E8 Security Fusion Platform 2.2
Photo Gallery
 |
 |
E8 Security Fusion Platform 2.2

Additional Info
| Company | E8 Security |
| Website | http://www.e8security.com |
| Company size (employees) | 10 to 49 |
| Type of solution | Software |
Overview
E8 Security’s Fusion Platform is designed around the Security Operations Center (SOC). Relying on rule-based and signature-based threat detection is no longer sufficient to stay ahead of hackers, especially when they’re already inside your organization – today’s heavy influx of data breaches is a symptom of this issue. Not to mention, sticking to rule-based detection requires time-consuming maintenance, a commodity resource security analysts don’t have much of in their mission to thwart hackers.
The E8 Security Fusion Platform uses completely unstructured (no rules or signatures), self-learning detection to better detect the unknown threats lurking in an enterprise network. This does not require enterprises to replace current infrastructure; the platform integrates with SIEM architecture to enhance threat detection efficiency. Once deployed, the Fusion Platform intakes data from either the SIEM or directly from the data source and runs analytics on it. This better ensures that the unknown threats lurking in the network can be identified and acted on, even before threat intel feeds are updated.
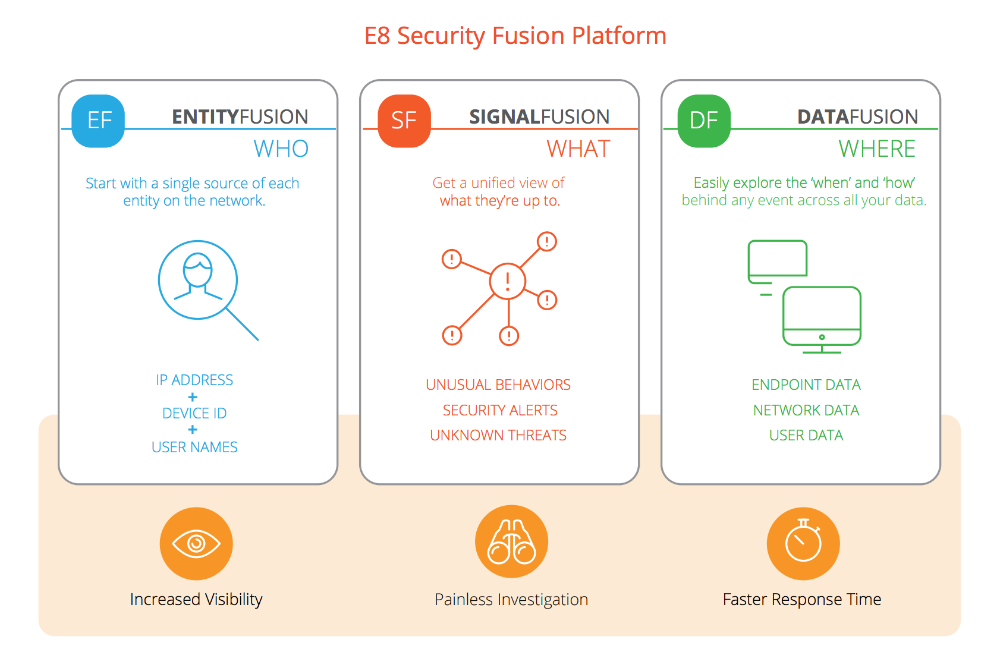
The Fusion Platform ties all behaviors back the user and device, regardless of IP address, so the analyst has immediate context to take swift action depending on the threat level of the alert. SOC analysts spend up to 20 minutes for each alert trying to figure our what device had a certain IP address at a specific time, and then which user or group owns that device. With the E8 Security Fusion Platform, this time is given back to the analyst so they can strategically address the threat and protect the network.
How we are different
o Insider threats can be difficult to pinpoint because legitimate credentials and access rights are often used. The E8 Fusion Platform detects the subtleties of suspicious behavior inside an organization when policies and signatures cannot —including credential sharing, privileged access abuse, and lateral movement — by tying each behavior back to the device and user, regardless of changing IP addresses.
o The E8 Security Fusion Platform is not just focused on access behaviors – it looks at the entire sequence of suspicious activity within the organization to provide optimal data visibility. It gives the full image of insider threat behavior, including insight into what is going on in the network and on endpoints, so SOC analysts can act more quickly and efficiently.
o The Fusion Platform does not require customers to replace existing infrastructure and investments. It uses customers’ existing technology stacks to gather data, making it quick to deploy and easy to maintain. It can integrate smoothly with SIEMs and other infrastructure to enhance security defenses, augment capabilities and tackle large-scale data ingestion from a holistic vantage point, while saving enterprises time and money. With the E8 Fusion Platform, enterprises don’t need another policy engine, as they likely already have a firewall, IPS and endpoint protection.



