Attivo Networks ThreatDefend Endpoint Detection Solution
Photo Gallery
 |
 |
Attivo Networks ThreatDefend Endpoint Detection Solution

Additional Info
| Company | ATTIVO NETWORKS |
| Website | https://attivonetworks.com/ |
| Company size (employees) | 100 to 499 |
| Type of solution | Software |
Overview
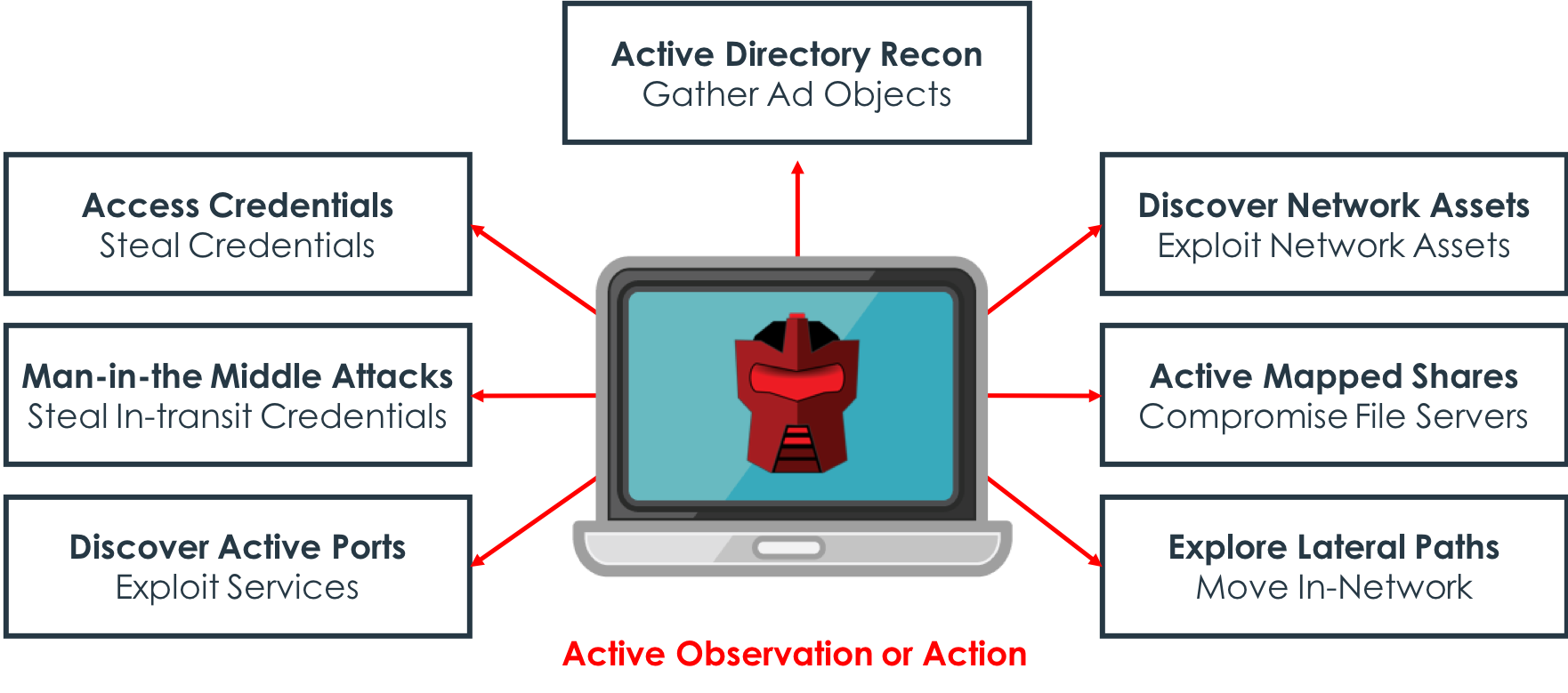
The Attivo Networks Endpoint Defense changes the game so that attackers can’t break out from the endpoint.
The ThreatDefend offerings interweave deception throughout the network and also turn every endpoint into a decoy designed to disrupt an attacker’s ability to break out without installing agents or disrupting network operations. The attack methods detected include, but are not limited to:
• Stealing local credentials
• Looking for file shares and connected systems
• Network reconnaissance as they look for hosts (production assets) and available services on these hosts
• Active Directory queries with the ability to hide information and return deceptive data to queries
• Man-in-the-Middle attacks where attackers steal credentials in transit
Locking down the endpoint with deception dramatically reduces risk by detecting attacks early and preventing lateral movement. Plus, alerts are substantiated, actionable, and provide company-centric threat intelligence for stopping an attack, hunting threats, and remediating faster.
• Locks down lateral movement from the endpoint in an efficient and agentless manner. In a recent EMA survey, deception customers cite 5-day dwell times and high confidence in detecting threats. This result was 90% better than users unfamiliar with deception technology.
• Creates deception credentials that identically match those of the system user. They are crafted to mirror-match, dynamically refresh timestamps, and they appear as any other credential would. They are so authentic that Red teams and tools like HoneypotBuster can’t tell the difference. These credentials breadcrumb the attacker into the deception decoy environment.
• Mapped shares attract attackers into the decoy environment, along with native integrations with existing endpoint solutions that can automatically quarantine the infected system. Additionally, the solution will “entertain” the attacker with reams of fake data, providing time to isolate the system and prevent further spreading.
• Network discovery attempts get derailed as the Attivo deception fabric interweaves decoy endpoints throughout the environment, with support for Microsoft, Linux, and Mac OS
How we are different
• The solution provides capabilities to monitor available services on production endpoints, and redirects attempted access into a deception environment. Every endpoint on the network effectively becomes a decoy and, when paired with the company’s deception lures, locks down an attacker’s ability to break out from the system without getting caught.
• Defenders also gain visibility into the attacker’s tools, the use of malicious software, and the ability to quickly quarantine infected systems.
• When attackers query Active Directory, the solution alters the response and adds deceptive content, creating an altered reality for the attacker, hiding valuable enterprise resource information, and reducing attack surfaces. With the redirection of activities into the deception environment, teams can also study the attack and gather Tactics, Techniques, and Procedures (TTPs), along with company-specific threat intelligence.



