Graylog Security
Photo Gallery
 |
 |
Graylog Security

Additional Info
| Company | Graylog |
| Website | https://graylog.org/ |
| Company size (employees) | 100 to 499 |
| Headquarters Region | North America |
| Type of solution | Software |
Overview
Graylog Security is the ultimate solution for businesses seeking operational efficiency, real ROI, and unmatched scalability. Our platform is designed for adaptability, supporting businesses of all sizes, and is ideal for modern hybrid cloud operations. With Graylog Security, practitioners can enjoy faster time-to-value while controlling costs, eliminating risks, and reducing operational complexity.
Graylog elevates cybersecurity through its comprehensive SIEM, Centralized Log Management, and API Security solutions. The company’s unique blend of AI/ML, advanced analytics, and intuitive design makes cybersecurity smarter, not harder. Unlike competitors’ complex, costly setups, Graylog offers power and affordability, simplifying the IT and security challenges. Founded in 2009, Graylog solutions are deployed in over 50,000 installations across 180 countries.
Real ROI with operational efficiency
Enterprise Strategy Group (ESG) survey of Graylog Security customers revealed that compared to previously deployed SIEM solutions, Graylog Security provided faster time to value and reduced cost, risk, and operational complexity. ESG predicts that Graylog Security can be operated by teams up to 20% smaller than some alternative SIEMs require. In addition, Operational efficiency from the Graylog platform can lead to an expected annual ROI of 158% to 263%.
Unmatched Efficiency and Scalability
Graylog’s architecture is designed for adaptability, supporting businesses of all sizes. The system’s efficiency reduces operational costs and enhances performance, ensuring that security teams can focus on strategic initiatives rather than being bogged down by data management and scaling challenges. By optimizing how data is stored and accessed, Graylog ensures that critical information is readily available for investigation and analysis while balancing performance, risk and cost.
