archTIS NC Protect
Photo Gallery
 |

 |
archTIS NC Protect

Additional Info
| Company | archTIS |
| Website | https://www.archtis.com/ |
| Company size (employees) | 10 to 49 |
| Headquarters Region | Asia |
| Type of solution | Software |
Overview
NC Protect from archTIS is a data-centric security solution that provides a simple, fast and dynamic solution to tailor information access and protection across popular enterprise collaboration and file sharing tools while meeting strict compliance and security obligations.
NC Protect finds, classifies and secures unstructured data in on-premises, cloud and hybrid environments to protect against breaches, data misuse and unauthorized file access by ensuring that users access, use and share files according to organizational regulations and policies. It dynamically enforces compliance and data security policies for global privacy regulations, confidentiality, intellectual property, data loss prevention, sensitive data access, information barriers, and custom business policies.
NC Protect’s data-centric, real-time information protection policies increase adoption and ROI of technology investments – without the complexity or cost of native tools. It allows IT administrators and security owners to manage user access without creating more security groups, sites, folders, or other information silos. Instead, admins define access rules, usage and sharing rights to control user actions dynamically to ensure that only the right users – access the right information – at the right time.
NC Protect integrates natively into Microsoft applications and file shares to add data-centric access control and data protection capabilities. Dynamic attribute-based access control (ABAC) and data protection policies safeguard files at rest and in motion. It enforces real-time conditional access, sharing and usage control of files and email based on data, user and environmental attributes. If the user context or data attributes change, NC Protect automatically adjusts access and protections based on defined policies. It dynamically enforces access and security policies for each and every user and device, completely transparent to the end user.
NC Protect is fully integrated with Microsoft 365 (SharePoint, OneDrive, Exchange), Microsoft 365 GCC High, SharePoint Server, NetApp ONTAP, Nutanix Files and Windows file shares.
Key Capabilities / Features
NC Protect from archTIS protects sensitive information against data loss and insider threats. It provides policy-based data-centric information security that is simple, fast and dynamic across Microsoft 365 and GCC High applications, including SharePoint Online, Exchange, Office, OneDrive, and SharePoint on-premises, Nutanix, NetApp ONTAP and Windows File Share environments.
It enhances enterprise applications with data-centric security capabilities to:
