Vendor Email Compromise: THE threat of 2021
Photo Gallery
 |
 |
Vendor Email Compromise: THE threat of 2021

Additional Info
| Company | Agari |
| Website | https://www.agari.com/ |
| Company size (employees) | 100 to 499 |
| Type of solution | Cloud/SaaS |
Overview
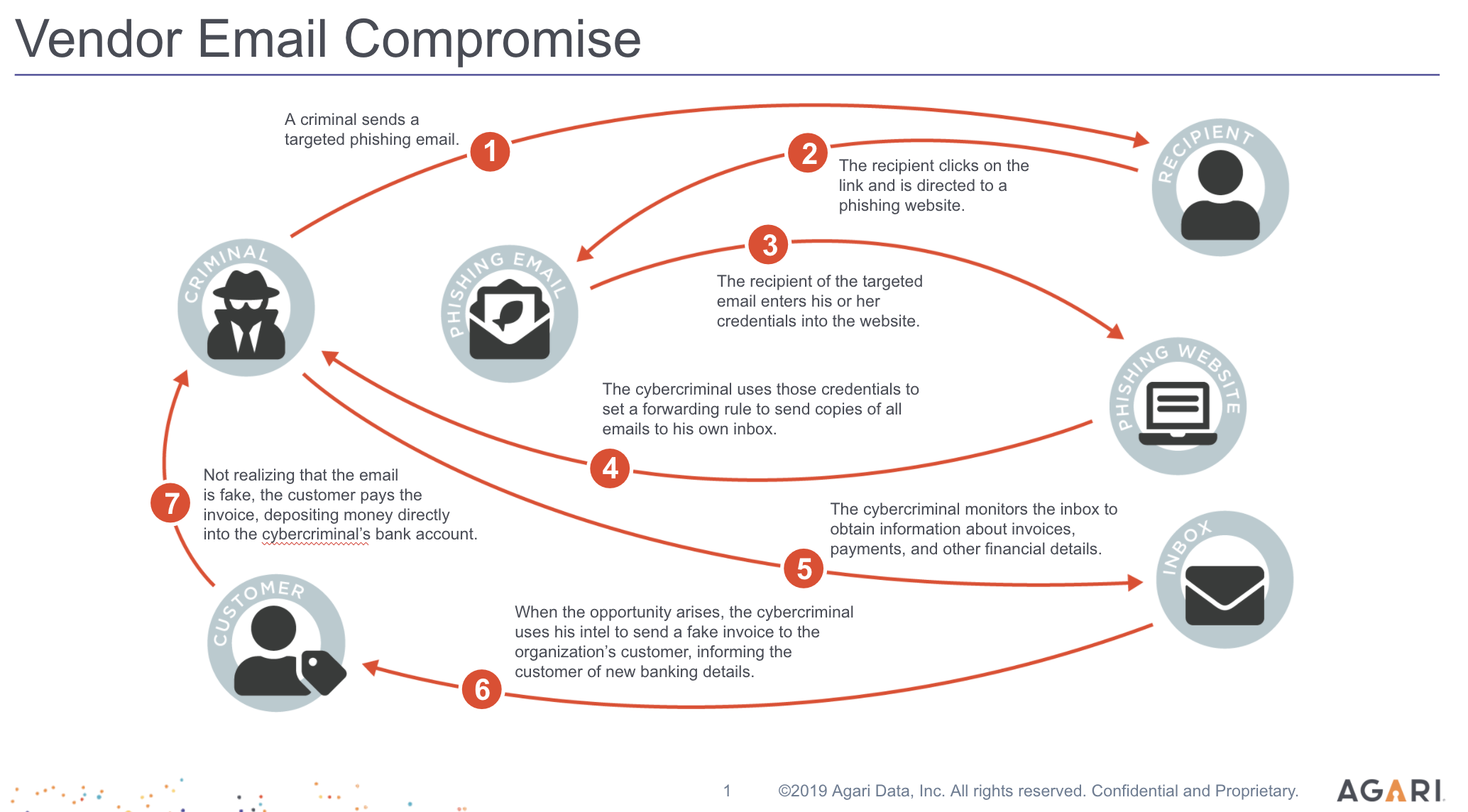
Vendor Email Compromise (VEC) spreads from one business to others like a contagion across the extended enterprise. Well-funded, organized cybercriminal rings use hijacked business email accounts and social-engineering tactics to gather insider information that is then used to create meticulously crafted and timed attacks between vendors and customers and among vendors. In this way, supply chain partners inherit risk from each other as employees are tricked into performing seemingly innocuous, but harmful actions. VEC attacks originate from legitimate email accounts that have been hijacked. Messages pass domain authentication and sail right through whitelists and other security controls.
On visual inspection, even highly trained security experts can’t spot VEC, and VEC contains highly-convincing business and personal details.
Agari Phishing Defense(TM) detects these rapidly evolving VEC attacks and can prevent them from reaching employee inboxes through policy-based, automated forensic analysis that understands the identity behind the email message. The first step in preventing a VEC attack is detecting compromised business email accounts. Agari Phishing Defense inspects incoming email messages, but also messages flowing from employee-to-employee across the organization for indicators of compromise. Agari Phishing Defense’s unique approach can detect fraudulent messages originating from legitimate email accounts.
Agari Cyber Intelligence Division (ACID) discovered and coined the term: Vendor Email Compromise based on its threat hunting efforts that uncovered cybercriminal gang, Silent Starling (This is the codename ACID gave the group; it isn’t their real name.). Silent Starling is a new group comprised of Nigerian cybercriminals, intent on scamming as much as they can from their victims through VEC.
How we are different
1. Agari's counterintelligence division ACID discovered globally cybercriminal groups using Vendor Email Compromise (VEC), and ACID coined the term.
2. Agari Phishing Defense(TM) protects enterprises from VEC, because it is the only anti-phishing product that uses machine learning to identify “good” email message sender to “good” email message receiver relationships. Agari Phishing Defense not only provides outstanding email security, it reduces the effort that the CISO organization has to exert to have world-class email security. Agari Phishing Defense is known for reducing the risk of companies leaking sensitive company or customer information, inappropriately transferring money out of the company, or social engineered attacks being successful. These are achieved while the IT security department spends less time on email security. Employees are able to focus on other risk areas and customers can typically avoid additional hires.
3. Agari Phishing Defense delivers results one-third faster than competitive solutions. Faster deployment means that better security is in place sooner and deployment costs are lower. Finally without Agari Phishing Defense, customers often need to roll out a full threat intelligence program. Agari Phishing Defense streamlines and automates threat detection management, which means that its customers don’t have to roll out a full threat intelligence program, including integrating threat data from multiple sources, saving customers time and money. Agari Phishing Defense continuously protects against VEC threats leveraging the only cyber intelligence-sharing network that provides human-vetted threat intelligence from the world’s top Security Operations Centers and human-vetted threat intel sourced from world-renowned BEC experts (ACID).



