Britive Cloud Access Management Platform – Maintain Zero Standing Privileges Across Your Multi-Cloud Environment
Photo Gallery
 |
 |
Britive Cloud Access Management Platform – Maintain Zero Standing Privileges Across Your Multi-Cloud Environment

Additional Info
| Company | Britive |
| Website | http://www.britive.com |
| Company size (employees) | 10 to 49 |
| Type of solution | Cloud/SaaS |
Overview
The cloud-native, 100% API based Britive Cloud Access Management Platform (no agents gateways or proxies) enables temporary Just-in-Time (JIT) privilege grants – the on-demand granting of elevated privileges for human and machine identities that are automatically revoked after a set period of time – which enables companies to minimize their attack surface through maintaining a state of Zero Standing Privileges (ZSP).
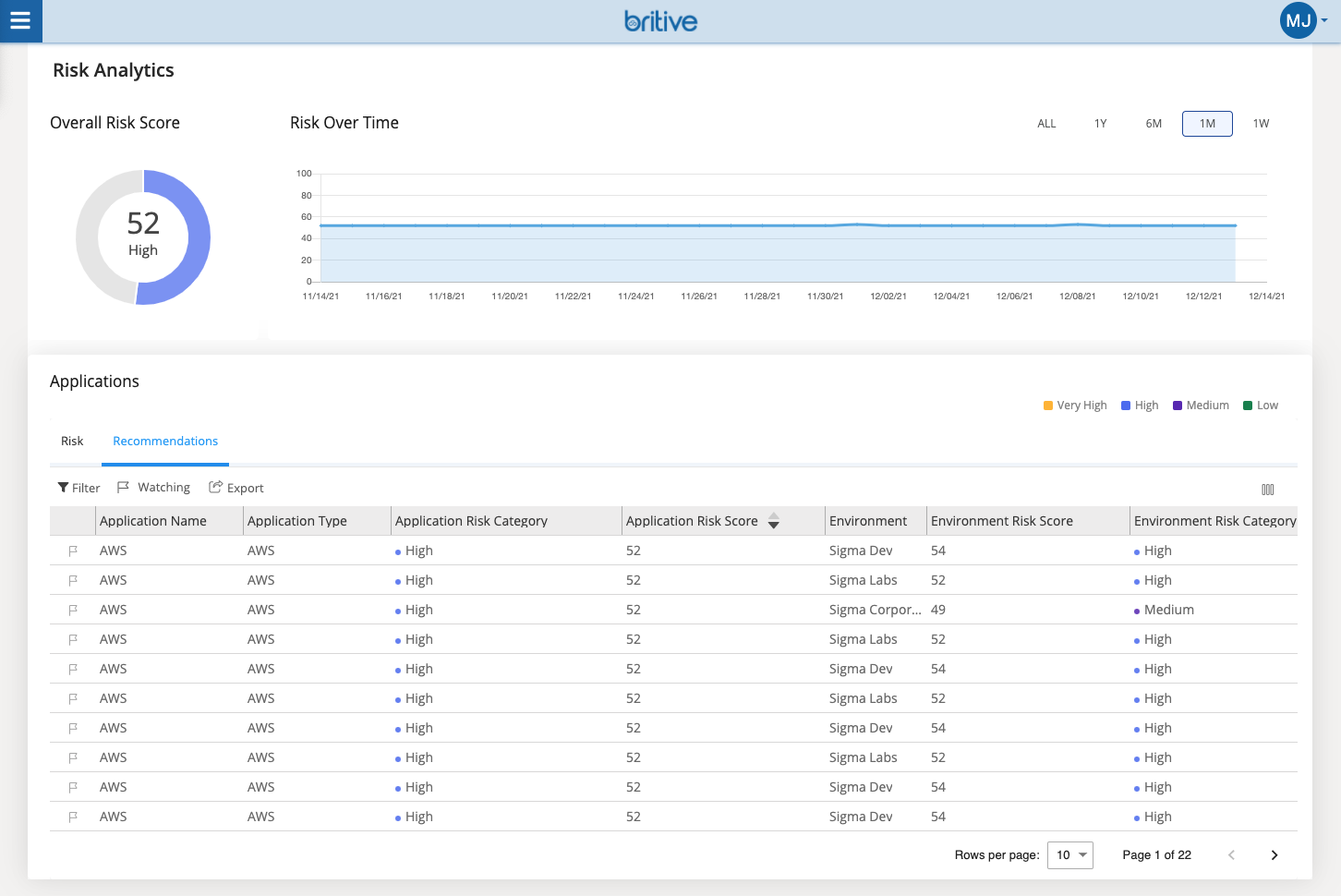
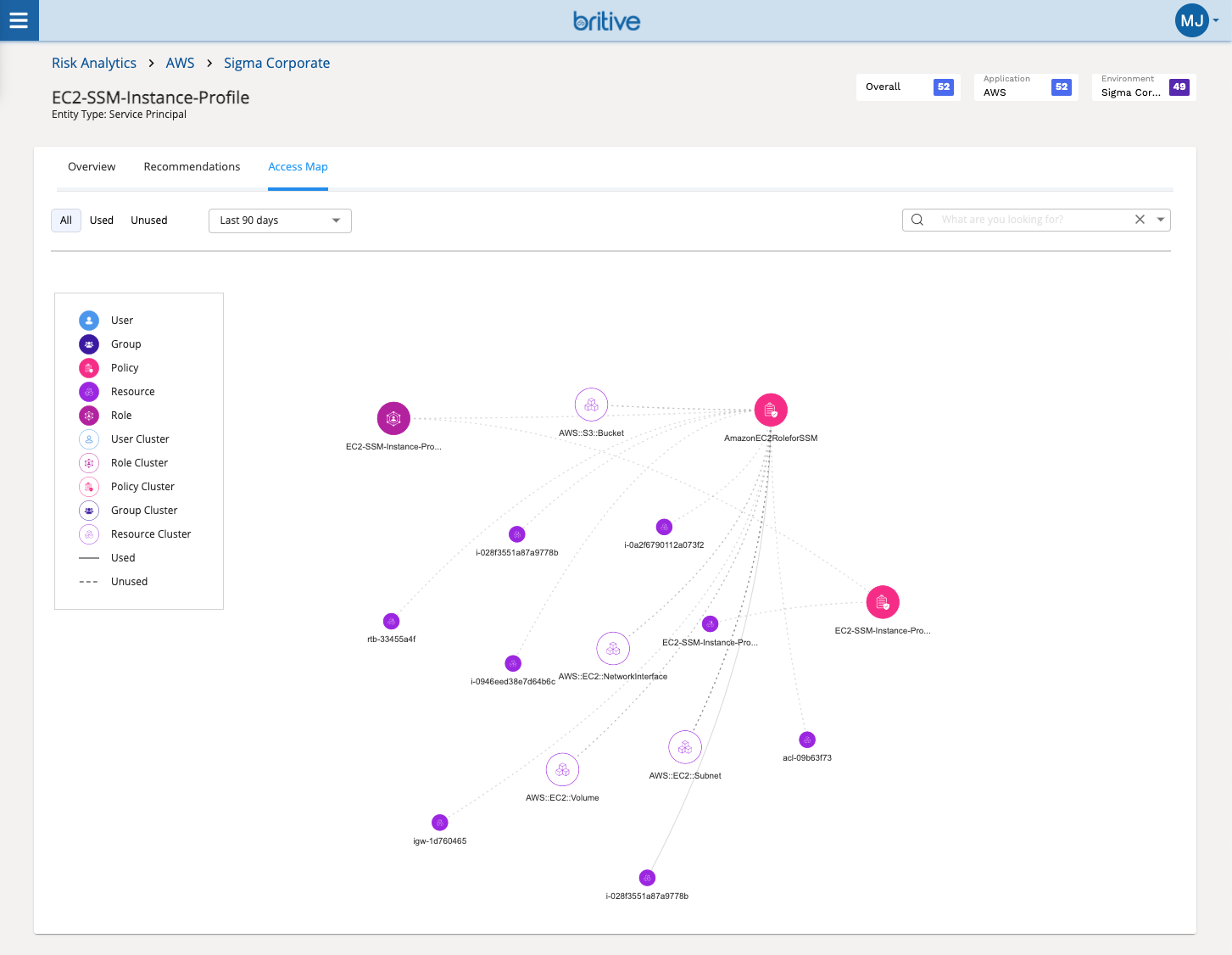
In addition, organizations can ensure that employees and contractors are granted the right level of privileges when onboarded, constantly right size those privileges over time, enforce access policies, and fully offboard users when they leave the organization. By providing visibility into all privileges cross-cloud and recommendations for right-sizing overprivileged entitlements, IT teams can maintain Least Privilege Access (LPA) throughout the cloud identity lifecycle, and minimize the potential blast radius of internal threat actors.
Third, Britive provides secrets management capabilities for non-human and service accounts, including the ability to grant ephemeral secrets to quickly spin up temporary services for testing & replace hard coded keys, as well as vaulting of static API keys, tokens, passwords, & service credentials.
How we are different
Unlike competing IAM/CIEM and PAM technologies:
1) Britive enables companies to maintain a state of Zero Standing Privileges (ZSP) by replacing high risk standing cloud access privileges with temporary Just-in-Time (JIT) privilege grants that are automatically revoked after a set period of time.
2) Britive provides a unified access model across multiple operation critical IaaS, SaaS, PaaS, and DaaS services. Competing solutions typically cover only IaaS or SaaS.
3) Britive integrates seamlessly with CI/CD automation software such as Jenkins and Terraform, empowering cloud application development teams to add access security to their development pipeline without introducing management complexity or creating a security speedbump – a common challenge for traditional IAM and PAM solutions, and a key impediment to building effective DevSecOps processes.



