Photo Gallery
 |
 |
Titania - Nipper Enterprise

Additional Info
| Company | Titania |
| Company size | 50 - 99 employees |
| World Region | Europe |
| Website | https://www.titania.com/ |
NOMINATION HIGHLIGHTS
There is growing recognition that to develop operational resilience against the current threat landscape, network security teams need visibility…
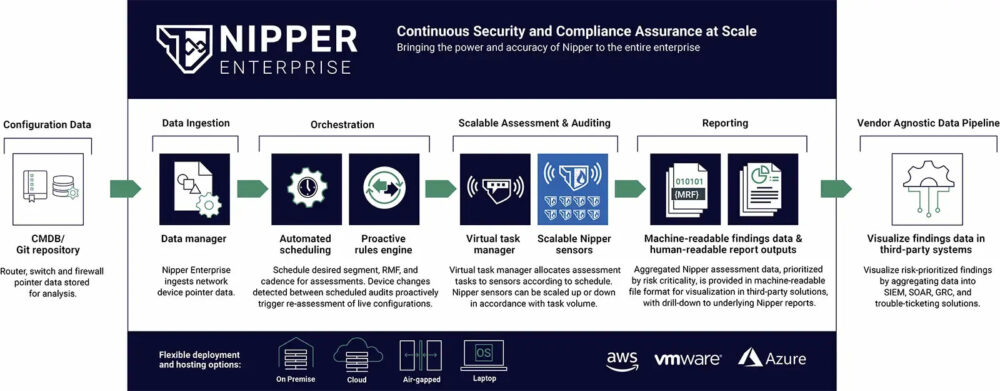
Nipper Enterprise assures continuous network security and compliance in near-real-time by automating an inside-out view of the network. The solution delivers fast, accurate visibility of configuration posture at scale, in accordance with vendor device-hardening best practices, Zero Trust segmentation, and control and risk management frameworks.
Organizations use Nipper Enterprise to increase the coverage and cadence of assessments and gain immediate awareness of any device configuration changes, evidence continuous compliance with regulatory frameworks, and minimize their attack surface with MITRE ATT&CK® misconfiguration prioritization.
The solution automatically prioritizes findings by security and/or compliance risk and provides remediation advice, by risk to shut down attack vectors, and device specific guidance on how to fix misconfigurations, decreasing remediation time.
Key Capabilities / Features
Nipper Enterprise customers with the tools they need to implement continuous auditing and defend their network from preventable attacks. The solution provides visibility of every configuration change on the network, in near-real-time, and can proactively assess those changes to determine network exposure risk.
By proactively monitor configuration drift, it also provides visibility of zero trust macro segmentation violations and vulnerabilities, automatically mapped to specific MITRE ATT&CK Tactics, Techniques and Procedures (TTP) and Known Exploited Vulnerabilities (KEVs), to inform business critical incident response and remediation strategies.
Nipper Enterprise allows customers to assess all devices and determine their security and/or compliance posture baseline. Assessments determine adherence to operational readiness and resilience standards (e.g. CORA and DORA), and report pass/fail compliance with PCI DSS, NIST, STIGs and CIS Benchmarks. These reports automatically categorize vulnerabilities based on their severity and potential impact on the network and provide mitigating advice and exact technical fixes for each vulnerability. This allows security teams to prioritize remediation efforts efficiently, focusing on the most critical issues first and reducing overall risk exposure.
How we are different
While many other network security solutions that focus primarily on surface-level audits, Nipper Enterprise delves deeper into the configurations of network devices and provides detailed and context-rich insights into any found network vulnerabilities through customizable security and compliance reports. This in-depth approach ensures that customers gain a comprehensive understanding of their network security posture, enabling them to take a proactive approach, identifying and address potential risks before they can be exploited by malicious actors.
Nipper Enterprise enables customers can assure continuous network security and compliance in offline networks, as the assessment methodology does not require direct access to devices. New or changed device configurations in the repository, trigger Nipper Enterprise to proactively fetch the latest (changed) configs for assessment.
Analyst house Omdia notes that Nipper Enterprise “adds a level of proactive security risk assessment and vulnerability management, which complements nicely the kind of server centric vulnerability assessment enabled by the likes of Qualys and Tenable.” Its findings reports are proven to offer unrivalled levels of accuracy, saving thousands of labour hours, and providing the granular detail needed to remediate vulnerabilities and evidence compliance with national cybersecurity directives and regulatory standards.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



