Fudo PAM
Photo Gallery
 |
 |
Fudo PAM

Additional Info
| Company | Fudo Security |
| Website | http://www.fudosecurity.com |
| Company size (employees) | 50 to 99 |
| Type of solution | Software |
Overview
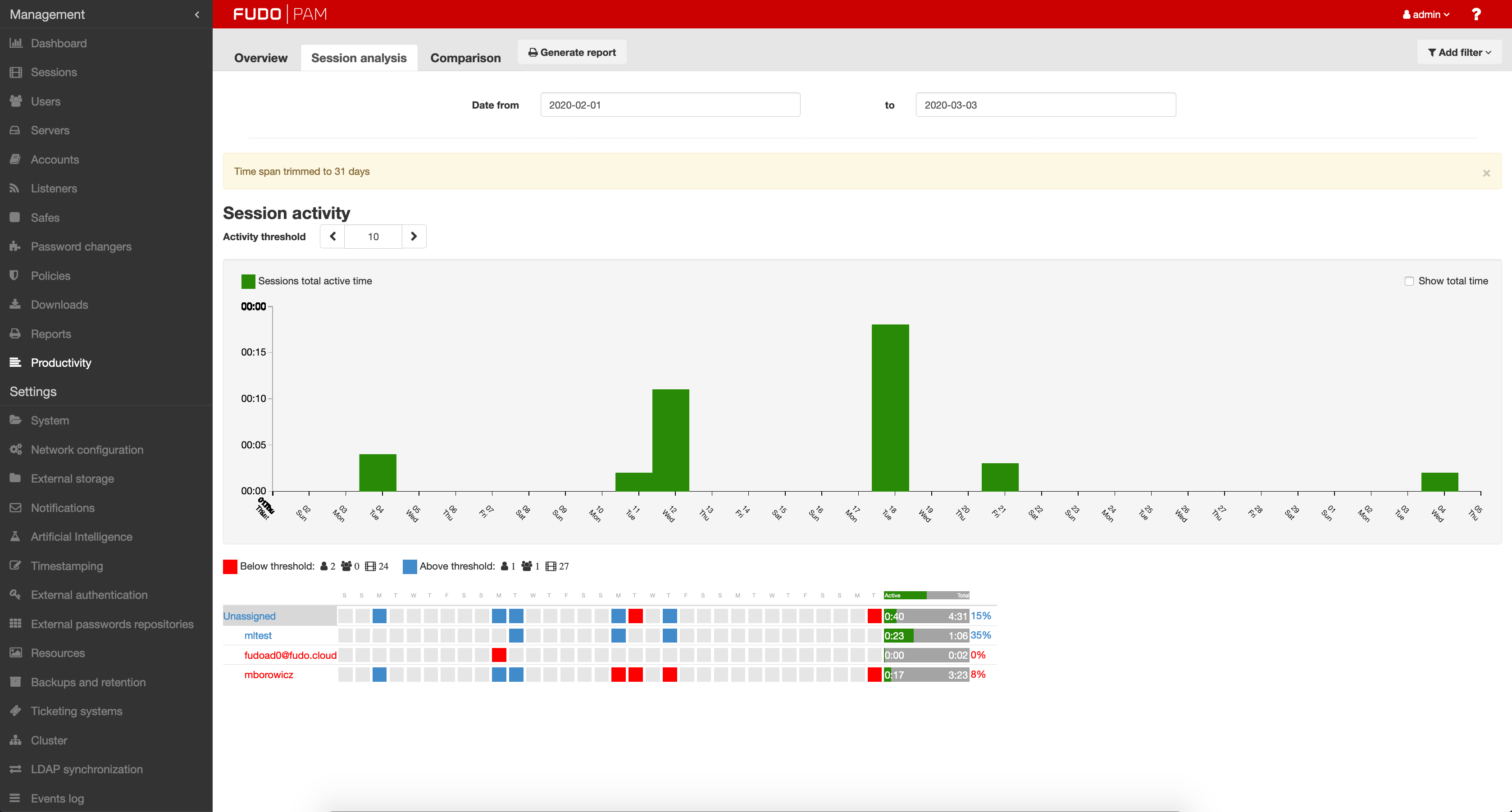
Fudo’s AI-powered behavioral analysis makes sure there is no identity theft happening from inside or outside the company. Based on advanced biometrics tracking, Fudo can detect even the slightest change in user behavior in SSH and RDP connections. Sessions are analyzed and scored in real-time to help you prevent access rights misuse and prioritize the review backlog.
All ongoing sessions are being monitored, and, whenever something suspicious is taking place, Fudo PAM sends alerts to the designated security officers. Based on AI-backed mouse moves, Fudo PAM’s biometric analysis knows in seconds that the session was taken over by an unauthorized user.
Fudo enables secure remote access to the company’s IT resources. It covers all possible scenarios: from 3rd party contractors accessing your critical infrastructure to thousands of employees accessing their office workstations from home. Remote users can access monitored systems through a proxy or by using a convenient Web Access Gateway.
One of Fudo’s key strengths is the ability to separate user access credentials from server or service access procedures. With this you can easily augment your login scheme with a second factor, like Google Authenticator, SMS, Duo or any kind of software or hardware token that can be checked using industry-standard RADIUS protocol. In addition, Fudo’s ability to integrate with Active Directory/LDAP-based user base, allows for sophisticated authentication and authorization scenarios out-of-the box, without any need for additional server or client software being installed. And by employing Secret Manager module, SOC teams can gain a level of control never achievable with any other tools.
How we are different
Fudo Secure Remote Access is the simplest way for remote users to access servers, applications, and systems.
In addition to offering the world's leading session recording mechanism, Fudo PAM also detects malicious employees or hackers using stolen credentials.
This award-winning solution is deployable in a matter of days and does not require any additional agents to be installed on the server.



