Photo Gallery

|
|
Viettel Vulnerability Space

Additional Info
| Company | Viettel Cyber Security Company |
| Company size | 100 - 499 employees |
| World Region | Asia |
| Website | https://viettelcybersecurity.com/ |
NOMINATION HIGHLIGHTS
Viettel Vulnerability Space is a solution that allows periodically identifying, classifying, prioritizing and minimizing security vulnerabilities of software versions on PC, Server, etc. to support security management and monitoring process on the client network.
• Provide a way to support the integration of information from popular Vulnerability Scanner systems, thus improving the ability to identify vulnerabilities and taking advantage of client’s available resources.
• Provide integration with many popular Threat Intelligence, CVE Database with the aim to quickly identify and react to new threats appearing on the Internet.
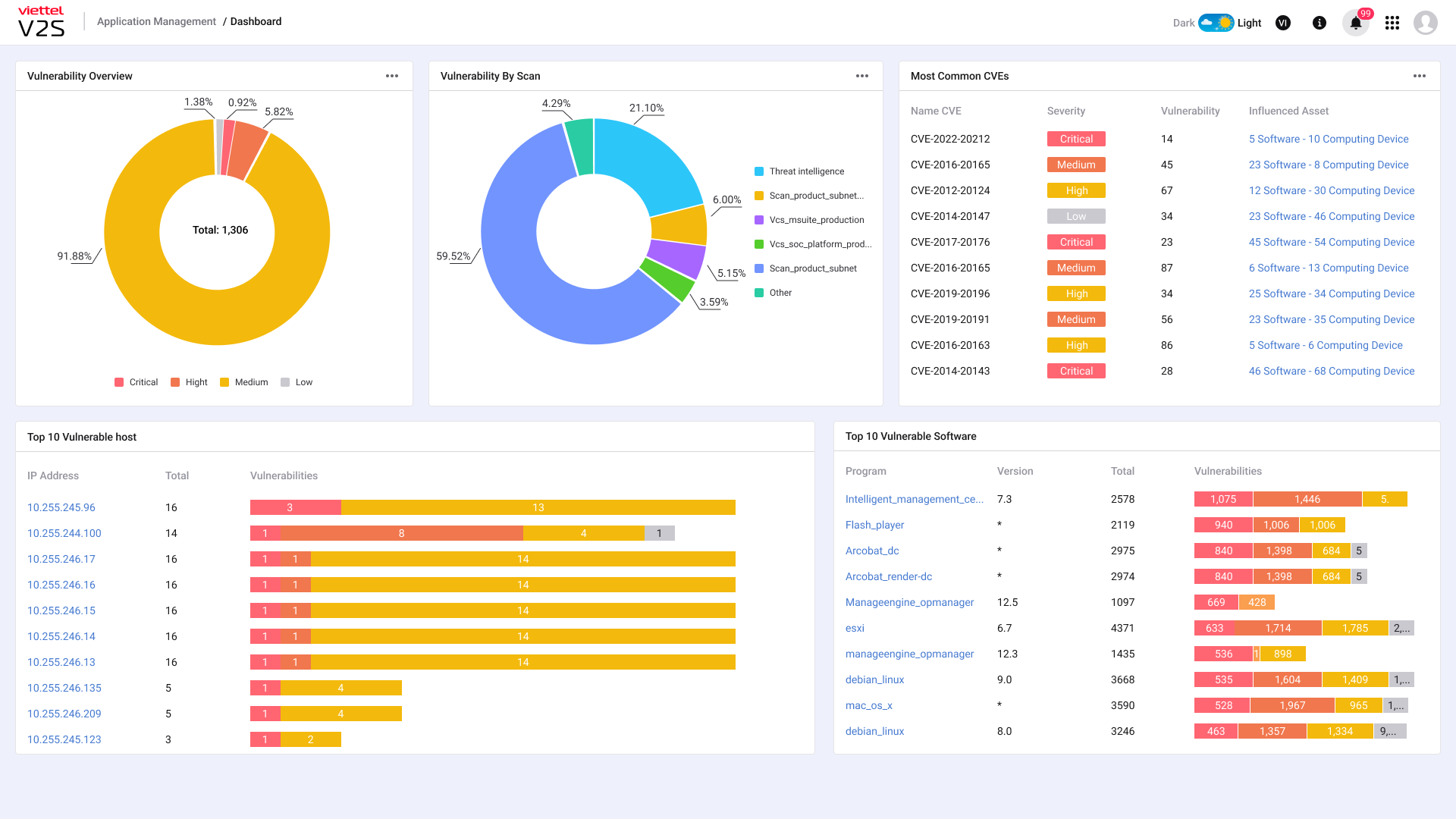
• Periodically review and identify vulnerabilities and threats on the network. Provide an overview of them in the client’s network.
