Photo Gallery
|
VMware Contexa: Cloud-Delivered Threat Intelligence

Additional Info
| Company | VMware |
| Company size | 10,000 or more employees |
| World Region | North America |
| Website | http://www.vmware.com |
NOMINATION HIGHLIGHTS
Cyber threats and attacks are rising at a rapid pace, and they continue to get more complex. The gap between bad actors and good defenders is growing as organizations struggle to keep up with an increasing number of sophisticated attacks. In fact, VMware’s Global Incident Response Threat Report found that lateral movement, which refers to a threat actor’s ability to move across different parts of a target organization’s environment, was seen in 25% of all attacks. Furthermore, with sophisticated attacks, lateral movements will be seen almost all of the time.
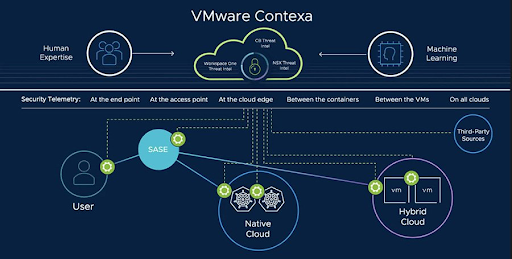
VMware Contexa is a full-fidelity cloud-delivered security intelligence that’s built into VMware’s security products. It improves security on networks and endpoints within workloads and modern applications built on containers. Contexa powers VMware Security to stop threats by discovering vulnerabilities, detecting threats, and quashing lateral movement. With access to the full breadth of network and endpoint technologies, the intelligence cloud is able to observe and evaluate every process running on an endpoint and every packet crossing the network. It’s then able to share its analysis with other security analysts and systems, allowing for the quickest, up-to-date decisions to be made constantly.
The technology processes data to produce threat intelligence based on the inner workings of applications and networks. With automated analysis and investigations, human intelligence is able to be applied exactly when and where it is needed. VMware Contexa strikes a balance between humans and technology by blending automated signal collection and analysis with human intelligence.
Enterprises of all sizes rely on VMware Security and Contexa to protect users, endpoints, networks, and workloads. Each day, protected organizations benefit from the billions of security events and network flows that Contexa processes.
How we are different
VMware Contexa has full visibility into threats, providing lateral security. Contexa sees every single lateral hop of an attack across endpoints, workloads, and networks. This unique visibility reveals not just the connection but the entire conversation. The pioneers of modern virtualization now protect VMs like no other—and provide innovative protection for modern applications.
VMware Contexa collects and processes more than 1.5 trillion endpoint events and 10 billion network flows each day, revealing approximately 2.2 billion suspicious behaviors daily. The data is analyzed by machine learning technology as well as by more than 500 human researchers. No other threat intelligence cloud analyzes as massive and complete a footprint of telemetry to stop today’s threats.
Contexa leverages full-fidelity data, applies analytics in-context, and then VMware Security enforces automated action at control points. VMware Contexa establishes intelligence by taking in information from a variety of systems and sources and building a shareable context. Such intelligence can expose threat actors moving within new distributed attack chains and be used to halt them. Contexa receives data from and shares analysis with other systems. This enables security analysts and security engineers to make intelligent decisions—delegating some of those decisions to machines. In October 2022, VMware’s Threat Analysis Unit (TAU) released a report about Emotet malware’s supply chain. Even after a coordinated takedown in early 2021, Emotet reemerged as a global threat, changing its command and control infrastructure rapidly and adapting accordingly. Using VMware Contexa, the TAU was able to observe and investigate waves of new Emotet attacks. The technology works with distributed control points within user endpoints, virtual machines, containers, and runtimes. Combining Contexa’s machine automation with the TAU’s human intelligence, the team was able to build a robust defense against Emotet’s resurgence, as well as other malware strains and threats.


