Blade RiskManager
Photo Gallery
 |

|
Blade RiskManager


Additional Info
| Company | KDM Analytics |
| Website | http://www.kdmanalytics.com |
| Company size (employees) | 10 to 49 |
| Type of solution | Software |
Overview
KDM Analytics Blade RiskManager (BRM) is the only product to fully integrate and automate security assessment based on the NIST Risk Management Framework (RMF) Assessment workflow.
BRM utilizes a model-based system engineering approach to obtain information about the system under analysis. This approach shifts risk towards the early stages of project development. Once uploaded to BRM, the system information is analyzed for fit-for-purpose to ensure a high level of confidence in the final results. It is integrated with information from a comprehensive cybersecurity knowledge base based on more than a decade of research.
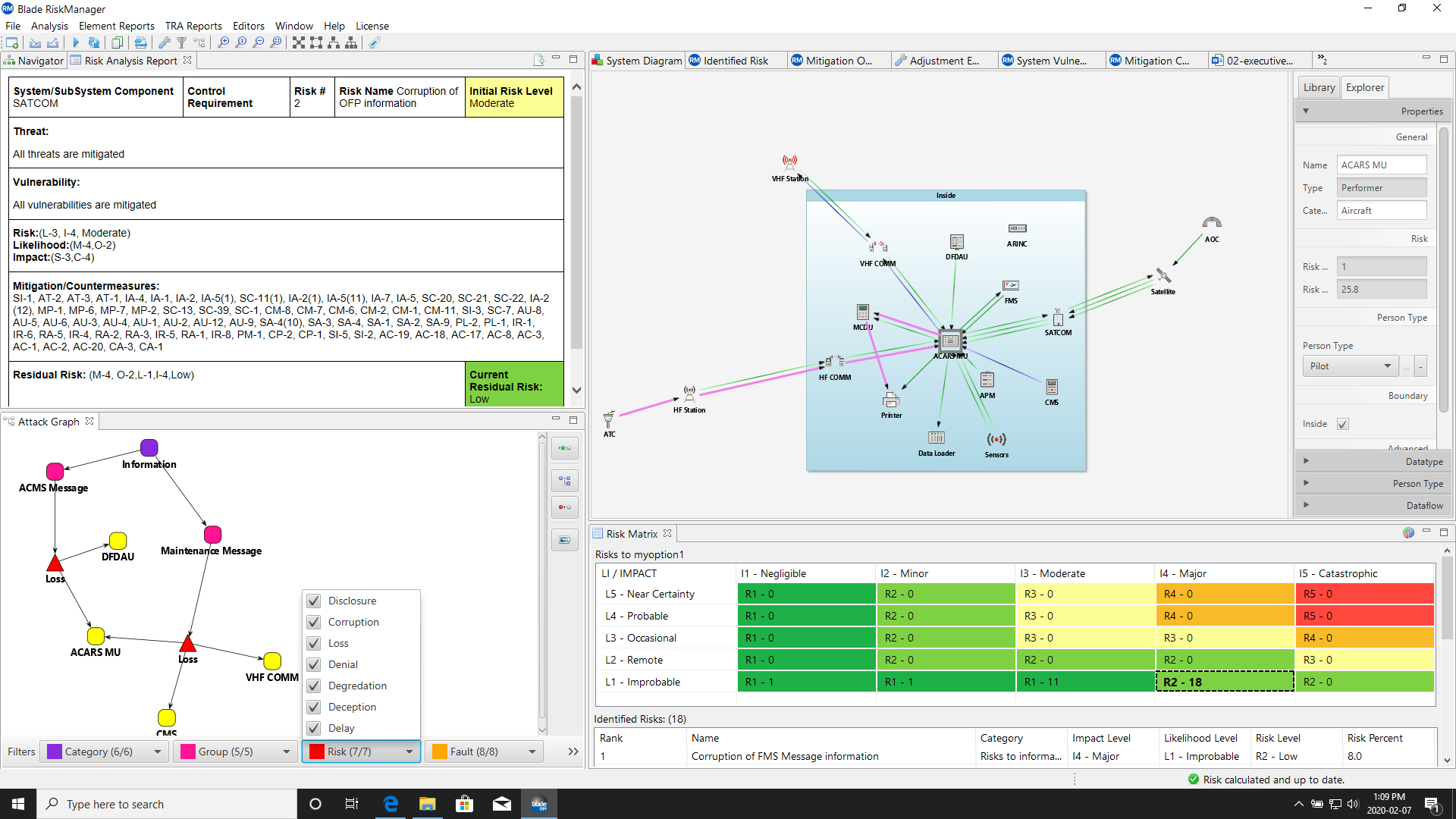
Blade RiskManager applies AI and reference rules to obtained system information to understand how the system can be attacked. It performs both direct and multi-stage attack analysis, automatically building the attack tree and identifying system exposures.
The product also automates the consideration of the means and opportunities of each attacker to mount the attack and produces a fully quantified, harmonized risk scale. This scale preserves the ordering of risk levels according to the NIST/DoD 5×5 risk matrix and produces a risk score followed by risk distribution across assets/targets, risks, threats and attacks. The resulting output is a prioritized list of risks, components, and vulnerabilities to focus on.
BRM also calculates, suggests, and automatically assigns Security Controls (SC) to each identified exposure/vulnerability. This ensures that only effective controls will be implemented: those that adequately mitigate the vulnerabilities and exposures.
BRM facilitates rapid, automated “what-if” scenarios to determine the most cost-effective solution, balancing budget and security. It generates Security Requirements with guidance, enabling engineers to implement the solution with security built in and security assessors to perform automated compliance risk.
Clients report that Blade RiskManager delivers greater value with minimal effort: 80% savings in resource and assessment time.
How we are different
AUTOMATES MODEL-BASED RISK ASSESSMENT (MBRA)
Blade RiskManager leverages system engineering models for the purposes of risk assessment (MBRA). Moving from document-centric to model-centric system engineering practices for describing systems enables BRM to be seamlessly integrated into the engineering design process, ensuring security is built-in and not bolted-on after the fact.
Through automation, clients using BRM typically achieve an 80% reduction in cost on first use while increasing robustness, completeness of the assessment, and confidence in the outcome.
AUTOMATES THE NIST RMF ASSESSMENT OF CYBER AND CYBER-PHYSICAL SYSTEMS
Blade RiskManager produces a comprehensive and systematic security assessment with a high level of confidence in the outcomes. The solution implements:
• Risk assessment based on NIST SP 800-37
• Security Controls based on NIST SP 800-53 and assessment reports in accordance with NIST SP 800-53A
• Risk levels are based on the NIST SP 800-30 risk assessment DOD Risk Management Guide and are computed based on the risk group’s likelihood and impact.
AUTOMATES, PRIORITIZES, AND QUANTIFIES RISK
Blade RiskManager is the only product to employ the most effective security assessment process that includes both top-down automated risk analysis followed by guided/targeted bottom-up vulnerability analysis. It answers the key stakeholder question: where should we focus mitigation efforts, resources and budget?
This is achieved through the following fully AUTOMATED capabilities:
• Threat modeling based on the operational and system architecture, followed by direct and multi-stage attack analysis and identification of exposures and operational impacts
• Graphical generation of system architecture, attack tree, and attack paths including risk analysis results (includes scoring)
• Assignment of Security Controls followed by risk computation: raw, mitigated, compliance, and residual risk
• Generation of risk assessment reports including security requirements and non-compliant risk assessment.



