Photo Gallery
 |

 |
Zentera Systems' CoIP Access Platform


Additional Info
| Company | Zentera Systems, Inc. |
| Company size | 10 - 49 employees |
| Website | http://www.zentera.net |
NOMINATION HIGHLIGHTS
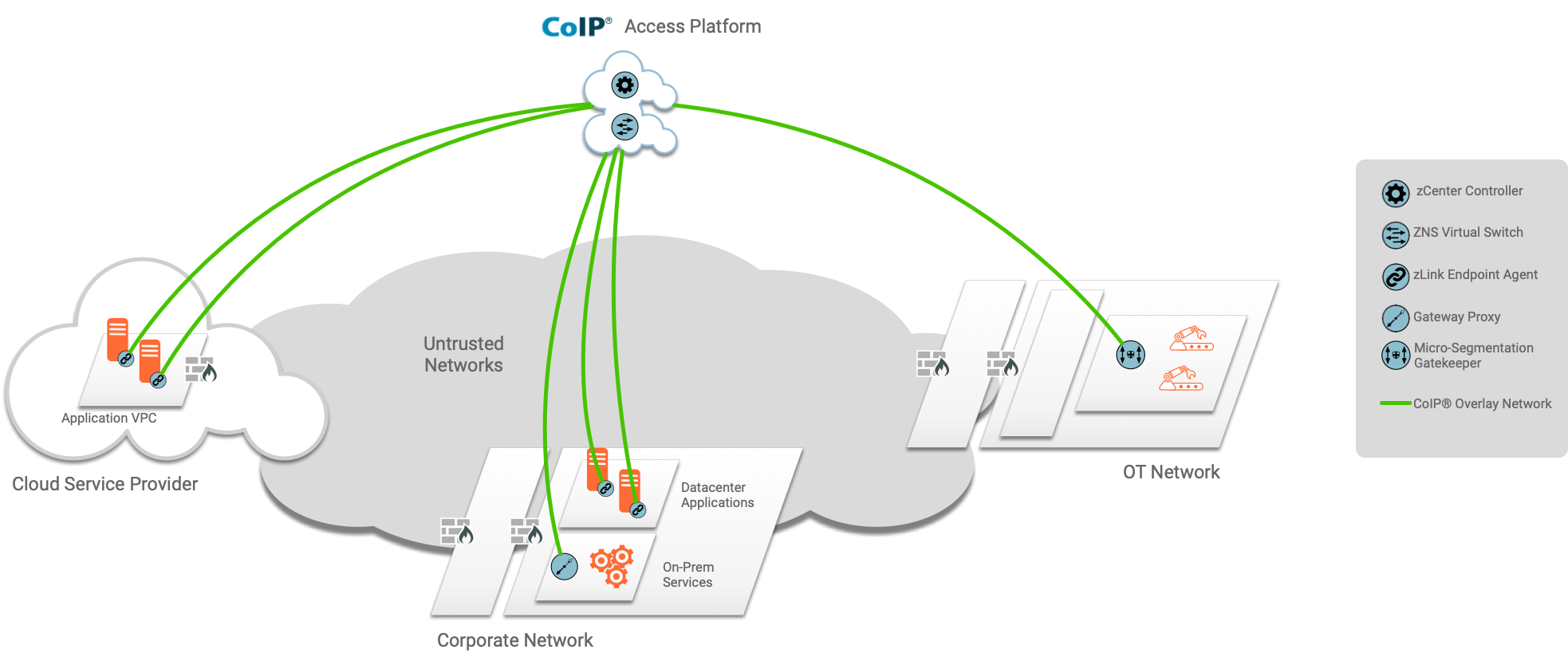
Zentera’s CoIP Access Platform is a Zero Trust security platform that connects and protects applications, endpoints, workloads, services, and users across hybrid environments. Policies that define who can communicate with what resources make security simpler than ever, when old paradigms like network topology-based security give way to user, endpoint, and application identity.
Digital Transformation has changed the way companies do business, but, the pressure to make existing corporate applications and databases available for new cloud or 3rd party applications or to remote workers has created a strain on corporate security – old perimeter-based models of network security don’t work once the users, applications and data go outside of those perimeters.
Current solutions are built on a patchwork of technologies: mobile device management to establish trust, VPNs to encrypt traffic, and UTM firewalls to filter out any unauthorized or malicious traffic. Deploying and managing user access requires wrangling a tangled web of distributed policies, controlled and operated by separate teams. Such an approach requires constant tuning and upkeep to stay in step with increasingly mobile users and applications, and fails to effectively scale to cope with ever-increasing cybersecurity threats.
Built on the principles of Zero Trust, CoIP Access Platform identifies and authenticates users, endpoints, and applications to establish endpoint and user trust. Access is blocked by default; the solution grants whitelisted, “least-privilege” access based on administrator-defined application-aware and time-based policies. By combining centralized policy management with distributed enforcement, CoIP Access Platform enables enterprises of all sizes to add Zero Trust security to existing applications and prepare them for a digitally-transformed future.
How we are different
- Deploys as a SaaS or as an on-prem appliance, allowing companies to set up and provide their own Zero Trust services with their existing Internet backhaul providers.
- Endpoint overlay network implementation avoids the need to touch infrastructure - no VPNs, router, or firewall configuration is necessary. Not only does this speed up implementation of new remote access policies, it also means that the policy enforcement is decoupled from underlay infrastructure, eliminating the need to file tickets to open or close firewall ports or re-engineer network topologies.
- Centralized policy management for end-to-end access control and visibility, across all environments.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



