Context™ AI-Driven All-Source Threat Intelligence Platform
Photo Gallery
 |
 |
Context™ AI-Driven All-Source Threat Intelligence Platform

Additional Info
| Company | Resecurity, Inc. |
| Website | resecurity.com |
| Company size (employees) | 50 to 99 |
| Headquarters Region | North America |
| Type of solution | Cloud/SaaS |
Overview
Resecurity Context™ is a Cyber Threat Intelligence (CTI) Platform enabling enterprises and government agencies to collect actionable intelligence from multiple sources by different criteria and to accelerate analysis, prevention and investigation workflow required for strategic and timely decision-making.
Resecurity Context™ is provided in form of dedicated secure portal (delivered as a Platform-as-a-Service or “PaaS”) with capability to produce automated intelligence feeds through API, STIX&TAXII protocol and/or other exportable formats (JSON, XML, TXT, etc.) for integration with third-party systems. The production of finished intelligence including but not limited to IOCs, TTPs, threat artifacts is organized through TAXII server.
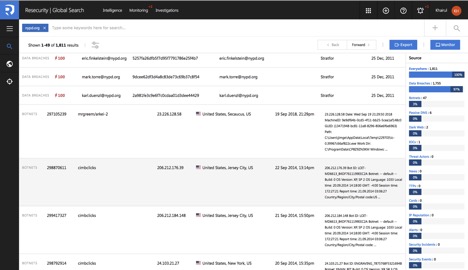
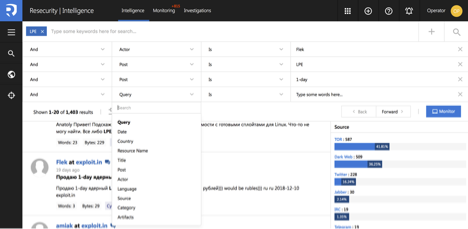
Resecurity Context™ supports flexible set of search filters in order to increase targeting, accuracy and relevancy of the search results. Search filters can be configured by operator through UI or API interface. The operator may define complex search filters and rules in specific module or across the whole platform.
Supported “Search Filters” and “Criteria” (over 50) for “Global Search” (will be executed across all modules of the platform). The same filters may be applied for monitoring tasks to make monitoring accurate.
Resecurity Context™ has a robust monitoring module allowing to configure multiple long-term monitoring tasks based on different criteria in order to optimize time-consuming and manual operations. The operator may quickly switch from search operations to automated long-term monitoring by creating a monitoring task based on the provided search query or using interactive wizard. Monitoring module provides real-time and near real-time cyber threat intelligence reporting capabilities depending on
How we are different
Context™ is globally recognized by government agencies and military to for providing a solution for forward hunting intelligence operation platform.
Second, Context™ data source does not use commodity or commercially available data. Over 48K sources of data is curated by engineers which is ETLed into Resecurity's Data Lake, which powers rest of Resecurity's solution.
Third, recognized by law enforcement and investigators around the world as having the first day operational capabilities. This is important because the operator does not have a learning curve on how to move around the system after initial knowledge transfer.



