Photo Gallery
 |

|
Zentera Systems' CoIP Access Platform


Additional Info
| Company | Zentera Systems, Inc. |
| Company size | 10 - 49 employees |
| Website | http://www.zentera.net |
NOMINATION HIGHLIGHTS
Hybrid applications are particularly challenging from a security perspective, because each of the components has its own set of security tools, often managed by different teams. Not to mention, existing security models based on a “hard shell” perimeter require a fixed enforcement point in the network (typically a firewall or UTM appliance), making it difficult to support agility and mobility of hybrid applications.
Additionally, legacy security models provide no defense against attacks originating inside the corporate network; internal traffic is assumed to be trusted. With the rapid shift to work from home that has been driven by Covid-19, attackers have dramatically increased their focus and efforts on obtaining credentials through phishing attacks. Once they land inside, it becomes much more difficult to defend against the attacks.
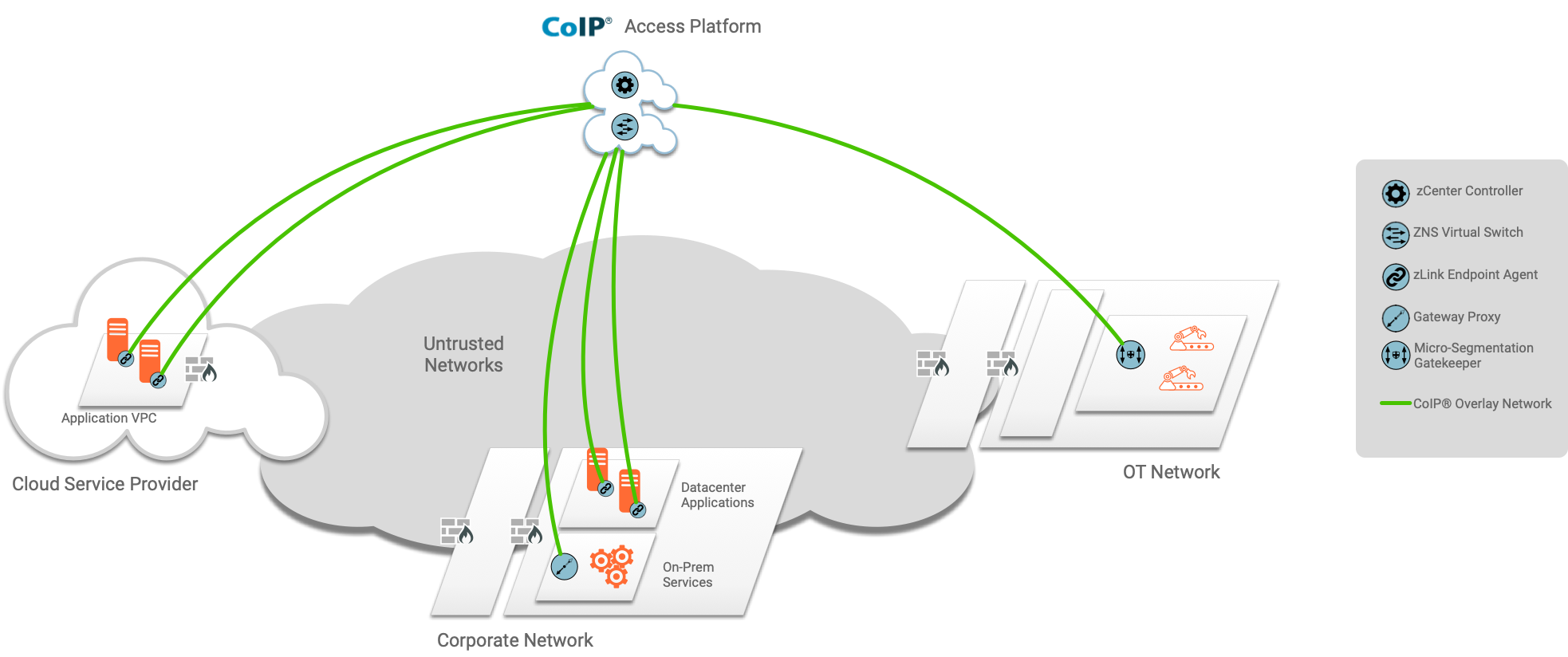
CoIP Access Platform is a complete solution to secure applications deployed in a hybrid cloud environment. It introduces a new security model that authenticates and controls direct communication between endpoints in any environment, on-prem, cloud, or hybrid. With policies based on zero trust principles, administrators have single-pane-of-glass management and visibility over applications deployed in hybrid environments, with security controls including micro-segmentation, firewalls, and threat detection and prevention.
CoIP Access Platform’s combination of security and speed have allowed enterprises to adopted it in a range of hybrid scenarios, including:
– Connecting cloud servers to on-prem services (code repositories, directory services, etc) without exposing the entire on-prem environment to the cloud
– Replicating on-prem databases to the cloud
– Securing applications in a multi-cloud environment
How we are different
- Game-changing security architecture, with both agent-based and agentless deployment models to onboard any TCP/IP application running on any endpoint (bare metal, VM, or container; on-prem or cloud) to Zero Trust identity controls.
- Overlay-based Zero Touch deployment model, which works on top of existing network and security infrastructure, without reconfiguration.
- Centralized console to manage and monitor application connection security across all distributed environments, reducing operational silos.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