Key Capabilities / Features
Graylog Security strengthens security posture immediately by:
Illuminating genuine threat activity
Expediting investigations by connecting relevant data across multiple sources without skyrocketing costs
Equipping practitioners with operational insights to enhance your risk mitigation strategies
According to an economic evaluation whitepaper by Enterprise Strategy Group, Graylog enables “teams to provide improved detection, investigation, and support for their customers much faster than if they were to try to build these capabilities themselves on other SIEM platforms.” Graylog helps organizations accelerate their security maturity with intuitive analyst workflows and dashboards that highlight risk for immediate action.
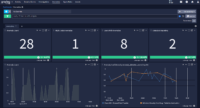
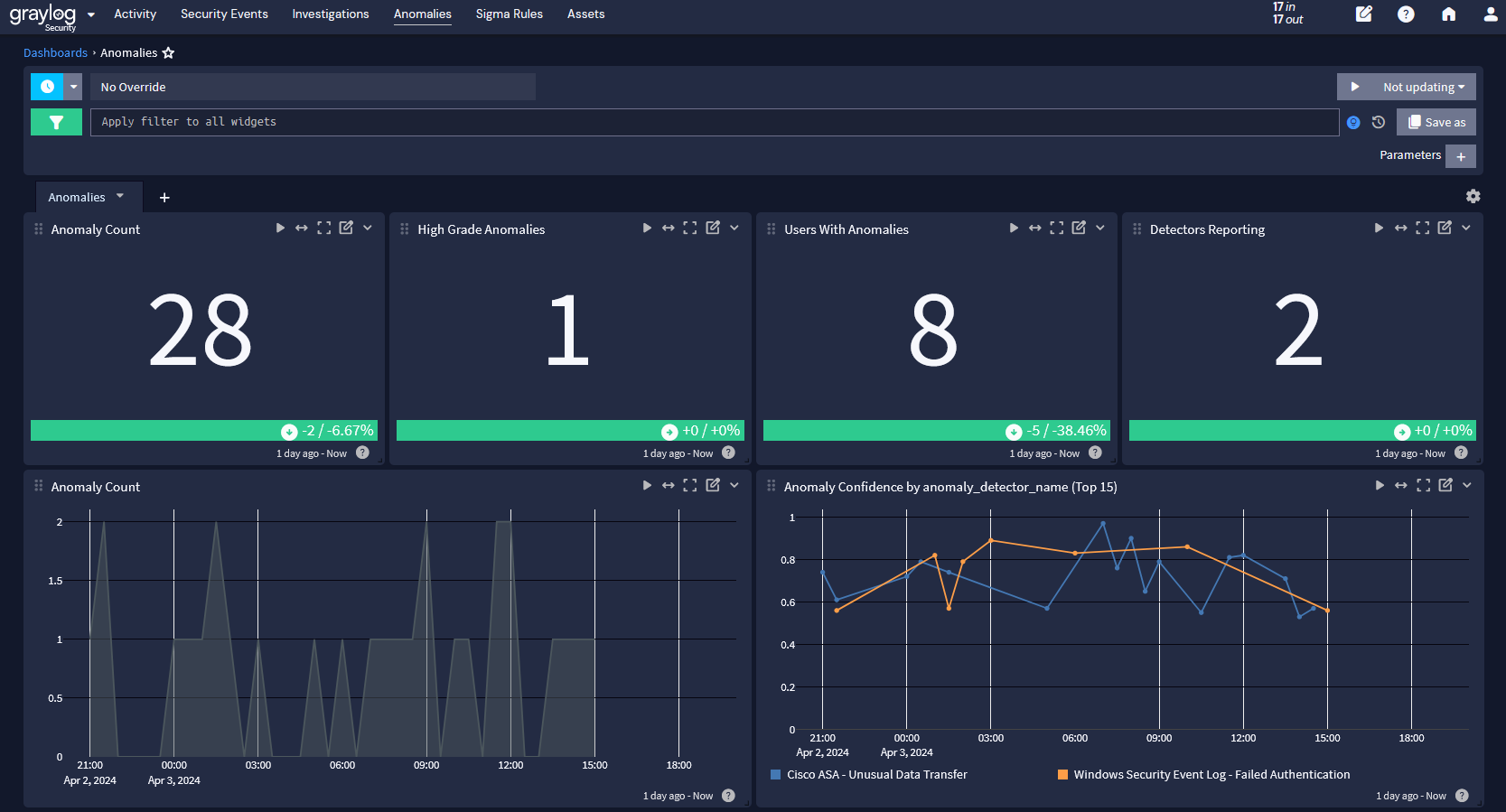
AI/ML-enhanced Anomaly Detection
Graylog’s preconfigured (AI/ML) detectors, Risk Scoring feature, and customizable dashboards proactively reduce risk and alert fatigue, all in an easy-to-use solution that requires no specialized training.
Faster queries
One of the most significant benefits reported by customers comparing alternative SIEMs in an ESG study was “Graylog’s ability to perform parsing and searches across much larger data sets in less time and with less effort.”
Data Enrichment
Graylog facilitates the enrichment of datasets with the results from other sources such as WHOIS, IP Geolocation, threat intel, and various data sets.
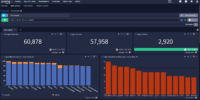
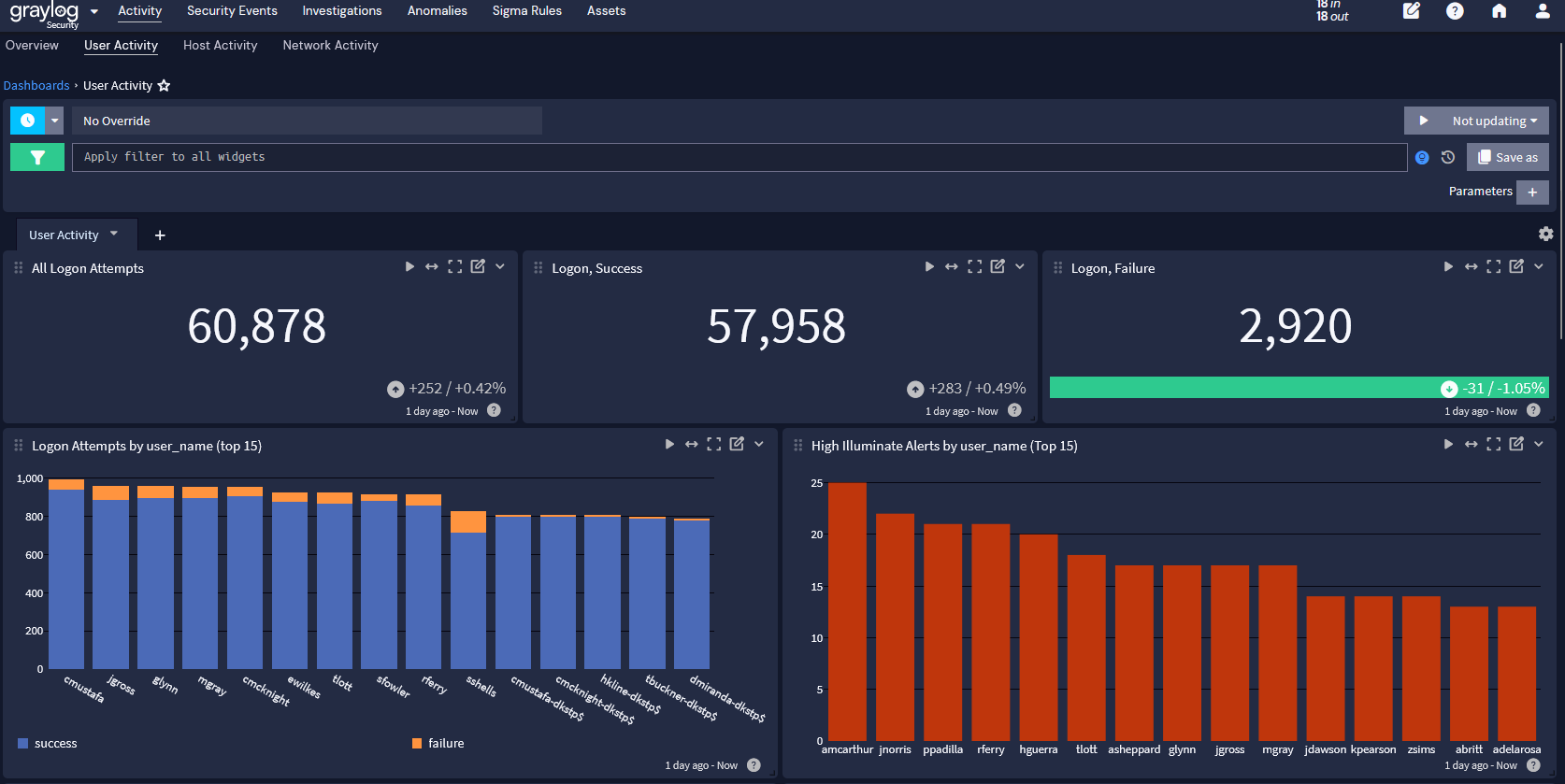
Reduced alert fatigue
With the ability to customize alert criteria to ensure that only the critical alerts require immediate attention, Graylog helps teams focus on high risk and actionable insights. Teams can receive vital alerts immediately via email, Slack, text, and other methods.
Compliance
Graylog security easily creates meaningful reports that help demonstrate compliance.
How we are different
• Simplifying life in the SOC
