Photo Gallery
 |

 |
Asimily


Additional Info
| Company | Asimily |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://www.asimily.com/ |
NOMINATION HIGHLIGHTS
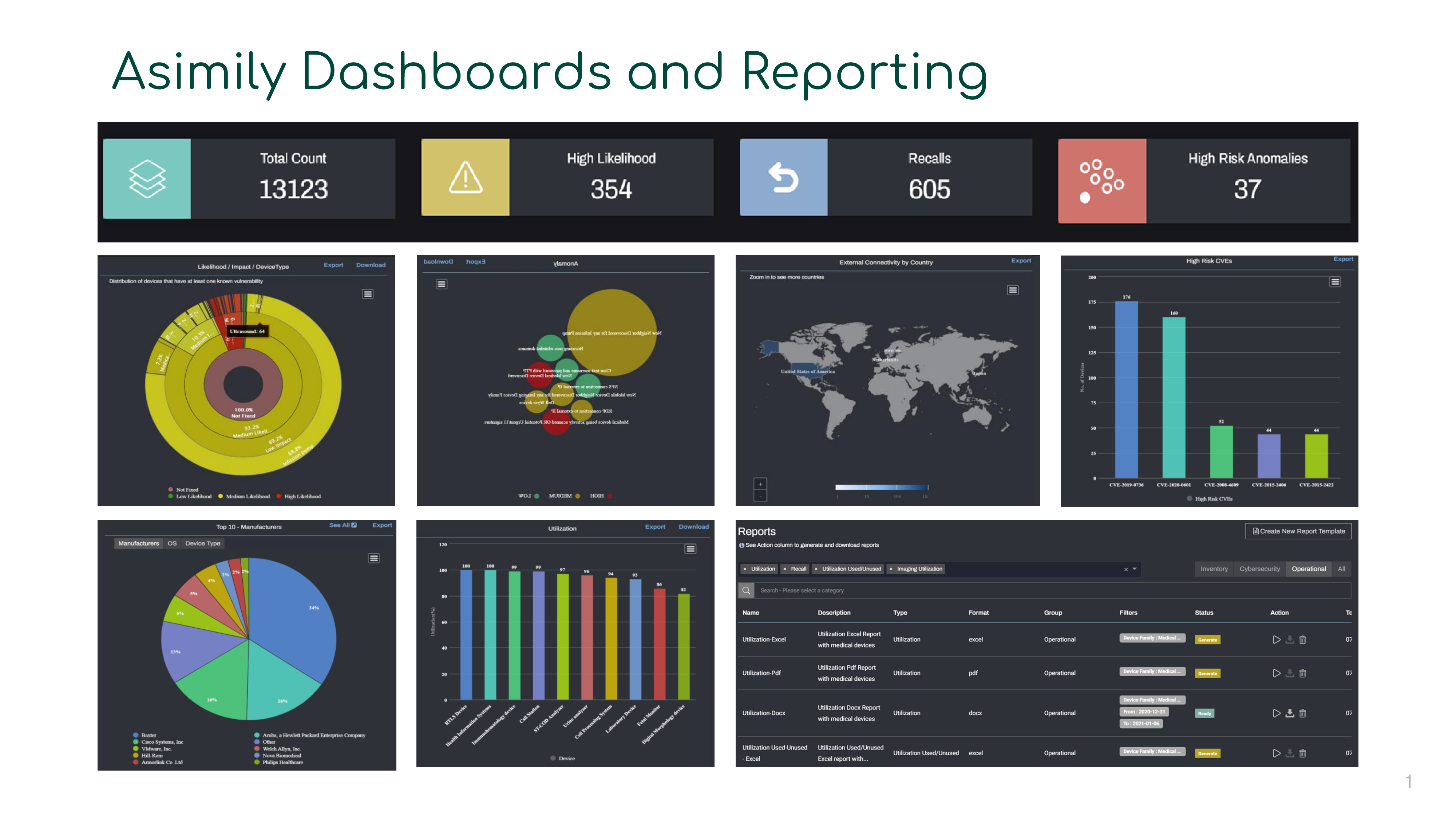
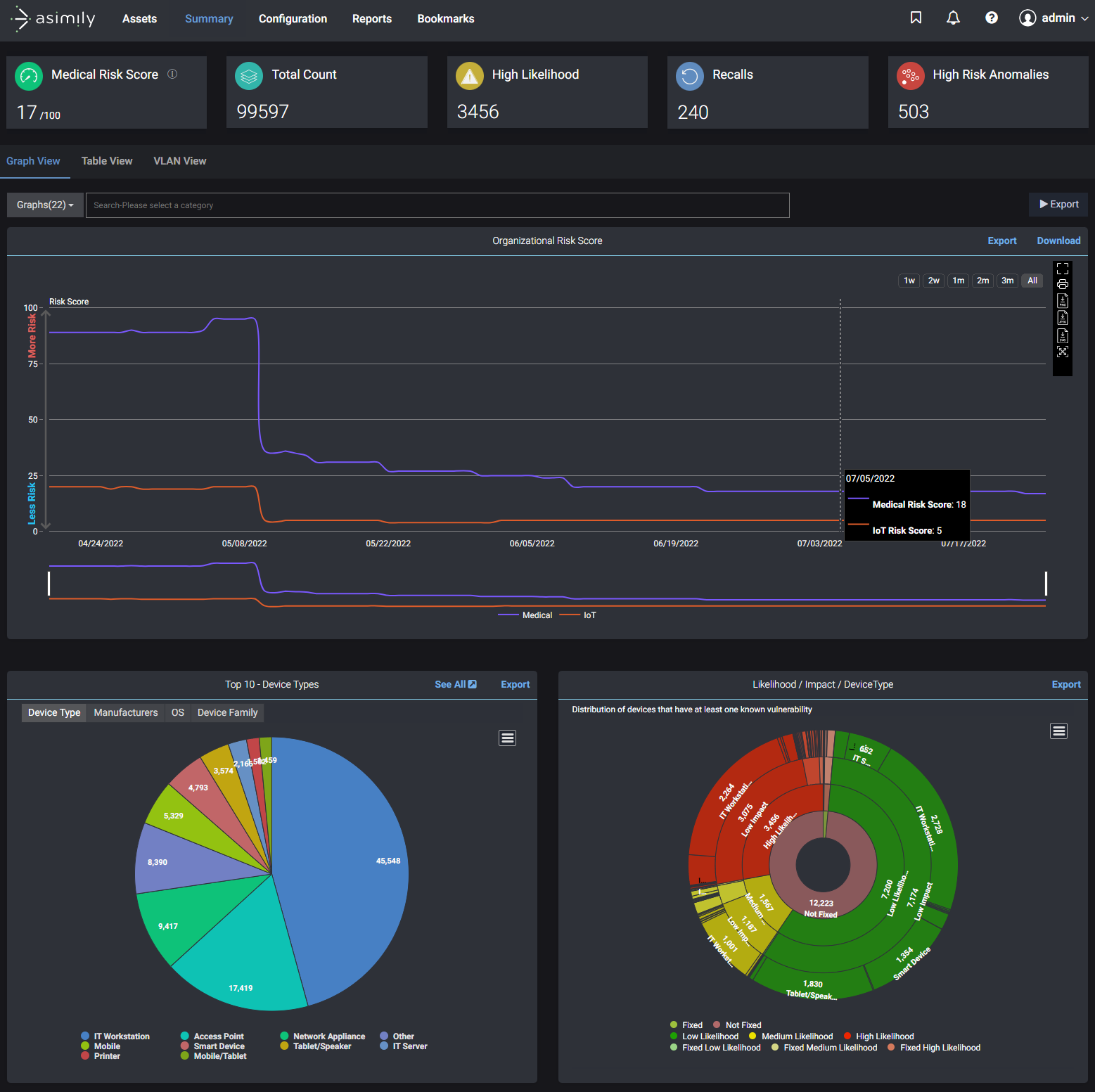
Asimily is a comprehensive Industrial IoT device asset and cybersecurity management platform. Using Asimily, manufacturers and other industrial organizations can comprehensively monitor and manage IIoT devices throughout their entire lifecycle—from pre-procurement all the way to decommissioning.
Through sophisticated passive scanning, Asimily discovers and classifies all Industrial IoT connected devices, with the largest repository of device metadata and capability information. Using Asimily’s proprietary machine learning-based technology, Asimily predicts which devices are most critical to manufacturing operations, and which are most vulnerable to a successful attack. Asimily baselines and profiles device behavior, and detects network anomalies that could indicate a potential compromise or exhibit insecure behavior that could precipitate one. Additionally, Asimily tracks device utilization and active recalls, so industrial organizations can ensure that assets are being allocated efficiently. Asimily helps manufacturers defend their organization, increase device availability and uptime, reduce operational expenses, and achieve compliance with security standards.
Key Capabilities / Features
Device Tracking: The solution helps manufacturers track where devices were last seen on the network, and the last network appliance or access point where it was seen. This helps them find devices that have been lost or forgotten.
Asset Utilization: Asimily tracks the utilization of every IIoT device on the network, how those trends are changing, and granular information such as what specific functions are being used or operations performed. This helps manufacturers with procurement decisions and lifecycle planning.
