Best Zero Trust Security – Cloudbric
Photo Gallery
 |
 |
Best Zero Trust Security - Cloudbric

Additional Info
| Company | Cloudbric |
| Website | https://v2.cloudbric.com/ |
| Company size (employees) | 10 to 49 |
| Type of solution | Cloud/SaaS |
Overview
Cloudbric Remote Access Solution Industry Status
The COVID-19 pandemic has changed not only daily life but also corporate life around the world.
We find more and more companies turning to VPN (Virtual Private Network) solutions to enable their employees to work remotely. As more companies turn to VPN solutions, they are quickly starting to realize the limitations and issues of using traditional VPN solutions.
Although VPNs have been around since 1996 and have been used to enable users to connect securely, companies are realizing that there are quite a few limitations and issues that make it impossible for them to use VPNs.
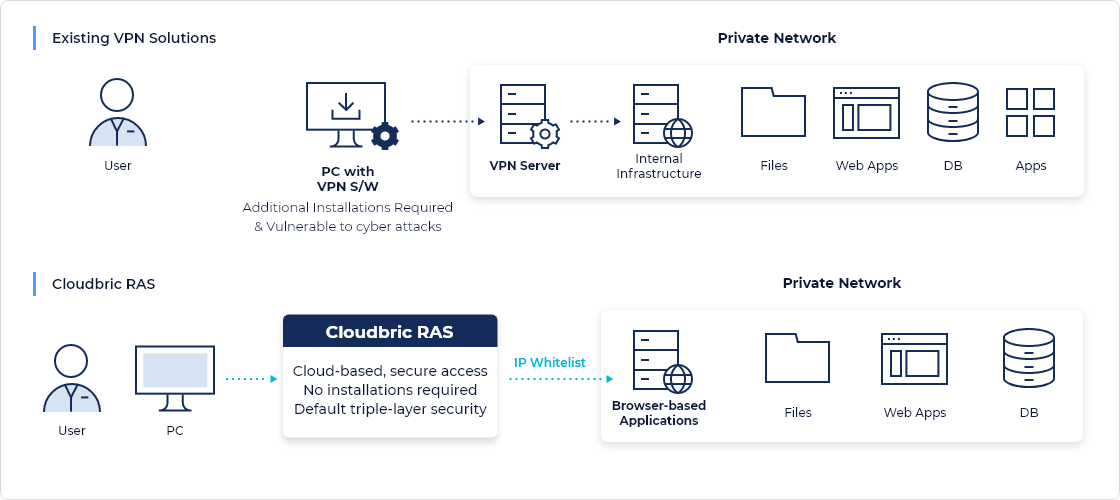
How Cloudbric Remote Access Solution Works
Cloudbric’s Remote Access Solution (RAS) uses End-to-End Encryption through Secure Proxy (EE2E) technology to securely connect users and corporate networks.
In addition, pre-authorized users can access the corporate network through two-factor authentication (2FA) anytime, anywhere. The implementation of Remote Access Solution can be performed instantly and easily as it requires zero installation of hardware or software. A simple change in network setting is all that is required.
Once implemented, a centralized dashboard enables the company to monitor and manage the solution. Only authenticated users will be able to access the corporate private network and data, regardless of device or access location.
RAS is applied on the domain of the web application (HTTP, HTTPS) within the organization. When users access the domain, they are first prompted with an authentication page, ensuring only authenticated users get access.
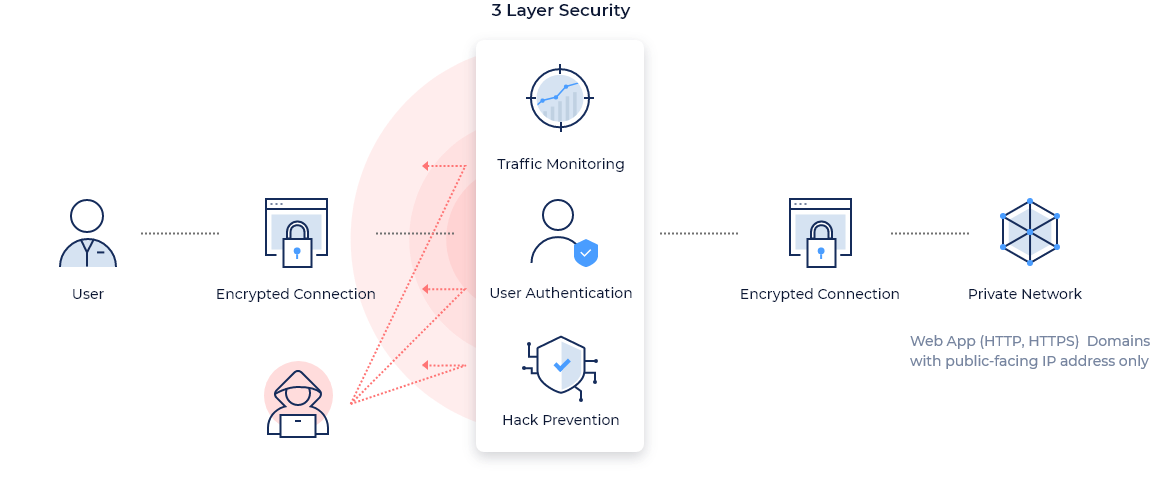
Cloudbric RAS is based on a zero-trust security model that thoroughly validates all access. It not only permits access of authorized users and devices, but also creates a remote access environment that is simple and quick to execute while providing thorough security based on 3 Layer Security which are authentication security, traffic monitoring, and hacking prevention.
How we are different
• Simple and cost-effective implementation
Users of the cloud-based Remote Access Solution can access the corporate private network anytime, anywhere through a web browser without any installing any hardware or software. Simply put, Remote Access Solution provides a cloud-based, secure channel for users to remotely access the data or applications on the web server within the Private Network. The solution is equipped with additional security features that block out hacking attempts and DDoS attacks—previously unavailable on traditional VPN solutions.
• Intuitive centralized management (can be managed with limited IT knowledge)
Cloudbric Remote Access Solution requires no additional installation of software or hardware on either the client side or the server side, unlike other remote working solutions such as VPNs. Every security layer of the Remote Access Solution is on the cloud, and thus requires no infrastructural resource from the user or network. Set-up is as easy as it can be—it’s a matter of changing DNS settings on the web server and providing user credentials. In minutes, users can access corporate web servers or other private networks remotely.
• Additional security layer (Basic DDoS protection, 2FA Authentication, Encryption, Traffic monitoring)
The core of Remote Access Solution is our 3-Layer Security consisting of Traffic Monitoring, User Authentication, and Hack Prevention. Traffic Monitoring detects and blocks common web-based threats including cross-site scripting (XSS), SQL injection, and even DDoS attacks. This provides a higher level of security for companies as Cloudbric monitors all traffic between the user and the webserver after the traffic passes through the preliminary security layer.
Additionally, all traffic that passes through the 3-Layer Security is encrypted automatically.



