Gurucul Open XDR Delivers the Most Comprehensive Analytics for Automated Detection and Targeted Threat Response
Photo Gallery
 |
Gurucul Open XDR Delivers the Most Comprehensive Analytics for Automated Detection and Targeted Threat Response

Additional Info
| Company | Gurucul |
| Website | https://gurucul.com/ |
| Company size (employees) | 100 to 499 |
| Headquarters Region | North America |
| Type of solution | Software |
Overview
As organizations evolve their networks and infrastructure based on digital transformation objectives, it leads to an expanding attack surface with numerous security gaps. The efficiency and sophistication of phishing and social engineering attacks makes it virtually inevitable that an initial compromise occurs. In addition, threat actors are piecing together existing and new malware strains with different techniques to better evade current detection methods that are often siloed.
EDR, NDR and traditional SIEM solutions struggle to reduce mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) – further extending attacker dwell time within an organization to several months. And traditional XDR solutions, which claim some form of analytics, are primarily focused on analyzing specific sets of telemetry. This includes endpoint, log, or network data, with underdeveloped capabilities across other necessary analytics. Worse, their claims of machine learning and artificial intelligence are just unadaptable, rule-based AIs that can be broken down as fixed conditional patterns, leaving them ineffective at adapting to and finding new and emerging attacks and variants.
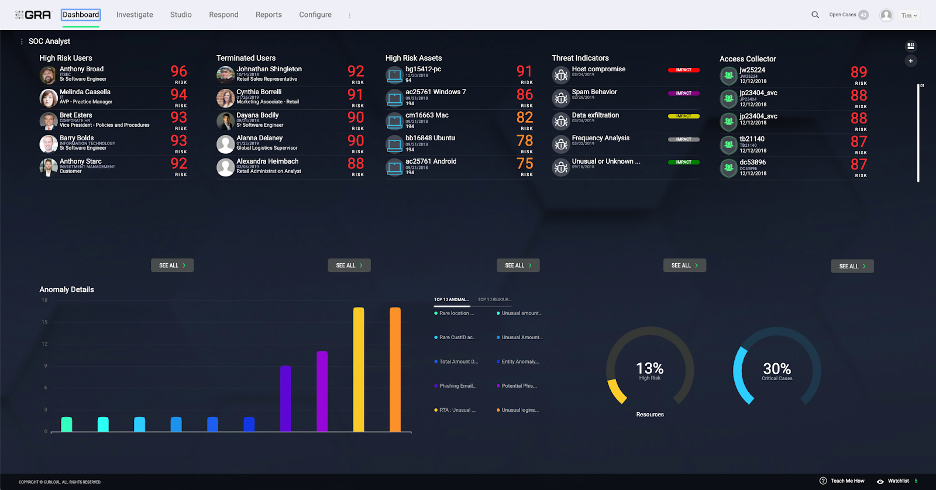
Gurucul Open XDR is a cloud-native, analytics-driven XDR product that is offered as part of the overall Gurucul security operations platform for augmenting threat detection, prioritization, triage, and response. It collects a wide variety of telemetry, correlation, and analysis of indicators of compromise for high-fidelity attack detection, prioritized investigation, and risk-driven response. With Gurucul Open XDR, SOC teams of varying skills and size gain the necessary visibility, context, and automation needed to identify attack campaigns in real-time and prevent damage within minutes and hours, not days, weeks or months.
With Gurucul’s data ingestion and correlation capabilities, the most comprehensive set of advanced analytics, and an industry-leading number of trained ML models, all consolidated into a single console, organizations can significantly accelerate and drastically improve their teams’ ability to prevent successful breaches early in the kill chain.
How we are different
Gurucul Risk Analytics (GRA) is the core of Gurucul’s Open XDR solution. It delivers a comprehensive set of correlation rules and ML models OOTB (more than 2,500), which are pre-configured/pre-packaged to use different vendor solutions logs including OS platforms, cloud platforms, firewalls, VPN, etc.
There is an intuitive web UI to create custom correlation rules and ML models without requiring involvement from data science/development teams (no black box). Gurucul Open XDR also provides OOTB mapping and alignment of threat indicators / IOCs with standard security frameworks including MITRE, NIST Security Framework, Cyber kill chain, and the ability to create / map IOCs to custom categories.
Reduces false positives: With its unique approach, Gurucul's Open XDR minimizes the number of false positives, enabling security teams to focus on real threats and improve incident response.



