Photo Gallery
 |
|
|
VMware NSX Network Detection and Response

Additional Info
| Company | VMware |
| Company size | 10,000 or more employees |
| World Region | North America |
| Website | https://www.vmware.com/ |
NOMINATION HIGHLIGHTS
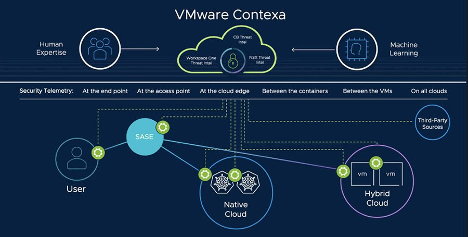
The patented NSX Sandbox deconstructs every behavior engineered into a file or URL to determine if it is malicious. It sees all instructions a program executes, all memory content, and all operating system activity. The VMware Threat Analysis Unit continuously updates VMware NSX NDR in real-time with threat intelligence, such as active command and control (C&C) servers, objects with zero-day exploits, toxic websites, and malware distribution points, and malware information useful to defend against threats specific to organizations.
SOC teams are overwhelmed by the high volume of low-fidelity alerts generated by security controls. The unique combination of AI-powered NTA, IDS/IPS, and network sandboxing slashes false positives by up to 90 percent and provides unmatched visibility. Massive amounts of network data down are condensed down to just a handful of intrusions, meaning analysts can spend time solving real incidents. rather than chasing false positives.
In one case, a Global Fortune 1000 Company in the financial services industry was having problems stopping advanced threats that bypass existing perimeter security controls. After deploying NSX Network Detection and Response in blocking mode, the company was able to stop malicious web traffic and email content before they entered the global network. NSX also provided this company with unparalleled visibility into the complete series of intrusions that cover the MITRE ATT&CK techniques. For example, NSX allowed the firm to see every stage within any given attack—whether a user clicked on the email or executed the attachment, what happened after the attachment was executed, whether the compromised host established communication with an external host, whether the attack involved additional accounts or hosts, and which datasets were accessed. The security team at this firm values the flexibility and scalability that NSX Network Detection and Response offers.
How we are different
The patented NSX Sandbox deconstructs every behavior engineered into a file or URL to determine if it is malicious. It sees all instructions a program executes, all memory content, and all operating system activity. The VMware Threat Analysis Unit continuously updates VMware NSX NDR in real-time with threat intelligence, such as active command and control (C&C) servers, objects with zero-day exploits, toxic websites, and malware distribution points, and malware information useful to defend against threats specific to organizations.
SOC teams are overwhelmed by the high volume of low-fidelity alerts generated by security controls. The unique combination of AI-powered NTA, IDS/IPS, and network sandboxing slashes false positives by up to 90 percent and provides unmatched visibility. Massive amounts of network data down are condensed down to just a handful of intrusions, meaning analysts can spend time solving real incidents. rather than chasing false positives.
In one case, a Global Fortune 1000 Company in the financial services industry was having problems stopping advanced threats that bypass existing perimeter security controls. After deploying NSX Network Detection and Response in blocking mode, the company was able to stop malicious web traffic and email content before they entered the global network. NSX also provided this company with unparalleled visibility into the complete series of intrusions that cover the MITRE ATT&CK techniques. For example, NSX allowed the firm to see every stage within any given attack—whether a user clicked on the email or executed the attachment, what happened after the attachment was executed, whether the compromised host established communication with an external host, whether the attack involved additional accounts or hosts, and which datasets were accessed. The security team at this firm values the flexibility and scalability that NSX Network Detection and Response offers.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



