Photo Gallery

|


|
TRIOVEGA GmbH - edge.SHIELDOR

Additional Info
| Company | TRIOVEGA GmbH |
| Company size | 50 - 99 employees |
| World Region | Europe |
| Website | https://triovega.com/ |
NOMINATION HIGHLIGHTS
In the rapidly evolving digital landscape, cybersecurity risks demand continuous adaptation. Organizations must proactively assess their security infrastructure, invest in advanced threat detection technologies, and develop comprehensive strategies. By objectively addressing these challenges, businesses can build more resilient approaches to protecting their digital assets and maintaining operational integrity.
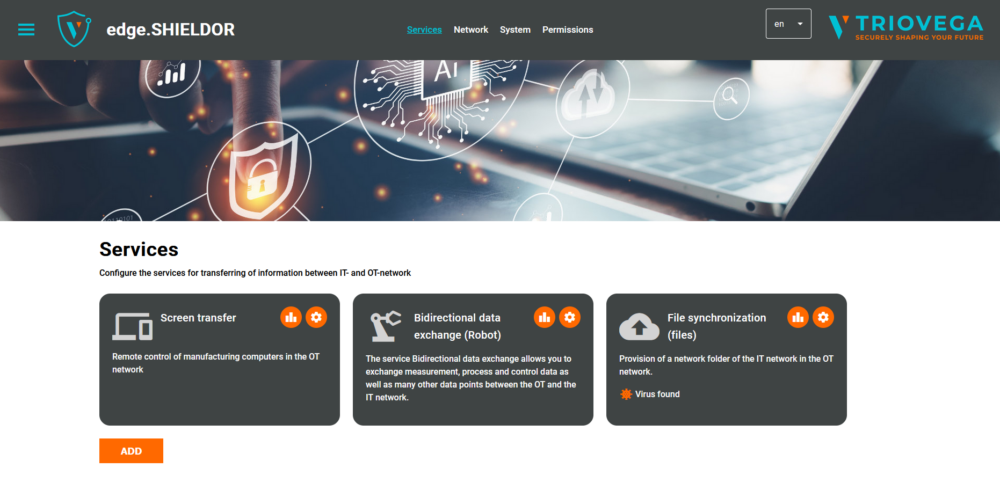
This is where our innovative security solution, edge.SHIELDOR, comes in. The solution works just like a protective “glass dome” placed over each production line, safeguarding both, the production equipment and the company network from cyber threats. Our product seamlessly combines the opposing goals of cybersecurity and connectivity in production environments. Despite stringent security measures—such as the complete separation of Information Technology (IT) and Operational Technology (OT) networks—edge.SHIELDOR enables secure data exchange between IT and OT networks. Through additional services like protocol conversion, edge.SHIELDOR can also securely integrate legacy machines that were previously taken off the network due to cybersecurity concerns. In real-world applications, this innovation has proven to significantly improve both production security and operational efficiency.
To maintain high security standards, access to edge.SHIELDOR instances is restricted to authorized users only, managed through a company-wide user directory service or a locally integrated user management system. Additional authentication mechanisms can also be implemented to further enhance security e.g. SAML.
The security concept behind edge.SHIELDOR is currently in the patenting process (WO 2022/128829 A1, German Patent and Trade Mark Office), with the patent acknowledged to be granted in Q2 2025, since all legal aspects were clarified end of 2024.
Key Capabilities / Features
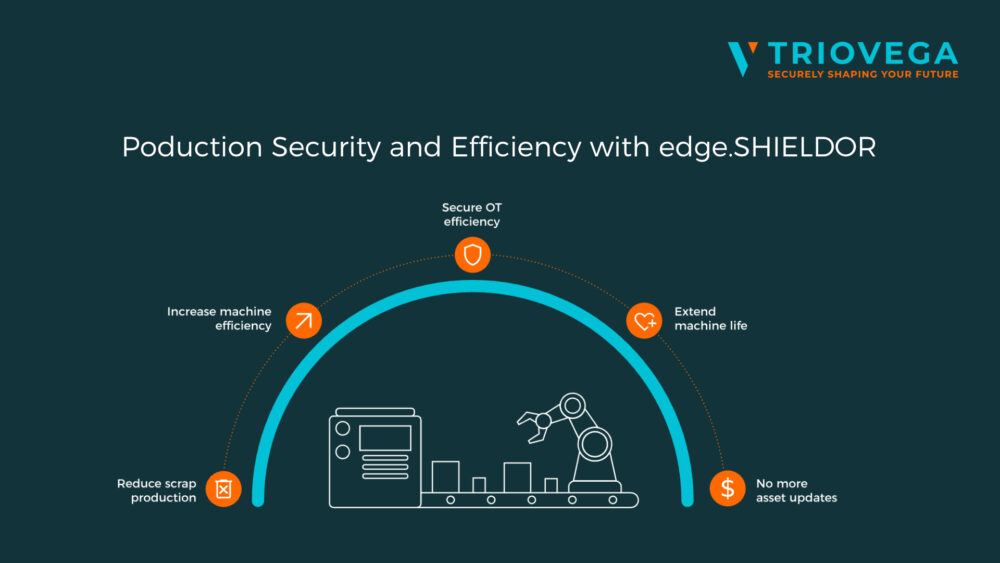
edge.SHIELDOR positively impacts our customers by reducing costs, enhancing efficiency and improving the overall security: Its interoperability enables the incorporation of existing production software components without compromising security, thereby streamlining OT security management and reducing Capital Expenditures (CapEx). Additionally, simplifying the patch management process by reducing the number of security updates required and allowing users to schedule these updates during planned production line downtime reduces Operational Expenditures (OpEx).
By supporting various protocols, edge.SHIELDOR seamlessly integrates both older and newer machines into existing networks. Consequently, the solution contributes to extending the service life of machines. The newly achieved secure data connectivity also enables data science activities, that can significantly increase production efficiency, reduce scrap amongst many other advantages.