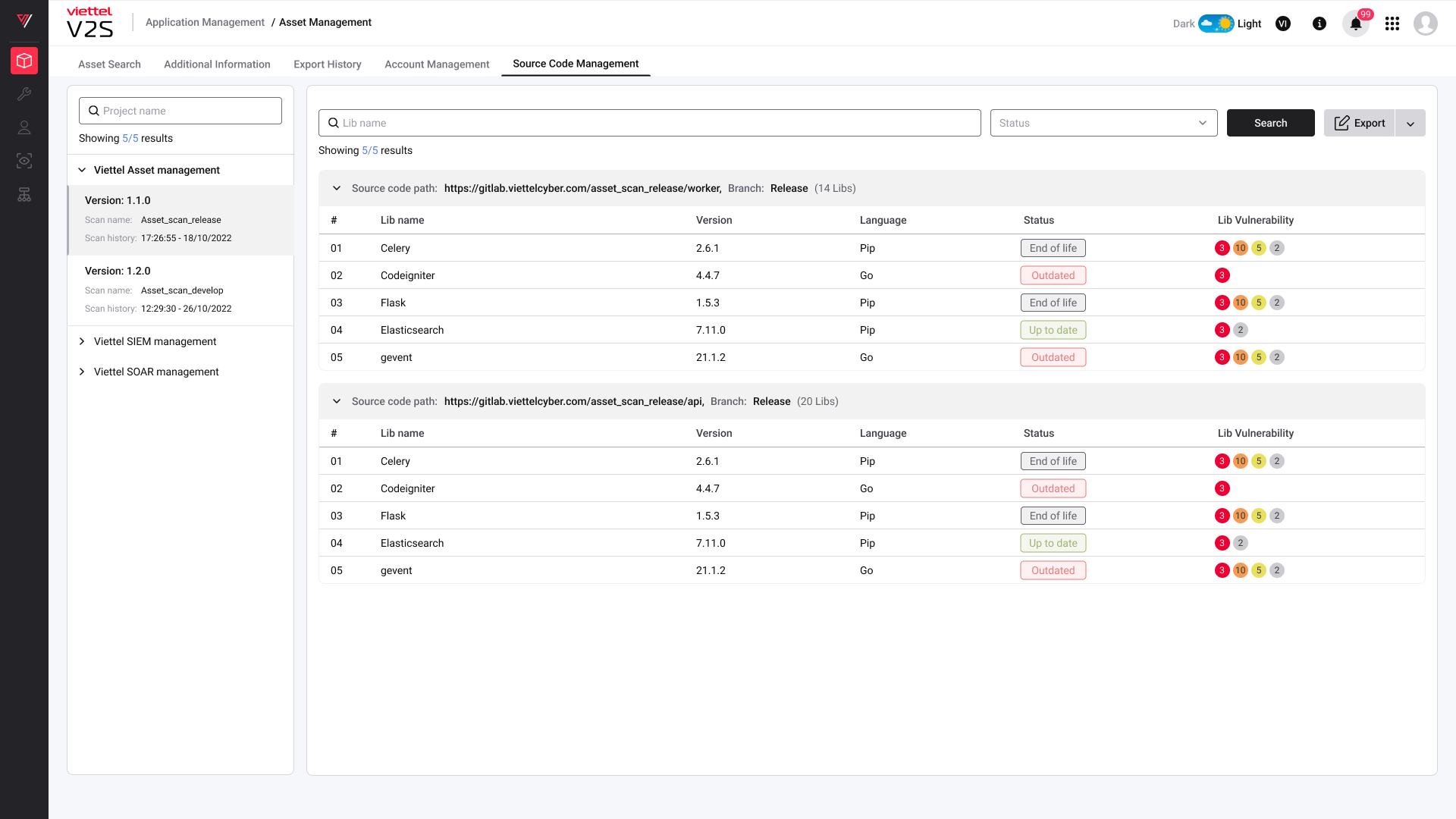
• Identify vulnerabilities in dependency and library used in self-developed products, support early vulnerabilities detection from the development environment and reduce information security risks when the product is deployed.
• Push alerts of high-level risks and vulnerabilities on computers to 3rd party ticket operation flows.
• Provide customized process to verify vulnerability information and improve alert accuracy for operation and handling.
How we are different
• Professional vulnerability management process: Viettel Vulnerability Space builds on a professional vulnerability management process from identifying, classifying, severity rating and actual exploits testing based on cybersecurity expert knowledge, as well as integrating ticketing systems. Providing organizations an overview of vulnerabilities across IT environments such as endpoints, network, etc. and servers from the time of discovery to the time they are handled, Viettel Vulnerability Space prioritize risks and address vulnerabilities as quickly as possible, thus reducing the operational load for vulnerability handling by up to 50%.
• Outstanding integration capabilities:
+ Automatic integrate Asset information from systems according to various standards such as API, AD, DNS, etc.
+ Automatically discover Shadow Assets based on log traffic, Network Protocol,etc. thus improving Asset coverage, as a basis for giving an overview of vulnerabilities across network.
+ Synthesize centralized vulnerability database knowledge with more than 200K vulnerabilities from NVD, 180K vulnerabilities from Viettel Threat Intelligence, 180K vulnerabilities from github advisories and many other vulnerability sources around the world.
+ Configure integration of popular Vulnerability Scanners in the world like Nessus, Nexpose, Acunetix, etc. to improve the ability to identify vulnerabilities across network from different perspectives, taking advantage of available knowledge from the world's leading Vulnerability Scanner developers.
• Ability to response quickly when vulnerabilities arise: Automatically scan software versions installed on devices when there is early warning from the Threat Intelligence system, giving the exact device that is installing software with version affected by security vulnerabilities, speed up response to critical new vulnerabilities, reducing manual vulnerability scanning efforts.


