Cyberbit Solution for Smart Building Security
Nominated in the Category:
Photo Gallery
 |

 |
Cyberbit Solution for Smart Building Security


Additional Info
| Company / Organization | Cyberbit Ltd. |
| Company size | 100 - 499 employees |
| Country | Israel |
| World Region | Middle East |
| Website | http://www.cyberbit.com |
NOMINATION HIGHLIGHTS
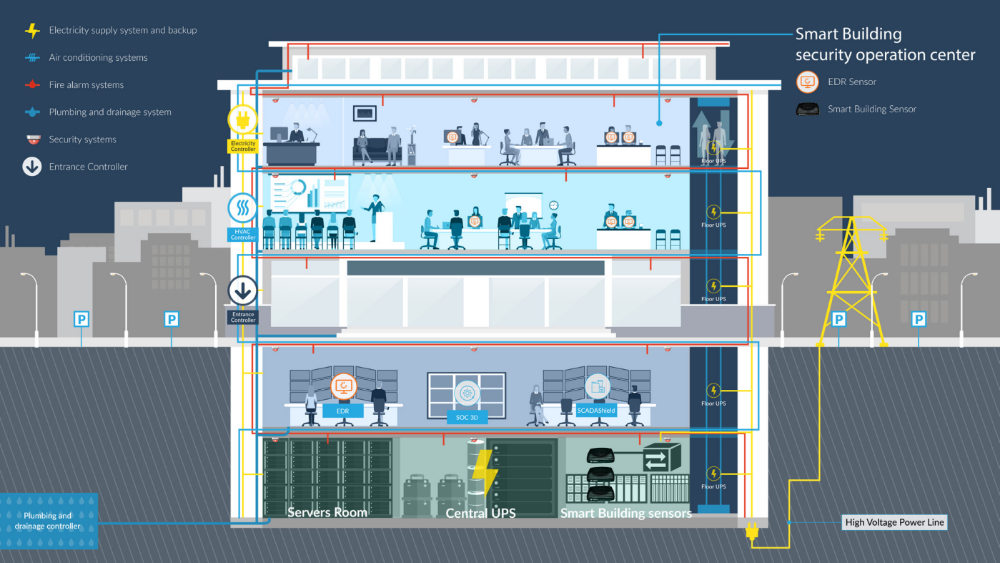
‘Smart buildings’ and data centers use automation and digital control to provide functional and operational advantages, but this connectivity also introduces new cybersecurity risks. Potential attackers can use the internet to gain access to critical physical systems and cause a myriad of damage such as; tampering with surveillance systems, shutting down critical systems like elevators and gates or power and water, and commandeering IP connected devices within the building.
In early 2016, Cyberbit was contacted by a large consulting firm regarding cybersecurity solutions for a new government compound. The structure was designed with the most advanced smart building features, but the project managers and consultants knew this would also put it at risk for cyberattack. Due to the sensitive nature of the facility, security was a major concern from the first day of planning. They sought a unified solution that could secure both the IT and OT networks and connect security information and alerts across multiple environments. This is especially important in converged environments like smart buildings where cyberattacks can traverse between IT, OT and IoT.
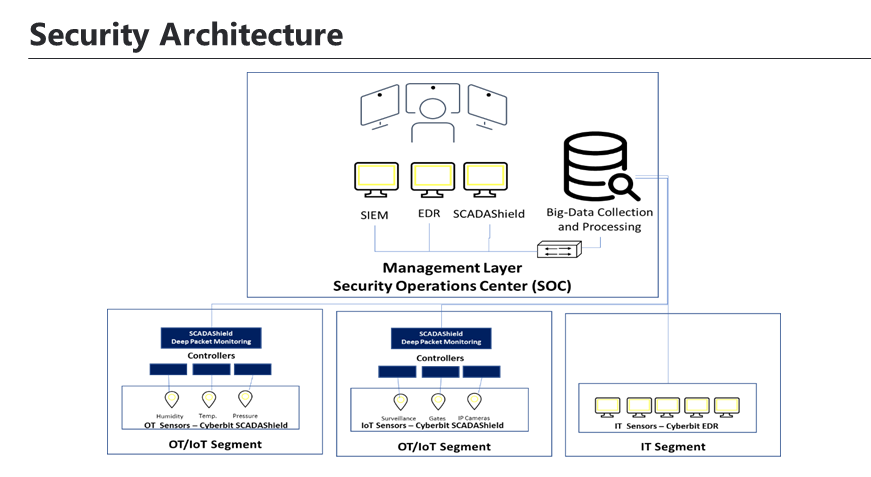
The Cyberbit smart building cybersecurity solution included:
IT sensors – EDR sensors were installed on all IT endpoints to continuously record kernel-level data from OS and analyze is for signs of malicious activity using behavioral analysis and machine learning algorithms.
IoT Monitoring – monitoring of IoT device activity, including surveillance cameras.
OT sensors – SCADAShield OT monitoring devices were installed to track OT network and industrial IT components to perform passive, non-intrusive granular DPI of OT network transmissions.
Centralized security operations – the entire operation is centrally managed from the facility’s SOC which collects all data from IT, OT and IoT systems and centralized alert correlation and incident response.
Accomplishments
• Integrated security across the entire attack surface -
The solution secures the entire IT, OT and IoT infrastructure
and all devices and analyzes data from all 3 segments to rapidly
understand multi-vector attacks or lateral movements between segments.
• Centralized visibility – Security is managed from a central Security Operations Center (SOC) enabling 24/7 situational awareness across IT, OT and IoT segments.
• Centralized incident response – In the event of a security incident, the SOC team can manage it centrally and analysts can access all real-time security data and tools from a single location, to accelerate response to security breaches no matter which segment(s) are affected.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



