Photo Gallery
 |

 |
Wallarm Integrated API and Application Security Platform


Additional Info
| Company | Wallarm |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://www.wallarm.com/ |
NOMINATION HIGHLIGHTS
The applications driving modern enterprises are increasingly under attack and APIs make up one of the most exploited attack vectors. Traditional application security solutions are either too narrow in focus or lack critical capabilities for deployment, integration and protection of APIs. Wallarm delivers integrated API and application security, providing unified API threat prevention, API discovery and risk management, and API security testing with next-gen WAAP capabilities. Wallarm can be deployed across on-prem, cloud and hybrid environments and allows customers to simplify their API security stack to achieve better protection in a highly scalable, easy-to-deploy and operate solution.
Wallarm specializes in protecting the APIs connecting the digital assets that are the lifeblood of modern industry. We deliver integrated, continuous API and application security in a unified, highly scalable, easy-to-use platform. Automated discovery, protection, response and testing for your APIs and applications are delivered in a single solution to help secure every digital transaction, in any environment, at any scale. Detailed insights into API and application security threats aid better cybersecurity decision-making and support adherence to regulatory standards. Rapid implementation and deployment flexibility combined with a comprehensive, scalable solution help you address current and emerging security challenges and protect the applications and digital assets driving your business.
Key Capabilities / Features
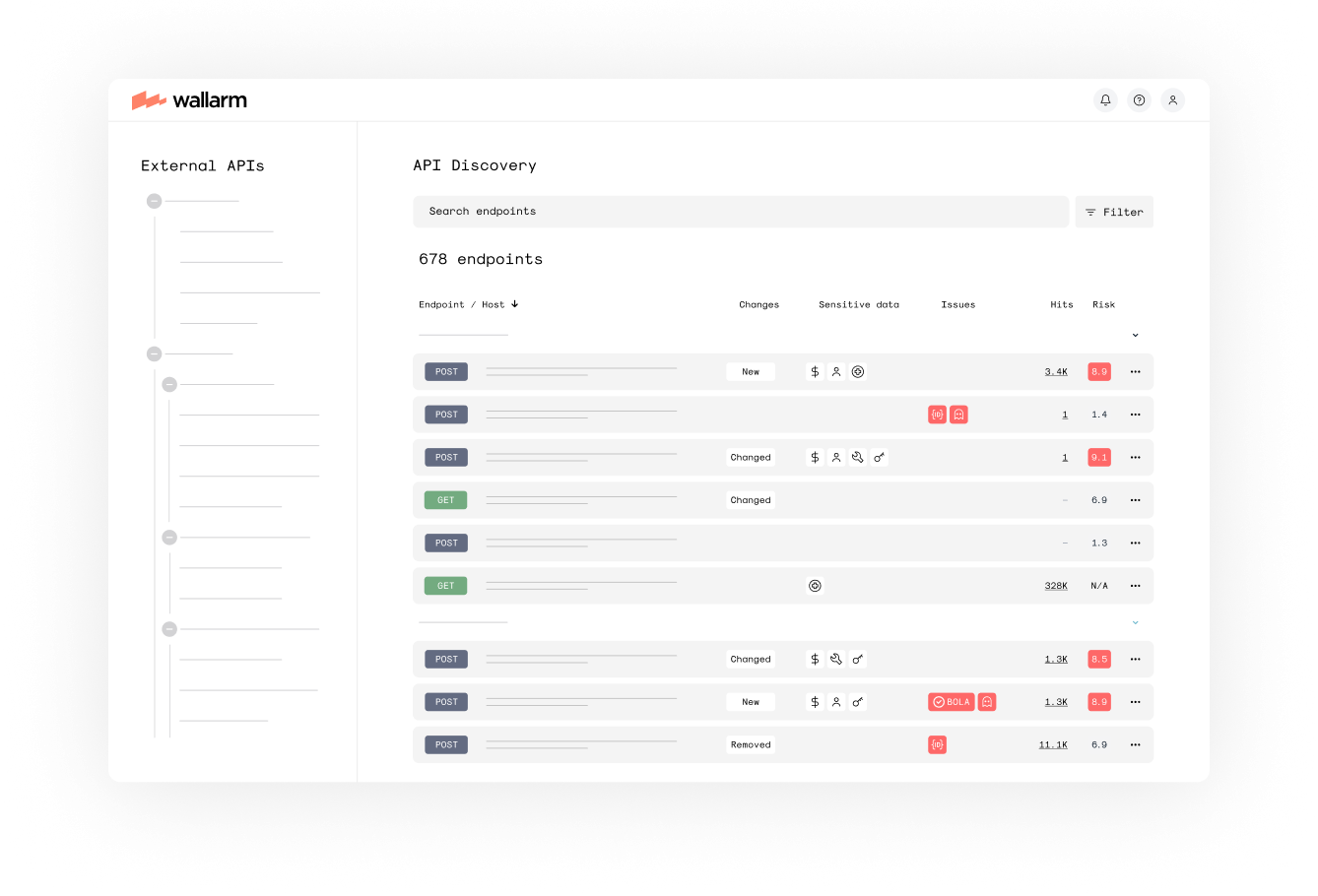
Discover
Wallarm automatically discovers and assesses your API attack surface, using detailed traffic analysis to create a complete inventory of API endpoints. The platform identifies parameters that potentially expose sensitive data and provides a risk score for every endpoint. Wallarm evaluates and catalogs API risk, with details necessary to identify and fortify API security. Wallarm monitors your entire API portfolio to detect new, changed, and rogue APIs, as well as drift from approved specs to improve control and minimize security coverage gaps. Wallarm actively tracks risky API endpoints, including those handling sensitive data like PII, to prioritize security activities and prevent costly breaches and compliance violations.
Protect
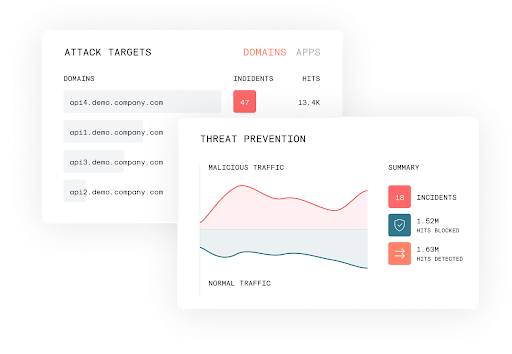