Illuminate is a Graylog-provided collection of content consisting of pipelines, parsing rules, lookup tables, dashboards and more. This standardization allows for the creation of universal dashboards, facilitating operations across different data sources seamlessly, (i.e. irrespective of the specific firewall). A single, overarching rule can be used across similar events, like "Windows Logon Brute Force" and "Linux Logon Brute Force.” By standardizing how log data is enriched and normalized searches become quicker and easier.
Recently, Graylog has formed an exclusive partnership to incorporate threat intelligence from SOC Prime into its offering. This integration introduces curated content packs that are designed to enhance threat detection and response times. Previously this level of content sophistication was only available to more advanced SOCs. Graylog is committed to continuously providing valuable, accessible content to its users, democratizing sophisticated security intelligence for broader use.
• Sophisticated queries for TDIR
Graylog’s reputation for faster-than-lightning queries has established its leadership for Threat Detection and Incident Response use cases, especially for organizations with limited resources. Searching large data sets quickly helps organizations detect and resolve cybersecurity, network, infrastructure, and application issues quicker, increasing operational effectiveness, improving service quality, and reducing risk to organizations. With Graylog, practitioners can build sophisticated queries in minutes, searching terabytes of data in milliseconds so that you get the answers you need at warp speed.
• Single platform for hybrid needs
Security teams must adapt to changing business priorities resulting in hybrid cloud operations. Unfortunately, the tools to support legacy on-premise and cloud are never quite the same, and teams find themselves overwhelmed by too many tools. Enterprise Strategy Group validated that Graylog Security offers the same feature set and lockstep development between on-prem (self-managed) and cloud versions, making it an excellent choice for modern hybrid cloud operations.



