Photo Gallery
|


|
Best Cybersecurity Strategy

Additional Info
| Company / Organization | https://solutions.com.sa/ |
| Company size | 1,000 - 4,999 employees |
| Country | Saudi Arabia |
| World Region | Middle East |
| Website | https://solutions.com.sa/ |
NOMINATION HIGHLIGHTS
Digitization and Digital Transformation have become key enablers in improving the efficiency and achieving excellence at all levels including nations, people and organizations. However, the most pressing question being discussed in the board and stakeholder meetings is “How do we ensure our digital transformation to be reliable, resilient, and sustainable?”. As we know, cyber threats are growing at rapid pace and leaders across nations and organizations are concerned about its impact in hindering the pace of their digital innovation missions. Adversaries and cyberattacks have become increasingly complex, severely impacting the goals of resilient digital transformation programs. Therefore, an effective and evolving cybersecurity strategy is essential to strike the right balance between managing cyber risks and enabling the business.
This business case annotates the “TRUST” cybersecurity strategy (T-Transform, R-Reinforce, U-Unify, S-Safeguard, T-Thrive) of Arabian Internet and Communication Services Company’s (“solutions by stc” or “solutions”) that aimed at enabling the business to leap forward through successful digital transformations and to be a center of excellence in fulfilling the prestigious 2030 Vision of the Kingdom of Saudi Arabia. The 5 pillars of “TRUST” cybersecurity strategy is summarized below:
T (Transform): Transform products and service offerings by engineering cybersecurity capabilities into our service offerings.
R (Reinforce): Reinforce cybersecurity capabilities to stay ahead of emerging threats and ensuring compliance with applicable regulations and standards.
U (Unify): Unify cybersecurity capabilities and act as a key driver to enable business objectives and transform company’s internal culture.
S (Safeguard): Safeguard business data with enhanced data protection and privacy rights using state-of-the-art technologies, optimized processes and governance excellence.
T (Thrive): Thrive in GCC (Gulf Cooperation Council) as a leader in cybersecurity using cutting-edge and innovative capabilities building customer trust and contributing towards 2030 Vision of the Kingdom of Saudi Arabia.
Accomplishments
Values Realized: Evaluations and external independent reviews of the solutions’ Cybersecurity program recognized that the solutions’ TRUST cybersecurity strategy execution overachieved on its targets. Where, the intended maturity was to improve from the ‘Reactive’ maturity level (Maturity score: 2) to ‘Integrated’ maturity level (maturity score: 4); the achieved maturity level is ‘Best-in-Class’ (maturity score: 5).
Key Accomplishments: The key accomplishments realized to solutions’ through TRUST cybersecurity strategy’s successful transformation journey is summarized below.
Achieved advanced levels of cybersecurity compliance against the cybersecurity regulatory requirements in Saudi Arabia.
Ranked #1 in cybersecurity maturity for 2 consecutive years among the group of companies.
Automated key cybersecurity processes and activities related to risk management, compliance monitoring, offensive & defensive cybersecurity practices and performance management capabilities.
Adoption of Service Management and Customer Experience metrics to deliver high quality cybersecurity services.
Established a robust cybersecurity risk management program to significantly reduce the cyber risks.
Brought about effective cybersecurity culture via continuous learning and awareness to keep the skills and capabilities of solutions’ staff and associated 3rd parties up-to-date and relevant.
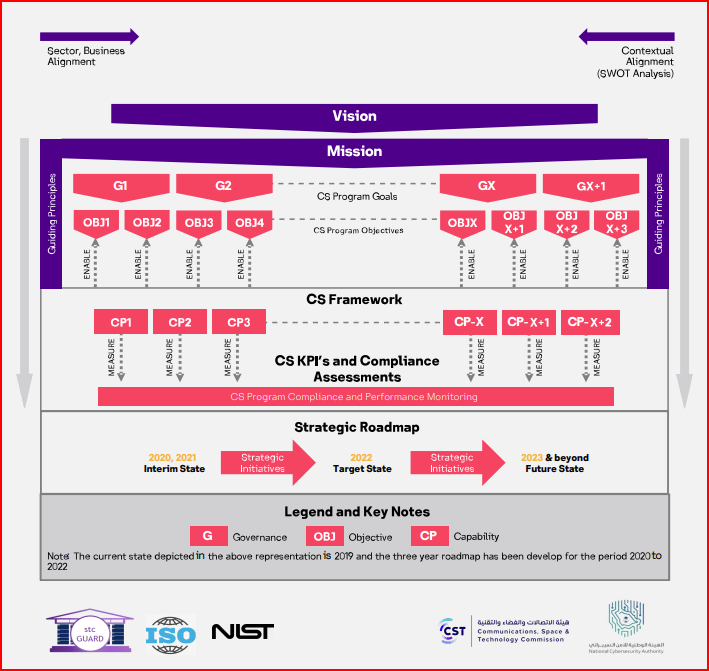
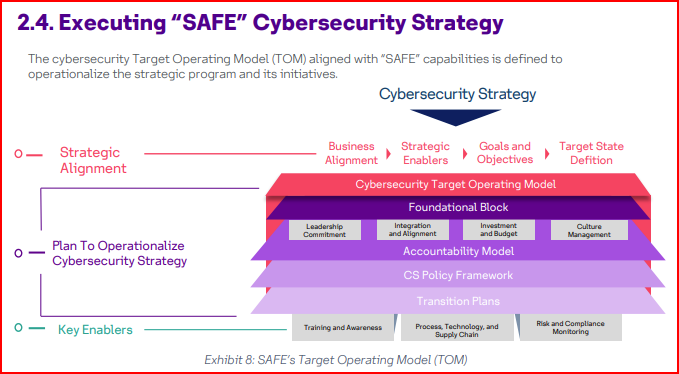
**The skeleton of “TRUST” cybersecurity strategy: solutions’ “TRUST” cybersecurity strategy is defined by its vision, mission, goals, objectives, and 40+ capabilities; towards achieving its core objective of business enablement with cyber resilience. The overall skeleton of the SAFE strategy is depicted in the exhibit below.
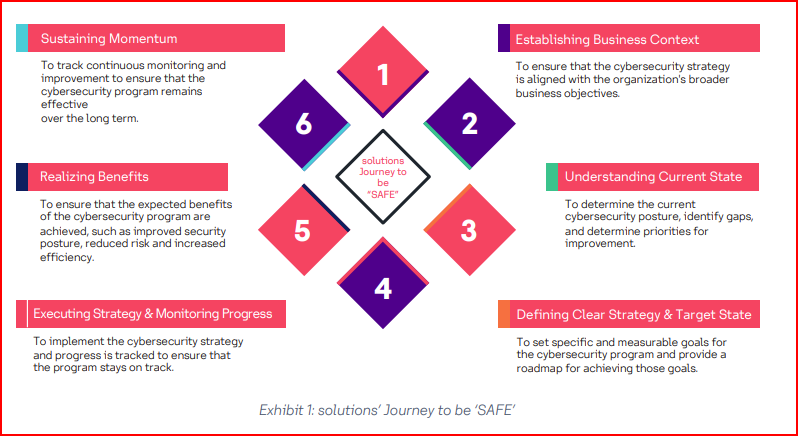
**The 6-staged “TRUST” Journey: Defining a cybersecurity strategy is neither the beginning nor the end; it’s a journey with series of events and initiatives. The figure below showcases solutions’ “TRUST” cybersecurity strategy transformation journey for a sustainable, resilient digital future.