Wallarm delivers fully integrated, cloud-native next generation protection capabilities to secure your entire API and application estate in a single, unified solution. The platform delivers advanced protection against emerging threats, including the OWASP Top 10, OWASP API Top 10, malicious bots, layer 7 DDoS, account takeovers (ATOs), 0-day exploits and other threats. Automated, grammar-based rules minimize dependence on manual Regex and help eliminate false positives to boost operating efficiencies. Wallarm works with native integrations, webhooks, and APIs to leverage existing DevOps and security tools, for better security and faster time-to-value.
Respond
Wallarm provides detailed data with extensive search and filtering capabilities for rapid response to API and application attacks. Customers can respond automatically or manually with specific remediation actions such as blocking attacks, blocking or graylisting IP addresses, targeted rate limiting, and creating virtual patches. Customers can further tailor responses and notifications with condition-specific triggers.
Test
Wallarm provides testing capabilities to reduce API and application risk sooner. Active and passive vulnerability scans identify vulnerabilities for remediation, while Active Threat Verification can use production attack traffic to test non-production environments. Customers can test APIs for vulnerabilities using an OpenAPI specification or Wallarm’s discovery data.
How we are different
Wider breadth of capabilities. Wallarm provides inline and out-of-band protection for APIs and applications, including API discovery, API threat protection, and more in a single, integrated platform. This allows customers to lower acquisition and deployment costs and operating overhead, improve time-to-value, and execute a more effective, consolidated approach to API and application security. Inline protection is optimized for performance, providing real-time active threat protection with minimal impact on latency.
Comprehensive API protocol support: Wallarm supports legacy and modern API protocols, which is critical for most organizations, which have a mix of APIs and applications. Wallarm not only supports the APIs that they have deployed today, the platform is designed to adapt quickly to support new API protocols as they are deployed in the future.
Deployment flexibility: A great tool is useless if it doesn't work in your environment. Wallarm provides broad support for customer environments of all types, including deployments with cloud providers, on-premise, across different kinds of infrastructure, integrated with API gateways, and more. Wallarm delivers the comprehensive API and application protection that customers need, while adapting to the environment that they already have in place.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



