Photo Gallery
 |
 |
Viettel Cyber Security Penetration Testing


Additional Info
| Company | Viettel Cyber Security Company |
| Company size | 100 - 499 employees |
| Website | https://viettelcybersecurity.com/ |
NOMINATION HIGHLIGHTS
Viettel Cyber Security is a branch of Viettel Group – The largest telecommunications group in Vietnam with over 111 million customers in 11 nations, developing information security solutions and providing information security services for domestic and foreign organizations and enterprises.
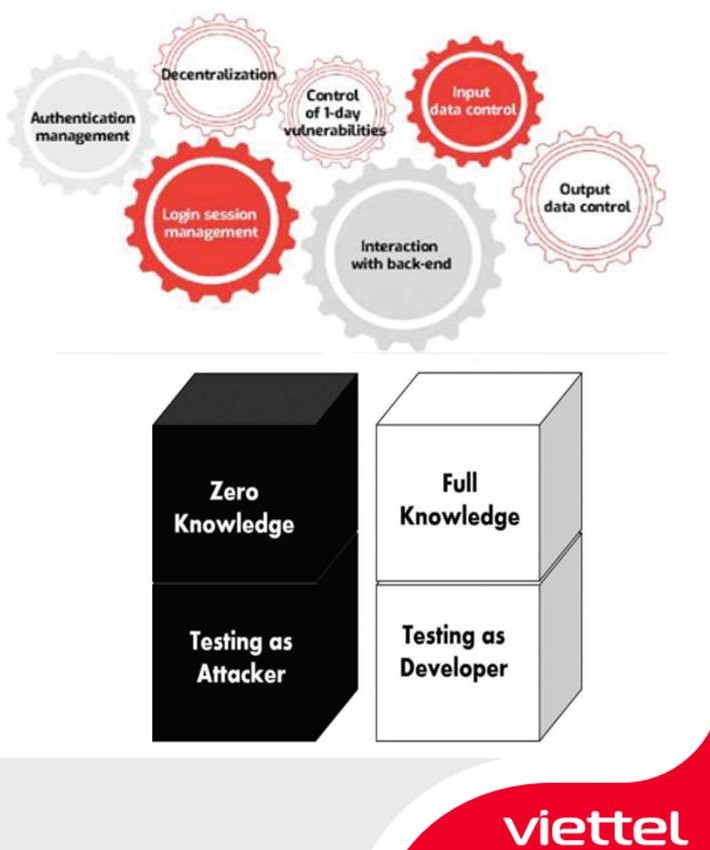
In 2011, Viettel Cyber Security first introduced Pentration Testing Services which is a form of testing whether clients’ IT systems can be attacked by playing as hackers and simulating attacks on clients’ systems. During its operations, VCS has researched and owned 300 zero-day vulnerabilities on various application platforms such as Microsoſt, Zimbra, Facebook, Paypal, etc. We investigate and respond to numerous attacks from big APT group in the world such as: MgBot, Cobalt, Turla Group, APT29, APT32, Winnti, Mofang, Lotus Panda …
Our Pentest Service methodology is the combination of: Description of vulnerabilities in the list of Top 10 OWASP; A checklist of vulnerability based on Next-gen pentest procedure; Bugcrowd’s Vulnerability Rating Taxonomy (World #1 crowdsourced security platform). Regarding client’s request, Pentesting team use a variety of tools such as Nmap, Dirb, Burspuite Pro, Viettel 1day scanner, especially Viettel Threat Intelligence, an in-house development tool, a big data source providing Intelligence about all kinds of cyber threats and Viettel 1-day scanner. We build a list of exploitation codes, package into a single tool to automatically scan, detect vulnerabilities and exploit.
Thanks to important results in detecting vulnerabilities of globally popular applications, VCS has been recognized as an excellent unit in the field of Information Security Audit, Supervision and Assurance. Over the 10-year period, we provided services for Viettel Group, Government bodies, Ministries, large enterprises and SMEs in various industries such as Telecommunication, e-commerce, …, large telecom companies in Africa such as Natcom (Haiti), Movitel (Mozambique), Halotel (Tanzania)…
How we are different
• Skilled ethical hackers
At Viettel Cyber Security, we are proud of our skilled ethical hackers are trained to replicate the mind of a malicious attacker and use an exhaustive set of tools to perform and imitate this mindset. VCS’s staff and experts have made constant efforts in the process of research and development of the most optimal products for clients’ information security across the country and other regional clients. During its operations, Viettel has researched and owned 300 zero-day vulnerabilities on various application platforms such as: Microsoft, Zimbra, Facebook, Paypal, etc. Our In-house project execution team has internationally recognized qualifications such as Winners of Pwn2Own Vancouver 2021, Tokyo 2020; Top 5 of BugCrowd researchers; Top 30 in Microsoft’s MSRC Most Valuable Security Researchers 2019-2021 and more.
• Top Pentesting Tools:
Viettel Pentesting team use a variety of tools such as Nmap, Dirb, Burspuite Pro, Viettel 1day scanner and checklist during the whole process, especially Viettel Threat Intelligence, an in-house development, a big data source providing Intelligence about all kinds of cyber threats and Viettel 1-day scanner. We build a list of exploitation code, package into a single tool to help automatically scan, detect vulnerabilities, even in some cases, automatically exploit. All of these tools will help implement efficiently and accurately in pen-testing process.
• Effective Procedure: We offer the pen testing process broken down into the following steps: Client sends audit request; audit plan; audit environment; performs audit; send audit results and remedies guidelines for detected vulnerabilities; Client takes remedies as guided and sends re-audit request. The process is completed and double checked by QA team until the audit results and assessment of remediation no longer contain errors. It is also recorded and captured for reporting when completing. The client can participate in the process to monitor and follow the whole

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



