Photo Gallery
 |

 |
Zentera Systems' Zentera Secure Access (ZSA)

Additional Info
| Company | Zentera Systems, Inc. |
| Company size | 10 - 49 employees |
| Website | http://www.zentera.net |
NOMINATION HIGHLIGHTS
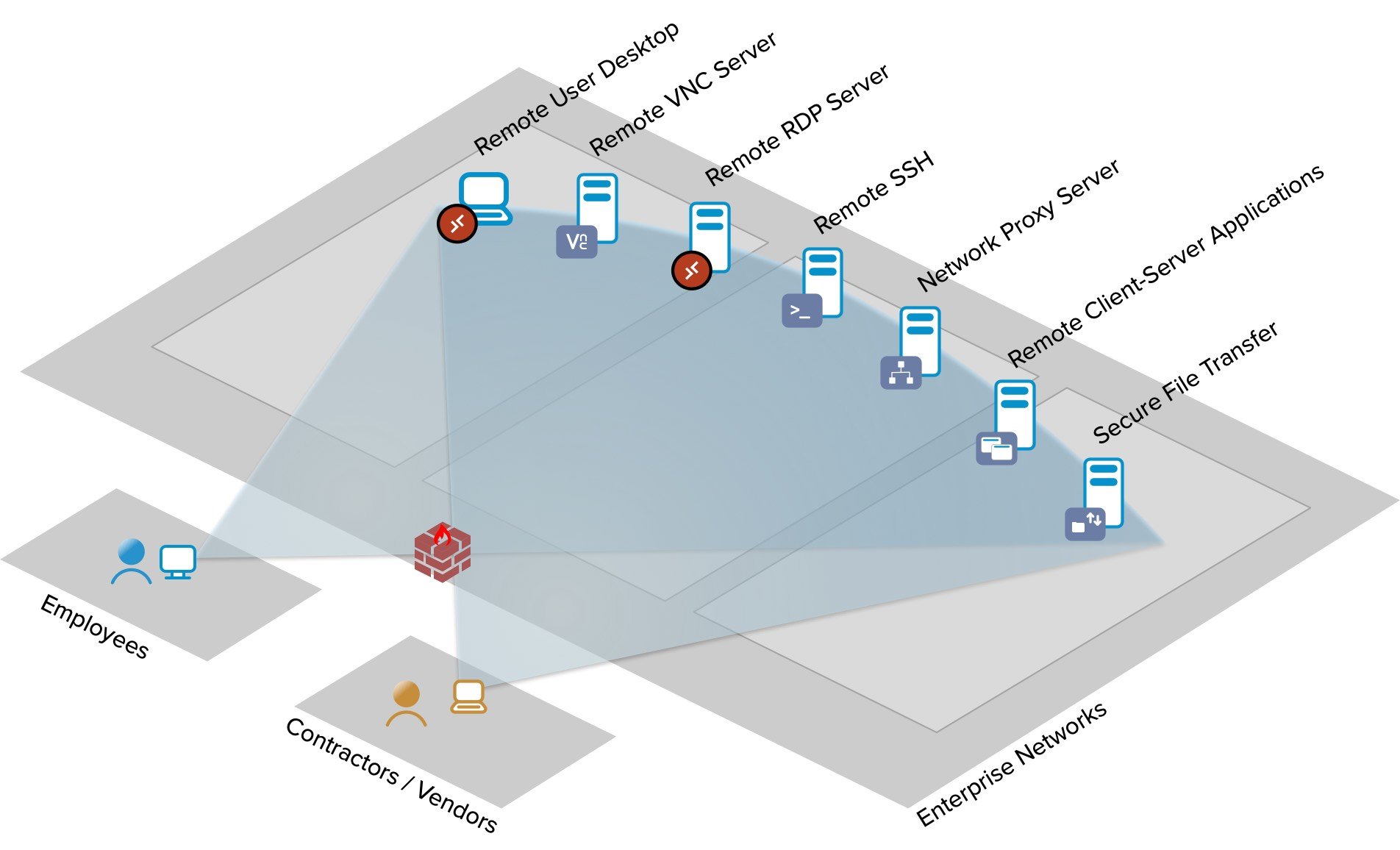
Zentera Secure Access (ZSA) is a privileged access platform that uses the principles of Zero Trust and SASE to dramatically simplify the process of configuring and managing privileged access. By identifying users, endpoints, and applications, administrators are able to create directed access to specific applications running on specific servers for users, based on roles and responsibilities, without providing them VPN access to the entire corporate network.
Current solutions are built on a patchwork of technologies: mobile device management to establish trust, VPNs to encrypt traffic, and UTM firewalls to filter out any unauthorized traffic. Deploying and managing user access requires wrangling a tangled web of policies, operated by separate teams. This approach requires constant tuning and upkeep to stay in step with increasingly mobile users and applications, and fails to cope with ever-increasing cybersecurity threats.
ZSA provides granular access for privileged users, who are identified using the customer’s existing identity provider. Without granting network level access, creating a VPN connection or opening a firewall, ZSA enables remote access, with built-in support for remote terminals, including VNC and RDP, as well as ssh, git, and any standard TCP/IP application.
Enabling remote access without opening the firewall significantly improves security. For example, ZSA can enable users to connect using Microsoft RDP without opening port 3389 to inbound traffic at the firewall, rendering that port inaccessible to unauthenticated users or client software.
End-to-end access control policies can be configured, managed and enforced centrally. Reducing the number of control knobs in the infrastructure significantly streamlines setup, reduces error-prone change requests, and minimizes troubleshooting effort.
ZSA also provides access logs, enabling auditing of user access to corporate resources for compliance initiatives or to inform digital forensics.
Customers have used ZSA to provide secure remote access for remote workers, 3rd parties, and securing access to OT environments.
How we are different
- Strong trust factors to identify and authenticate users, endpoints and applications
- Centralized policy management for end-to-end access control and visibility
- Overlay-based Zero Touch deployment model, which works on top of existing network and security infrastructure, without reconfiguration.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



