Photo Gallery
 |
|
|
VMware Carbon Black Cloud

Additional Info
| Company | VMware |
| Company size | 10,000 or more employees |
| World Region | North America |
| Website | https://www.vmware.com/ |
NOMINATION HIGHLIGHTS
According to VMware’s 2022 Global Incident Response Threat Report, 57% of respondents have encountered ransomware attacks in the past 12 months. VMware Carbon Black Cloud offers a number of ways to protect against ransomware in real-time. These methods provide visibility into, detection of, and blocking of ransomware attacks along the kill chain, including monitoring for malicious signatures, advanced detections, machine learning, and behavioral analysis.
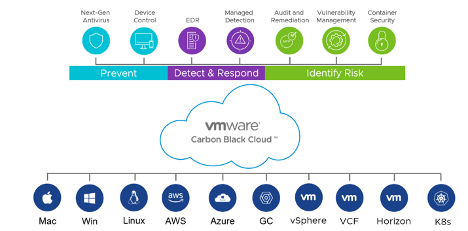
VMware Carbon Black Cloud provides all these capabilities with a single, lightweight endpoint sensor and a single console UI without scheduled scans by monitoring the activity of all binary executions in real-time. VMware Carbon Black Cloud detects and blocks ransomware and other more advanced attacks without impacting the performance of the endpoint. With VMware Carbon Black Cloud, organizations maintain visibility, protection and control over their employees’ endpoints, even if they are disconnected from the corporate network.
VMware Carbon Black Cloud consolidates multiple endpoint security capabilities (NGAV, EDR, IR, threat hunting, etc.) so that infrastructure and security teams can operate faster and more effectively using a shared source of truth. By leveraging the cloud, VMware Carbon Black makes cybersecurity easier for defenders (and harder for attackers) by introducing things like auto-scaling, continuous deployment, and cascading software patch rollouts.
VMware Carbon Black Cloud is powered by VMware Contexa, a full-fidelity threat intelligence cloud. As new adversarial techniques emerge, VMware Contexa recursively identifies historic triggers, builds detection and prevention logic based on your environment, and deploys enforcement without the need for any administrative action, which accelerates resolution when you encounter indicators of compromise. VMware Contexa currently identifies active network exploits at a daily rate of 80,000 exploits, including Log4Shell and other moderate to critical exploits. Each day, nearly 2 million files are further analyzed, resulting in more than 1 million ransomware attack preventions every 90 days.
How we are different
● High-fidelity, behavior-based detections: VMware Carbon Black Cloud integrates with the Microsoft Antimalware Scan Interface (AMSI) to leverage high-fidelity, behavior-based detections created by the VMware Threat Analysis Unit to block ransomware in its tracks by detecting the exploit kits commonly used by strains of ransomware, such as Cobalt Strike, PowerShell Empire, and Metasploit. By detecting these exploit kits, VMware Carbon Black Cloud can shut down the ransomware attack before it is able to do any damage.
● Machine learning technology: VMware Carbon Black Cloud uses machine learning to conduct static analysis of the binary to determine if it is suspected to be malware. This static analysis looks at the metadata embedded in the binary as well as human-readable strings for indicators that it is malicious. If the binary is judged to be suspected malware, it can be blocked through policy.
● Deletion of known malware: VMware Carbon Black Cloud can automatically delete known malware in a configurable window of one day to four months. This known malware will not be allowed to execute before it is deleted according to policy. This window is to help security teams ensure that false positives are not being deleted. VMware Carbon Black Cloud classifies malicious activity by MITRE ATT&CK technique IDs (TIDs). It also generates an alert visualization to help quickly understand the scope of the attack, establish the root cause, and prioritize response.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