Vulnerability Management: The solution discovers devices and understands which ones have vulnerabilities with a high likelihood of exploitation. Devices are prioritized using this likelihood and the impact that a breach of the particular device would have, based on Asimily's understanding of the device’s purpose and the type of data it handles.
Inventory: Asimily identifies all IIoT devices in the network for manufacturers. Detailed parameters such as the device's exact model and software version are provided for the most complete and accurate inventory.
Anomaly & Threat Detection: Asimily monitors and detects misconfigurations, attacks, zero-day vulnerabilities, and anomalous behavior from IIoT devices. A number of alerting options are provided, including integration with major SIEM vendors.
Mitigation: For every vulnerability, the solution provides recommendations for mitigation measures that will reduce or eliminate the risk, including when patching or segmentation is not possible. Additionally, Asimily integrates with major NAC and firewall solutions to block, segment, or micro-segment devices on the network, and can apply those policies automatically if desired.
How we are different
-- Asimily identifies and parses more than 100 different protocols, using this context to provide granular device classification for any IIoT device model on the network, with over 99% accuracy.
-- Asimily’s flexible policy engine provides 100% visibility for any device (and on any parameter) through policies recommended by Asimily and targeted for the manufacturing customer. The solution provides automated anomaly and attack detection for new and existing threats, and customers can customize these policies to fit their organization’s specific needs and existing controls. This can be used to detect attacks that can often fly under the radar, such as low-and-slow data exfiltration.
-- Asimily is the only solution with a Distributed Sniffer, which allows manufacturers to capture IIoT network traffic from any devices on the network, either on demand or automatically in response to a network anomaly event. This is critical for network troubleshooting, incident response, and forensic analysis.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



