Compass, SpyCloud
Photo Gallery
 |
Compass, SpyCloud

Additional Info
| Company | SpyCloud |
| Website | https://spycloud.com/ |
| Company size (employees) | 100 to 499 |
| Headquarters Region | North America |
| Type of solution | Cloud/SaaS |
Overview
According to SpyCloud’s 2023 Annual Ransomware Defense Report, 81% of organizations experienced a ransomware attack within the last year. It’s clear that despite an emphasis on ransomware defense, cybercriminals are developing more sophisticated tactics to target and exploit companies’ assets for personal gain. The threat landscape is expanding, and corporations need a modern approach to fighting cybercrime to protect critical infrastructures.
SpyCloud, the leader in operationalizing Cybercrime Analytics, revolutionizes ransomware protection by proactively defending users and organizations from cyberattacks. While investigating the cause of a security breach, SpyCloud leverages data from the darknet to expose vulnerabilities and automate the prevention of identity-based attacks such as ransomware.
According to the same report, one-third of the companies affected by ransomware had at least one infostealer infection before being attacked.
Infostealer malware enables data theft at a large scale while remaining hard to detect. Session cookies allow cybercriminals to mimic legitimate users and bypass standard security measures. Due to malware stolen data staying active for months or years, these attacks increase users’ vulnerability to repeated cyber incidents if not corrected or remediated immediately.
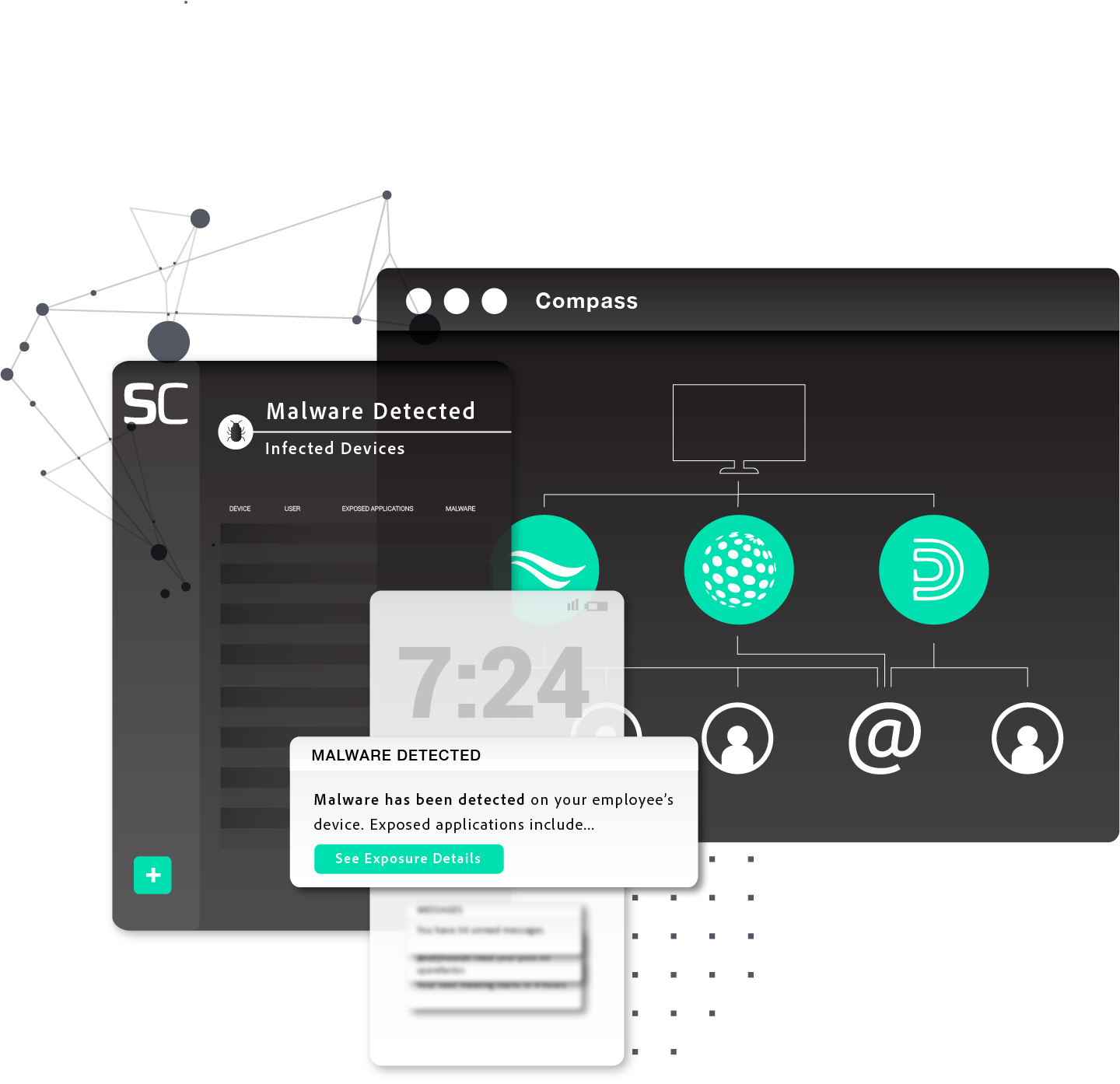
SpyCloud released its Compass solution to help enterprises detect and respond to the initial precursors of ransomware attacks. Powered by malware intelligence found in SpyCloud’s unmatched database of over 560 billion recaptured credentials, enterprises using Compass can provide definitive evidence that stolen data tied to an enterprise is in cybercriminals’ hands. This reduces organizations risk of ransomware and shortens incident response by identifying hard-to-detect malware infections often used as ransomware entry points.