• Automatically discover and classify sensitive content based on the sensitivity level of its contents
• Dynamically adjust file access rights and protection based on file, user and environmental attributes to control who can access information, and how it can be used, copied or shared
• Adjust security with fine-grain access and protection policies as files move between people and locations
• Enforce secure read-only viewing of sensitive information with a built-in Secure Reader
• Encrypt individual files automatically only when the situation requires
• Redacts sensitive or confidential information, such as keywords or phrases
• Obfuscate/Hide files from the view of unauthorized users in the application UO
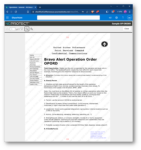
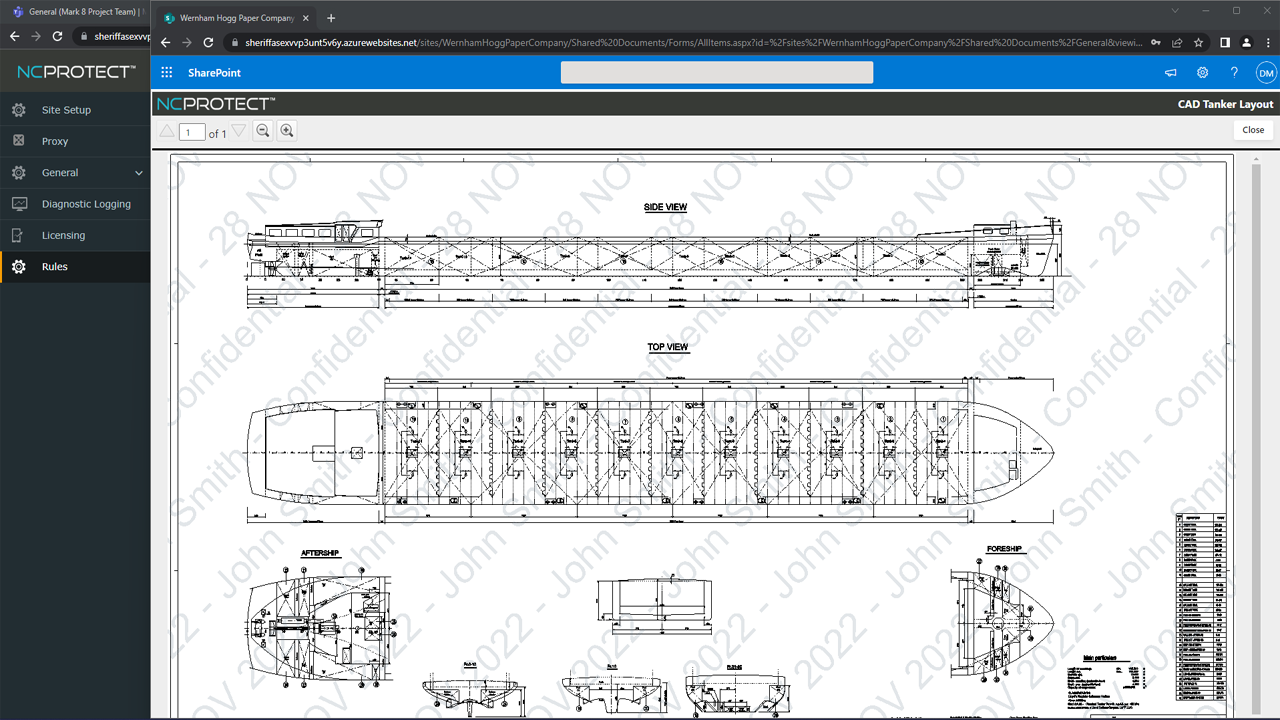
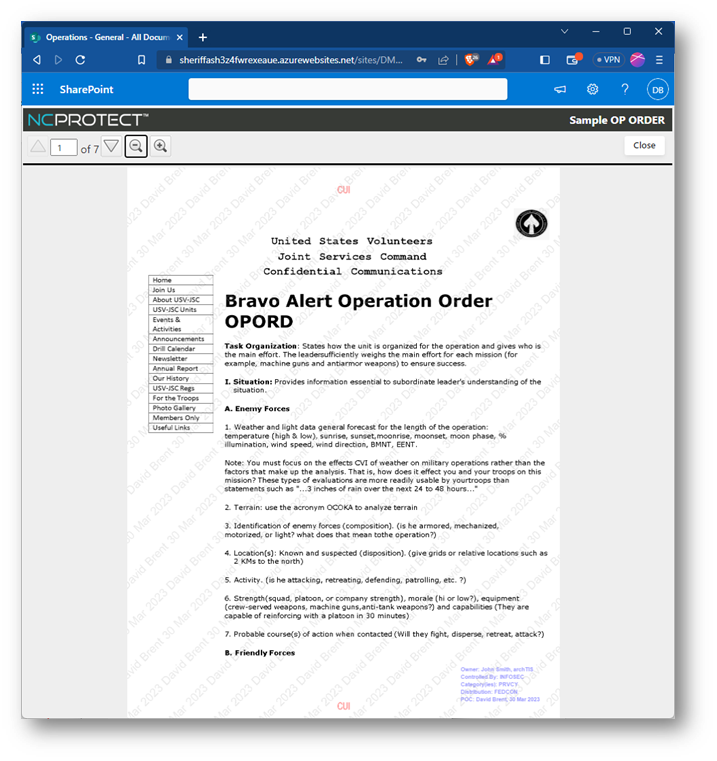
• Add handler-based security watermarks automatically to Word, PowerPoint, Excel and PDF documents to track chain of custody
• Insert Controlled Unclassified Information (CUI) Banners/Footers and CUI Designation Indicator labels, including Owner Name, Controlled By, Category, Distribution/Limited Dissemination Control and POC to documents as a watermark for CMMC 2.0, DFARs and NIST compliance.
• File integrity checks prevent users from overwriting valid files with corrupted files and protect digital assets from being maliciously encrypted.
• Supports common file types, including Word, Excel, PowerPoint, PDF, OCR, CAD, images, text files and more.
• Log all access to and actions taken with protected documents. Audit logs can be integrated with SIEM tools (Splunk and Microsoft Sentinel) for further analysis and downstream actions.
NC Protect’s unique capabilities enhance data security across an organization's enterprise collaboration and file sharing applications.
How we are different
• NC Protect’s data-centric ABAC-based policies dynamically enforce access, usage, and sharing rights in real-time based on file and user context. Policies can be managed and applied centrally across enterprise collaboration tools for consistent and scalable data security and insider threat protection. Policies are enforced efficiently and dynamically without the need to create separate sites, roles or security groups.
• Augments native security features in supported platforms to enforce secure read-only access, hide sensitive files from unauthorized users, redact sensitive or classified information, trim the application ribbon, apply dynamic user-based security watermarks, and encrypt or restrict attachments sent through Exchange Email.
• Requires no additional client-side application, reducing IT overhead and implementation time to start securing data in hours, not days or weeks. Access and security policies are enforced for every user and device every time access to a specific file is requested, completely transparent to the end user.



