CyberArk Identity
Photo Gallery
 |
 |
CyberArk Identity

Additional Info
| Company | CyberArk |
| Website | cyberark.com |
| Company size (employees) | 1,000 to 4,999 |
| Type of solution | Software |
Overview
CyberArk Identity is a leading IAM solution that enables organizations to securely extend all their business applications and IT services to remote workers and on-the-go users while delivering an exceptional end-user experience. CyberArk Identity includes Workforce Identity and Customer Identity and is differentiated by its AI-powered, adaptive authentication capabilities.
The solution includes:
CyberArk Identity Single Sign-On: gives workers convenient one-click access to all their enterprise applications using a single set of credentials.
CyberArk Identity Adaptive Multi-Factor Authentication: helps businesses avoid data loss and other risks posed by compromised or stolen credentials.
CyberArk Identity Lifecycle Management: lets administrators efficiently onboard and offboard users, and manage their access privileges throughout their course of employment.
CyberArk Identity App Gateway: lets users securely access traditional applications hosted in corporate data centers using the same credentials and authentication methods they use to access cloud apps.
CyberArk Identity Directory Services: lets organizations centrally manage enterprise IT directories at scale.
CyberArk Identity User Behavior Analytics: uses AI and Machine Learning to collect, analyze, and visualize user behavior and threat data in real-time.
According to The Forrester Wave™: Identity As A Service For Enterprise, CyberArk Workforce Identity offers well-designed authentication with endpoint MFA, passwordless options, strong user self-service capabilities, and the ability to sequence authentication factors in different ways. CyberArk was also named as the only Visionary in the Gartner Magic Quadrant for Access Management based on recent innovations.
In the past year, CyberArk has introduced product innovation across its Identity offerings, including the launch of CyberArk Identity Secure Web Sessions, which enables organizations to record and protect user web application sessions, while continuously authenticating users during sensitive sessions. CyberArk also announced Lifecycle Management for Privileged Users, which allows customers to further expedite employee onboarding, including those with privileged access, and meet audit and compliance mandates more efficiently.
How we are different
CyberArk Identity is differentiated from other IAM solutions based on its security-first approach. Where competitors focus primarily on operational benefits, CyberArk leads with security to help customers defend against attacks and enable their digital businesses. CyberArk Identity enable access across any device, anywhere at just the right time:
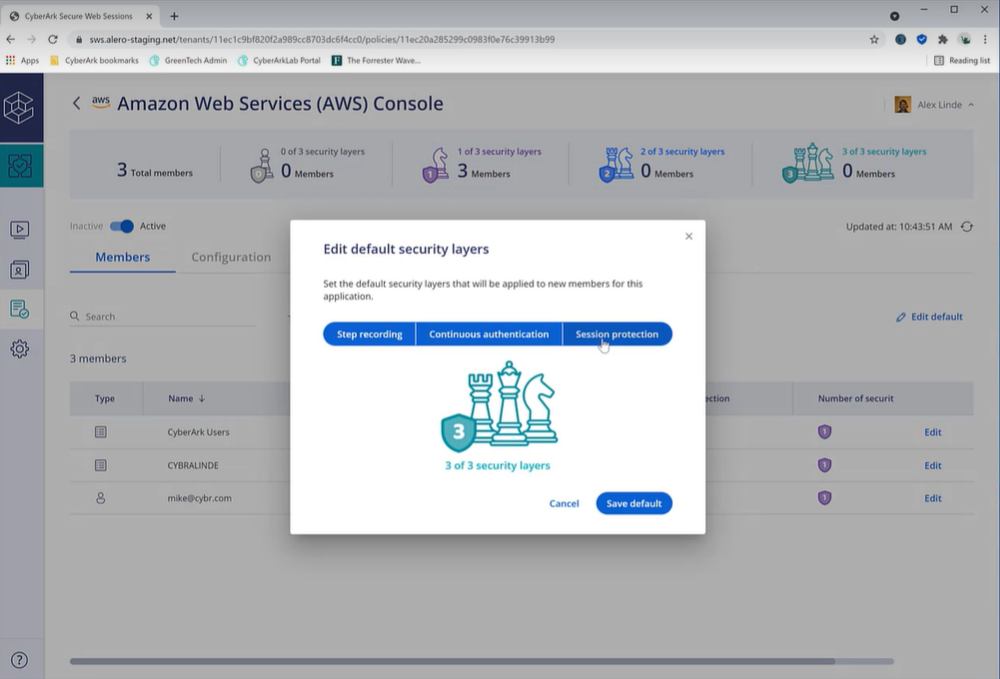
-CyberArk Secure Web Sessions - CyberArk Identity Secure Web Sessions helps security and compliance teams unmask and address insider threats and errors quickly by adding extra layers of security to web application sessions. Teams can record and search every click and data change made within a protected app while maintaining a frictionless user experience, implement continuous monitoring and re-authentication, and restrict data exfiltration actions, such as copying of data and file downloads.
-CyberArk Identity Adaptive Multi-Factor Authentication - CyberArk Identity Adaptive Multi-Factor Authentication (MFA) helps businesses avoid data loss and other risks posed by compromised or stolen credentials. The solution supports a variety of authentication mechanisms, including passwordless factors, and protects a range of enterprise identities and resources, such as applications, infrastructure, and endpoints. Unlike traditional MFA solutions, CyberArk Identity Adaptive MFA uses AI-powered behavioral analytics and contextual information to determine which authentication factors to apply to a particular user in a specific situation, improving end-user satisfaction and productivity.
-CyberArk Identity User Behavior Analytics - CyberArk Identity User Behavior Analytics uses AI and Machine Learning to collect, analyze, and visualize user behavior and threat data in real-time. The solution includes interactive dashboards to help administrators easily assess risk, reporting tools to help administrators investigate security incidents and support audits, and real-time alerts to notify administrators of suspicious activity. It also provides webhooks to feed alerts to third-party tools like ServiceNow.