Additionally, Compass is the only solution to enable Post-Infection Remediation (PIR), a more complete malware infection response that provides a framework of additional steps to existing incident response protocols. This approach negates opportunities for ransomware and other critical threats by resetting the application credentials and invalidating session cookies extracted by infostealer malware.
Key Capabilities / Features
Compass helps organizations proactively prevent ransomware by identifying definitive evidence of malware-infected devices, along with exposed users and applications that cybercriminals use to walk right into networks. As a result, organizations fill the gaps in their malware protection framework to detect and respond to high-priority threats.
In addition, Compass identifies infected devices and applications connected to an organization by monitoring malware records for the target domains and third-party subdomains an organization chooses. Once it identifies what has been exfiltrated by the infection, such as credentials and session cookies for critical business applications, security teams can understand the scope of the threat at-a-glance.
From there, Compass provides detailed information on each exposure to shortcut the investigation steps and enables teams to quickly implement Post-Infection Remediation (PIR). With insights such as malware type, user details, time, application and more, organizations can streamline the recovery process with PIR.
Other capabilities include:
Exposed Application View: view all third-party applications that were exposed by each infostealer, including shadow IT apps accessed with either personal or corporate email address
Managed Devices and BYOD: pinpoint the exact malware-infected managed or unmanaged device that was used to access corporate applications
High Fidelity Alerts: get definitive evidence that stolen data tied to your enterprise is in criminal hands, with alerts of new exposures
Interactive Graphs: visualize the scope of a potential threat, including infected devices, users, and applications with actionable details
Intuitive Portal: see thorough details of each infection, along with powerful visualizations that illuminate your remediation action plan
Stolen Cookies: view the count and name of stolen cookies associated with your monitored subdomain for the affected applications
How we are different
Industry Leading Research: In 2023, SpyCloud published its annual Ransomware Defense Report, analyzing trends related to ransomware and how businesses are responding to this threat. The report provided insight into common entry points for attacks, the most-used countermeasures, gaps in prevention and the financial impact of ransomware attacks. A key finding from the report indicated that 75% of security leaders are confident in their ransomware defenses, but 81% were affected by ransomware at least once in the past year, demonstrating the need for new approaches like PIR to help address the existing security gaps enabling these attacks.
Unmatched Intelligence: SpyCloud is known for curating, analyzing and operationalizing the industry’s largest repository of recaptured darknet data that fortifies ransomware prevention solutions. Powered by its unmatched repository of 560+ billion recaptured assets from the criminal underground, SpyCloud turns darknet data into actionable insights that quickly identify exact-match exposures, compromised passwords, stolen cookies and other identity data. SpyCloud’s scale of high-quality data is curated and enriched with a flexible and scalable API that enables action on evidence of compromise, further strengthening their unique approach to ransomware prevention.
Redefining Remediation: SpyCloud has pioneered a new remediation strategy, Post-Infection Remediation (PIR) to help organizations gain deep visibility into malware-exposed workforce applications, determine the identity of threat actors, and provide actionable steps to prevent future attacks like ransomware. This new approach better enables security teams to invalidate active sessions, reset credentials, and review users’ activity and access within each application.