The products unique security concept allows to simplify the process of updating and securing manufacturing machines without disrupting production or relying on maintenance windows, edge.SHIELDOR eliminates the need for machine software updates.
Implementing edge.SHIELDOR helps companies to mitigate key cybersecurity risks:
Common vulnerabilities in operating systems and equipments are a prevalent risk at manufacturing companies. Through edge.SHIELDOR's security concept, production systems are safeguarded, and many of these risks are eliminated by completely separating the OT network from the IT network.
For example, insecure protocols pose a significant risk, which edge.SHIELDOR addresses by converting outdated and insecure protocols (e.g., OPC-DA, SMBv1) into secure ones (e.g., OPC-UA or SMBv3).
Another prevalent risk is password management and password strength. edge.SHIELDOR proactively mitigates this issue by integrating with the company’s authentication and user management systems, while additionally having its own authentication methods.
Looking into the future, the development road map for edge.SHIELDOR includes an external access (VPN access), which is expected to be implemented and released in the first half of 2025.
How we are different
+ Typically, implementing OT security approaches can lead to a loss of connectivity and data access, especially when integrating legacy machines. These older machines often use outdated, insecure protocols that pose significant security risks. Think of it like sending a letter to an address, but the door code to that address is also being transmitted visibly on top of the envelope - a gateway for attackers. edge.SHIELDOR addresses these challenges by converting insecure protocols into secure ones, allowing legacy machines to be integrated securely into modern IT networks.
The product's security architecture implements a complete segregation between IT and OT networks, while still enabling selective and controlled data transfer between these two environments. This enables secure access to process data, a unique selling point to other security solutions. Furthermore, machines which were previously disconnected from the network due to security concerns are now back in operation, with their software-based service life effectively extended. Establishing secure data connectivity is a crucial step in the digital transformation of production environments. This newly achieved data connectivity lays the foundation for further data science activities, which are necessary in efforts to significantly increase production efficiency and Overall Equipment Efficiency (OEE).
+ edge.SHIELDOR operates entirely in the background, ensuring that production runs uninterrupted. In fact, edge.SHIELDOR allows machines to operate securely even when critical updates are pending. These updates can then be scheduled during planned maintenance windows, minimising unexpected interruptions.
+ Based on thorough market research, edge.SHIELDOR is the only solution applicable without peripherals (i.e. deployed on virtual machines). This advantage enhances OT-security without requiring additional physical IT assets (e.g. IPC) that also need maintenance or updates and thereby reduces the complexity significantly.


