Kentik Detect
Photo Gallery
 |
 |
Kentik Detect

Additional Info
| Company | Kentik Technologies |
| Website | http://www.kentik.com |
| Company size (employees) | 50 |
| Type of solution | Software |
Overview
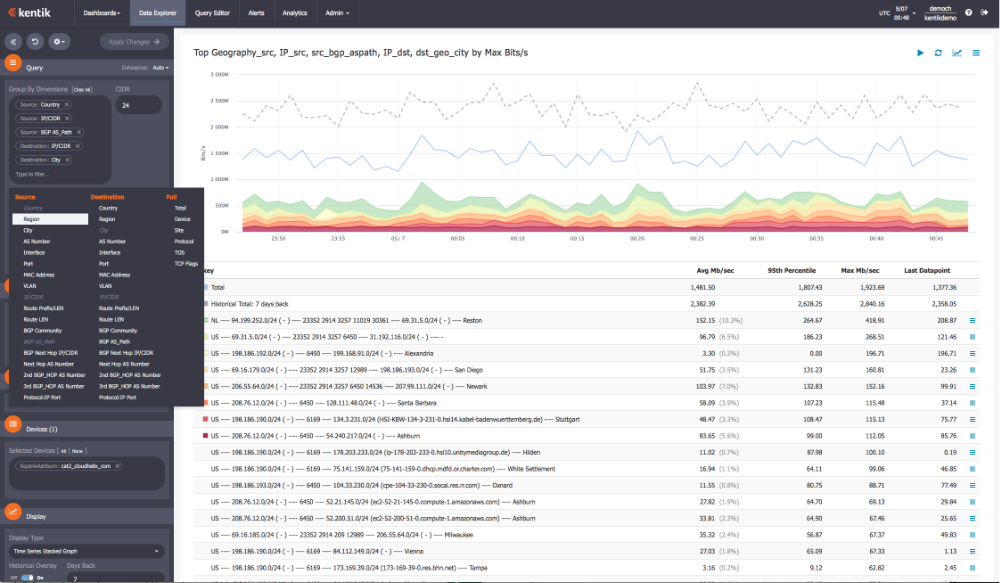
Kentik Detect offers the industry’s only purpose-built big data network analytics and DDoS detection platform, offered as a convenient SaaS or on-premises deployment. Kentik Detect ingests tens of billions of traffic flow, BGP, SNMP, network performance and geolocation data records per day, offers learning algorithm-based, network-wide traffic anomaly detection that delivers 30% greater DDoS detection accuracy than legacy, single server appliances, and provides web portal-based multi-dimensional, ad-hoc network analytics on multi-billion row datasets with query responses in a few seconds.
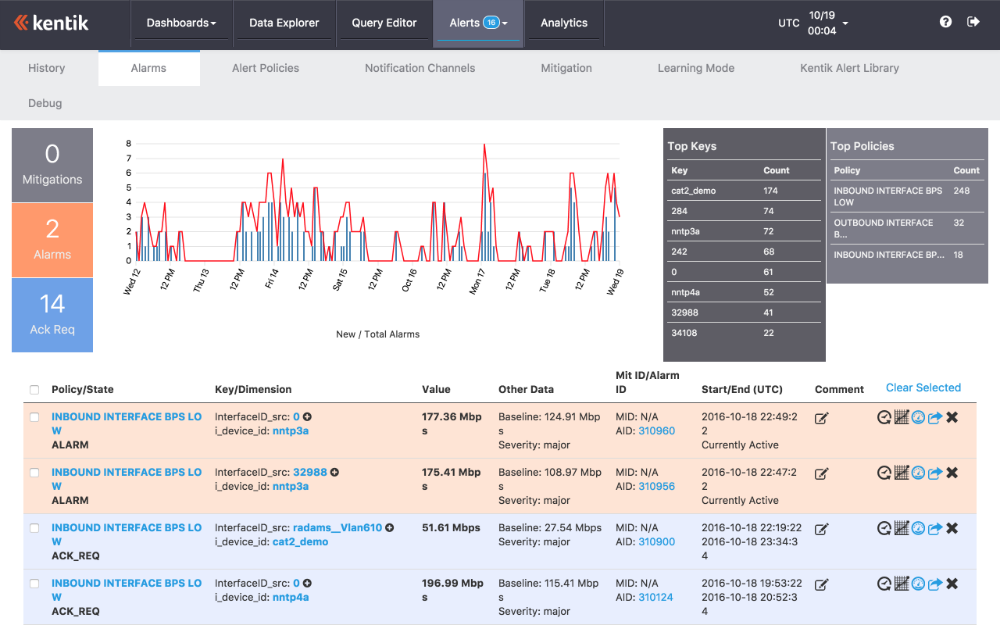
Kentik Detect’s DDoS detection automates triggering of hybrid mitigation techniques including Remote Triggered Black Hole, and integration with Radware, A10 and other mitigation solution providers.
Kentik Detect’s anomaly detection and ad-hoc analytics provides the most powerful way to detect bad network traffic behaviors and diagnose traffic patterns rapidly, for greater security operations and forensic intelligence.
How we are different
--Breakthrough in DDoS detection with 30% greater detection accuracy and automated vendor-neutral, hybrid mitigation support
--Only big data-powered network traffic analytics platform for network and security forensics
--Only multi-dimensional traffic anomaly detection and adapative, learning-algorithm baselining for security operations


