability assessments are no longer fit for purpose, and RMFs advocate for continuous vulnerability monitoring – because devices that were deemed secure yesterday, might not be today.
Nipper Enterprise meets this demand as it has been scaled for the entire enterprise to deliver continuous misconfiguration and vulnerability detection and risk-prioritized remediation across every router, switch and firewall in the network on an up-to-hourly basis or as configurations change.
Key Capabilities / Features
Stateless and passive, Nipper Enterprise is a horizontally scalable and agentless web app which uses a set of containerized Nipper instances that scale up and automate the auditing of the configs of every network device, every day, and provides forward-thinking customers with the tools needed to implement continuous auditing, support their zero trust strategies and defend their network from preventable attacks.
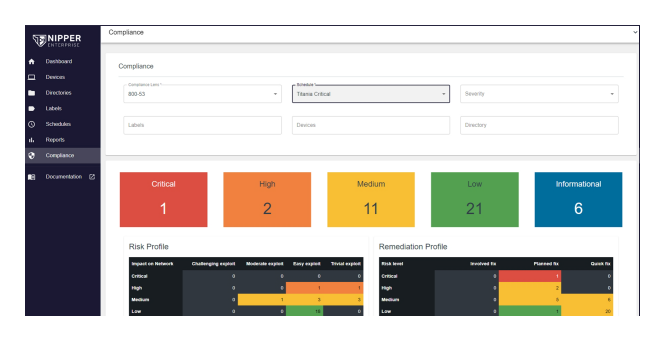
Nippers' software evaluates network device configurations against industry standards and best practices, providing detailed insights into the networks security posture network and highlighting deviations that could pose security risks. This continuous monitoring also ensure compliance with regulatory requirements such as DISA RMF, NIST 800-53/171, STIG, CMMC and PCI DSS 4.0.
A key capability of Nipper Enterprise is its ability to automatically generate detailed security and compliance reports summarizing a networks security results against mandated data security standards and requirements, identified vulnerabilities and recommended remediation actions. These reports automatically categorize vulnerabilities based on their severity and potential impact on the network and provide mitigating advice and exact technical fixes for each vulnerability. This allows security teams to prioritize remediation efforts efficiently, focusing on the most critical issues first and reducing overall risk exposure.
As mandated data security standards have shifted towards a zero trust approach to network security, Nipper Enterprise takes a proactive approach and offers continuous misconfiguration and vulnerability detection and risk-prioritized remediation across every router, switch and firewall in the network on an up-to-hourly basis or as configurations change, to detect newly introduced vulnerabilities promptly.
With Nipper Enterprise, customers can assess and assure security and compliance, even in offline networks, as the assessment methodology does not require direct access to devices.
How we are different
1. Nipper Enterprise boasts a unique approach to network security by emphasizing depth and granularity, with one of the standout features being its unparalleled level of inspection. While many competitors offer network security solutions that focus primarily on surface-level audits, Nipper Enterprise delves deeper into the configurations of network devices and provides detailed and context-rich insights into any found network vulnerabilities via customizable security and compliance reports. This thorough approach ensures that customers using Nipper Enterprise gain a comprehensive understanding of their network security posture, enabling them to identify and address potential risks before they can be exploited by malicious actors.
2. With Nipper Enterprise, customers can assure continuous security and compliance, even in offline networks, as the assessment methodology does not require direct access to devices. New or changed device configurations in the repository, trigger Nipper Enterprise to proactively fetch the latest (changed) configs for assessment. Nipper Enterprise provides SOCs and NOCs with the ability to proactively assess configuration changes between audits, providing additional layers of vulnerability analysis that highlight indicators of compromise, determine exposure to real-world threats (through MITRE ATT&CK dashboards) and guide threat hunting teams with historic security posture that informs incident response.
3. Nipper Enterprise distinguishes itself through its robust reporting capabilities. In addition to identifying vulnerabilities, Nipper software generates detailed security and compliance reports that provide actionable insights and recommendations for remediation. This unique approach to network security also means that the reports provide the evidence needed to assure compliance with security controls and risk management frameworks including DISA RMF, NIST SP 800-53/171, STIG, CMMC and PCI DSS 4.0. As a result, the findings reports are proven to offer unrivalled levels of accuracy which saves customers thousands of labour hours, and provide the granular detail needed to evidence compliance and/or provide remediation advice for detected


