AuthMind Identity SecOps Platform
Photo Gallery
 |
 |
AuthMind Identity SecOps Platform

Additional Info
| Company | AuthMind |
| Website | http://www.authmind.com |
| Company size (employees) | 10 to 49 |
| Headquarters Region | North America |
| Type of solution | Cloud/SaaS |
Overview
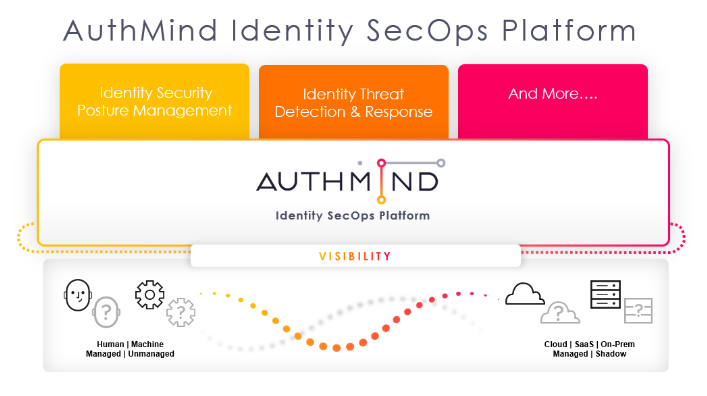
The root cause of most data breaches today surrounds compromised identities. After all, hackers don’t hack in, they log in. The reality is that people, processes, and technology supporting Identity and Access Management (IAM) programs at organizations still need to align with what this actually means to make identity the new perimeter. Most IAM programs were built to enable access but are poorly equipped to detect identity misconfigurations, vulnerabilities, and threats. That is why securing identities is now emerging as a key pillar of an organization’s cybersecurity defenses alongside other security investments.
As part of this transition, security teams are now investing in two new areas, Identity Security Posture Management (ISPM) and Identity Threat Detection and Response (ITDR), as they elevate the importance of securing identities to prevent attacks.
ISPM is about preventing identity-based attacks by surfacing misconfigurations in a customer’s identity stack that make them vulnerable. These include challenges in correctly identifying users across different systems, configuring multi-factor authentication (MFA) incorrectly, and enforcing access via Privileged Access Management by users with privileged access. Reviewing and resolving these misconfigurations must be done on an ongoing basis using ISPM tools since an organization’s attack surface is consistently changing as new identities are granted access and new applications are introduced.
ITDR is about detecting and responding to identity threats with the identity infrastructure as they happen in real-time. ITDR solutions make incident resolution faster for Security Operation Center (SOC) teams by providing full identity context to incidents, allowing SOC teams to quickly determine all identities involved to discover the “who, what, when, and where” surrounding the incident. ITDR solutions can provide these insights even if an identity is not part of an organization’s existing Identity Directory or working from an unmanaged device.
AuthMind uniquely provides both ISPM and ITDR.
Key Capabilities / Features
- At the core of AuthMind’s Identity SecOps Platform are its Visibility capabilities. AuthMind’s cutting-edge patented Access Neural Network (AI Graph) technology delivers unparalleled visibility into the activities of both human and machine identities when they access cloud services, SaaS platforms, and on-premises assets. AuthMind's technology is distinct as it guarantees consistent visibility, even when dealing with unmanaged identities and unidentified assets.
- The Visibility provided by AuthMind enables Identity Security Posture Management (ISPM) so that identity teams can quickly identify and address identity-related blind spots, in the same way that Wiz provides Cloud Security Posture Management for cloud security teams. These blind spots include shadow assets not managed by any directory or Identity Provider, unauthorized local accounts, missing multi-factor authentication, and access that bypasses an organization’s established security policies. AuthMind also simplifies the resolution of common identity operation issues, such as locked accounts, and improves the resilience of the identity infrastructure.
- AuthMind’s Visibility also offers comprehensive Identity Threat Detection and Response (ITDR) capabilities, a feature notably absent in XDR and EDR solutions such as CrowdStrike. What sets AuthMind apart from other TDR (Threat Detection and Response) solutions is its ability to detect identity-specific threats with full identity context for fast and actionable remediation.
How we are different
- Comprehensive Insights to Identity Activities and Broadest Coverage. AuthMind is the only solution that can provide visibility to the activity of all identities (human-to-machine, machine-to-machine), as they access assets, including on-prem, multi-cloud, and SaaS. AuthMind's technology is distinct as it guarantees consistent visibility, even when dealing with unmanaged identities and shadow assets. Unlike other solutions that can only secure Active Directory or specific identity security providers, AuthMind protects all identities and the entire identity fabric.
- Fast Incident Investigation with Full Attacker Context. AuthMind provides full context on identity threats, enabling threat teams to respond to identity attacks more swiftly than alternative solutions. AuthMind’s unique capability lies in its ability to aggregate multiple events with identity context and provide the full coordinates of the attacker, including identity details, hostname, and IP address. As a result, AuthMind significantly reduces the time needed to detect and resolve identity security incidents.
- Extends Beyond Your Identity Infrastructure. Most solutions can only detect and respond to threats targeting your identity infrastructure. AuthMind takes it further with a comprehensive ITDR and Identity Security Posture Management platform that can provide insights into blind spots outside the defined identity infrastructure, such as unmanaged assets, local accounts, unapproved SaaS usage, and detection of users who bypass an organization’s Zero Trust Network Access (ZTNA) tools.
-
Vote for this Nomination
(click the thumbs-up icon to cast your vote)

 (20 votes)
(20 votes)You need to be a registered member to vote for this nomination. Please register here.


